c write a program that keeps track for presenters for colleges in usa the program should use a structure to store the data about a presenter struct presenter string name string presentationtopic string address string telephone
Answers
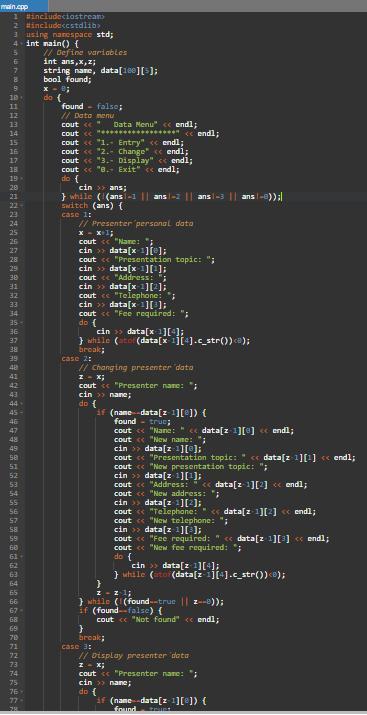
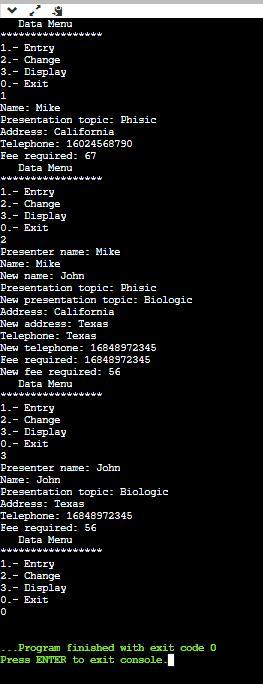
C++ program to register data from presenters for colleges, using a menu interface and array-type data structure. Below is an image of the code.
C++ code#include<iostream>
#include<cstdlib>
using namespace std;
int main() {
// Define variablesint ans,x,z;
string name, data[100][5];
bool found;
x = 0;
do {
found = false;
// Data menucout << " Data Menu" << endl;
cout << "*****************" << endl;
cout << "1.- Entry" << endl;
cout << "2.- Change" << endl;
cout << "3.- Display" << endl;
cout << "0.- Exit" << endl;
do {
cin >> ans;
} while (!(ans!=1 || ans!=2 || ans!=3 || ans!=0));
switch (ans) {
case 1:
// Presenter 'personal datax = x+1;
cout << "Name: ";
cin >> data[x-1][0];
cout << "Presentation topic: ";
cin >> data[x-1][1];
cout << "Address: ";
cin >> data[x-1][2];
cout << "Telephone: ";
cin >> data[x-1][3];
cout << "Fee required: ";
do {
cin >> data[x-1][4];
} while (atof(data[x-1][4].c_str())<0);
break;
case 2:
// Changing presenter' dataz = x;
cout << "Presenter name: ";
cin >> name;
do {
if (name==data[z-1][0]) {
found = true;
cout << "Name: " << data[z-1][0] << endl;
cout << "New name: ";
cin >> data[z-1][0];
cout << "Presentation topic: " << data[z-1][1] << endl;
cout << "New presentation topic: ";
cin >> data[z-1][1];
cout << "Address: " << data[z-1][2] << endl;
cout << "New address: ";
cin >> data[z-1][2];
cout << "Telephone: " << data[z-1][2] << endl;
cout << "New telephone: ";
cin >> data[z-1][3];
cout << "Fee required: " << data[z-1][3] << endl;
cout << "New fee required: ";
do {
cin >> data[z-1][4];
} while (atof(data[z-1][4].c_str())<0);
}
z = z-1;
} while (!(found==true || z==0));
if (found==false) {
cout << "Not found" << endl;
}
break;
case 3:
// Display presenter' dataz = x;
cout << "Presenter name: ";
cin >> name;
do {
if (name==data[z-1][0]) {
found = true;
cout << "Name: " << data[z-1][0] << endl;
cout << "Presentation topic: " << data[z-1][1] << endl;
cout << "Address: " << data[z-1][2] << endl;
cout << "Telephone: " << data[z-1][3] << endl;
cout << "Fee required: " << data[z-1][4] << endl;
}
z = z-1;
} while (!(found==true || z==0));
if (found==false) {
cout << "Not found" << endl;
}
break;
}
} while (!(ans==0 || x>100));
return 0;
}
To learn more about array data structure in C++ see: https://brainly.com/question/15088893
#SPJ4
Related Questions
Migrating a traditional database design to the web can require design modification, additional software, and some added expense.
a. true
b. false
Answers
This statement about databased design and software is true.
what is data?In the pursuit of knowledge,data is a collection of to the discrete values that convey information,descresing the quantity, quality fact and statistics and other basis units by of meaning,or simplyof the sequence of symbol that is may further interpreted.
A web-based data design requires users to have by the powerful workstations. Migrating a traditional abd to the database design to and the web can required and design modification, additional software, and to some added expense. Web-based systems are thd popular because they offer by ease of access, cost-effectiveness, and to worldwide connectivity.
To know more about data click-
https://brainly.com/question/518894
#SPJ4
what type of penetration testing technique is used if the tester has no prior knowledge of the network infrastructure that is being tested?
Answers
The type of penetration testing technique used if the tester has no prior knowledge of the network infrastructure that is being tested is a black box.
What is a black box?Either a "black box" is physically installed in the vehicle or a smartphone app is downloaded. It connects to a GPS unit that tracks the position, speed, distance, frequency of driving, and time of day the automobile is moving.
Therefore, If the tester has no prior knowledge of the network infrastructure that is being evaluated, a black box penetration testing technique is performed.
To learn more about the black box, refer to the link:
https://brainly.com/question/29762147
#SPJ1
what key word shows that a method will not return a value? group of answer choices instantiate void null parameter variable
Answers
Void functions shows that a method will not return a value, group of answer choices instantiate void null parameter variable.
Except that they do not return a value when the function executes, void functions are constructed and used just like value-returning functions. The term "void" is used by void functions in place of a data type. A void function executes a task before returning control to the caller; nevertheless, it does not return a value. The return statement has no return value, thus you can use it or not. Control will automatically return to the caller at the conclusion of the function even without the return statement. A good way to use a void function is to print a header and footer to a file or screen.
Keep in mind that the C++ language supports both void functions and value-returning functions as subprogram types.
To know about void kindly visit
https://brainly.com/question/24160353
#SPJ4
what is wireless fidelity (wi-fi)? group of answer choices includes the inner workings of a wi-fi service or utility, including the signal transmitters, towers, or poles and additional equipment required to send out a wi-fi signal. a metropolitan area network that uses radio signals to transmit and receive data. a means by which portable devices can connect wirelessly to a local area network, using access points that send and receive data via radio waves. a communications technology aimed at providing high-speed wireless data over metropolitan area networks.
Answers
Wireless fidelity allows for the creation of a Wireless Local Area Network.
What exactly is network fidelity?Network Fidelity: A Metric to Quantify the Similarity and Realism of Complex Networks. Abstract: The analysis of complex networks revolves around the fundamental properties shared by the vast majority of natural and synthetic networks that surround us.
What is network fidelity, exactly?Network Fidelity: A Metric to Quantify the Similarity and Realism of Complex Networks. Abstract: The fundamental properties shared by the vast majority of natural and synthetic networks that surround us are central to complex network analysis.
What exactly is network fidelity?Network Fidelity: A Metric to Quantify the Similarity and Realism of Complex Networks. Abstract: Complex network analysis is based on the fundamental properties shared by the vast majority of natural and synthetic networks that surround us.
learn more about wireless fidelity visit:
brainly.com/question/12719383
#SPJ4
what type of power connector would you likely use to provide supplemental power to a high-end processor?
Answers
4+4 pin 12V type of power connector would be used to provide supplemental power to a high-end processor.
As long as you are not using the EPS12V connector, this 4-pin connector, which powers your CPU, must be connected to the motherboard. Most processors, whether they are Intel or AMD, use the 4-pin ATX12V connector.
Even AMD's power-hungry FX series, up until the hexa-core series, only needs a 4-pin CPU connector. Therefore, having a pair of them on the PSU is ideal because they are more crucial to have in the big picture.
High-end computing (HEC) is the term for computer systems that have hundreds or even thousands of times the amount of processing power of a typical computer system.
A processor is the logic circuitry that responds to and executes the fundamental commands that drive a computer (CPU). The CPU is thought of as the primary and most significant integrated circuit (IC) chip in a computer because it interprets the bulk of computer commands.
Question:
what type of power connector would you likely use to provide supplemental power to a high-end processor?
4 pin Molex 6+2 pin PCle 4+4 pin 12V 20+4 pin P1To learn more about Processor click here
brainly.com/question/28255343
#SPJ4
Is Android a proprietary OS?
Answers
Android is proprietary in its majority of versions. The primary parts are from the Android Open Source Project (AOSP), which is a piece of free and open-source software principally covered by the Apache License.
Mobile touchscreen devices like smartphones and tablets are the only ones for which it is particularly made. Anyone may create any sort of gadget using the open source code for Android. However, if producers want to associate the Android brand with their goods.Android OS is a mobile operating system built on Linux that is largely used on smartphones and tablets. The Android platform consists of a Linux kernel-based operating system, a graphical user interface, a web browser, and end-user apps that may be downloaded. So, for the following reason, security, Linux is the foundation of Android. Additionally, Linux is utilized to operate a variety of systems on so many different levels, as was already explained. Linux is used by numerous complex-architectured devices, such as cars, in addition to supercomputers.
Learn more about Android here:
https://brainly.com/question/4121093
#SPJ4
Juanita lists expenses in a pivottable field named expenses. She wants to filter the pivottable to display data only for expenses greater than $1,000. What type of filter should she use?
Answers
Juanita should use to filter Value on the PivotTable to display data only for expenses greater than $1,000.
In PivotTable use the following steps:
Select Greater Than under Row Label Filter > Value Filters.
Choose the values you want to use as filters in the Value Filter dialogue box. It is the expense in this instance (if you have more items in the values area, the drop-down would show all of it). Choose the circumstance.
Then, Press OK.
Now, choose the values you want to apply as filters. It is the expense in this instance (if you have more items in the values area, the drop-down would show all of it).
• Choose the circumstance. Select "is larger than" because we want to find every expense with more than $1000 .
• Fill out the last field with 1000.
In an instant, the list would be filtered and only display expenses with more than 1000.
Similar to this, you can use a variety of different conditions, including equal to, does not equal to, less than, between, etc.
To learn more about PivotTable click here:
brainly.com/question/19717692
#SPJ4
in order to terminate multiple network cables that converge in one location such as an electrical closet or server room, what should you use?
Answers
In order to terminate multiple network cables that converge in one location such as an electrical closet or server room, we can use patch panel.
What is patch panel?A patch panel is a device or unit with a series of jacks, usually of the same or similar type, used to connect and route circuits in order to monitor, connect, and test them in a convenient and flexible way. . Patch panels are commonly used in computer networks, recording studios, radio and television.
The term patch comes from its early use in telephony and radio studios, where spare equipment could be temporarily replaced with failed equipment. This reconnection was done using patch cords and patch panels, similar to jack panels on corded telephone switches.
Learn more about patch panel https://brainly.com/question/29484618
#SPJ4
if your goal was to construct a network in which all points were connected and the distance between them was as short as possible, the technique that you would use is
Answers
The technique used is Minimum spanning tree if your goal was to construct a network in which all points were connected and the distance between them was as short as possible.
A spanning tree is a subset of Graph G that has the fewest number of edges feasible connecting every vertex. As a result, spanning trees are unconnected and lack cycles.
We can infer from this definition that every linked and undirected Graph G has at least one spanning tree. Since a disconnected network cannot be spanned to all of its vertices, it lacks a spanning tree.
A minimum spanning tree in a weighted graph is one that has the least weight among all the other spanning trees in the same graph. This weight can be quantified in the actual world as distance, traffic load, congestion, or any other arbitrary number indicated to the edges. Minimum spanning tree uses either of the two greedy algorithms namely Algorithm Kruskal and The Prim algorithm.
To learn more Spanning tree about click here:
brainly.com/question/28111068
#SPJ4
How long will it take to crack a 3 digit lock?
Answers
The range of potential integers is 0000 to 999, or 10*10*10=1000. Accordingly, it may take you anywhere between 1 attempt (if you're incredibly lucky) and 1000 efforts (if your luck is just awful).
but if you decided to try sufficient instances, it could reach near including a median of 500 chances but unless you tested all the numerals through 000 to 999 in series.
If replication is forbidden, the numerals 1, 2, 3, 4, 5, 6, 7, 8, and 9 can indeed be transformed into 504 separate 3-digit numbers. Note: The multiplier concept can also be applied to the solution of this query.
Seven different numbers can be assigned to the first digit of a three-digit number: 1, 2, 3, 4, 5, 7, and 9. Since repetition is allowable, the second and the third digits can each have 7 different values, for a total of 777=343 different possible permutations of integers. When all four digit integers are what you're after, you have 10 options for the first, 10 options for the second, and 10 options for the third, giving you a total of 10x10x10 = 1000.
To learn more about 3 DIGIT NUMBERS visit here :
https://brainly.com/question/6073713
#SPJ4
__________ are a part of big data analytics that allow a company the opportunity to analyze location data from mobile phones of employees.
Answers
Location analytics is a part of big data analytics that enables a company the opportunity to analyze location data from the mobile phones of employees.
Location analytics is an extra layer of geographical data for a business that allows a company to extract more valuable insights, and gain a deeper understanding of its staff's or consumers' activities.
Location analytics combines geographic data on assets, transportation, infrastructure, and the environment with data on an organization's business operations and consumers to determine powerful answers to any business issue and share these insights with the rest of the organization.
You can learn more about location based analytics at
https://brainly.com/question/7334919
#SPJ4
which database security risk occurs when data from a higher classification level is mixed with data from a lower classification level?
Answers
The database security risk that occurs when data from a higher classification level is mixed with data from a lower classification level is known as a security breach.
This kind of security breach can happen if data from various classification levels is kept in the same database or on the same server, or if data from a higher classification level is sent to a device or system that isn't allowed to access it.
This kind of security lapse can result in serious repercussions, such as the unauthorized disclosure of private or sensitive information, harm to an organization's reputation, and legal liabilities. Additionally, it can weaken the database's overall security, leaving it open to attacks from bad actors.
Implementing appropriate security controls and procedures is crucial to ensuring that data from various classification levels is kept separate and secure and to preventing this kind of security risk.
To know more about database security risk kindly visit
https://brainly.com/question/29375527
#SPJ4
nearshore outsourcing occurs when using organizations from developing countries to write code and develop systems. in offshore outsourcing the country is geographically far away. group of answer choices false true
Answers
Overseas outsourcing utilizing businesses in poor nations to create systems and produce code.
Organizations from underdeveloped nations are used in offshore outsourcing to write code and create systems. Offshoring, however, is a subset of outsourcing in which a business contracts with a third party to provide services in a nation other than the client company's home country in order to benefit from cheaper labor costs. Quality and efficiency improvements, lower operating costs, the ability for businesses to concentrate on their core competencies by outsourcing non-core functions, decreased risk exposure, access to outsourcing service providers' economies of scale, expertise, and best-in-class practices, and access to cutting-edge technologies.
Learn more about system here-
https://brainly.com/question/14253652
#SPJ4
what file systems supported by windows can be used for volumes and drives that don't hold the windows installation? (choose all that apply.)
Answers
ExFAT, FAT32, and NTFS file systems supported by windows can be used for volumes and drives that don't hold the windows installation. A computer's file system is a storage structure for managing data. Users can easily and rapidly access info thanks to it.
ExFAT: Large external storage devices that can be used with other operating systems use the exFAT The following characteristics apply to exFAT:
ExFAT partitions have a maximum disc size of very large. The recommended maximum is 512 TiB.An exFAT partition may hold files up to 16 EiB.Linux and Unix are incompatible with exFAT.Defragmenting exFAT partitions frequently is advised.ExFAT is unable to reserve disk space.file system, which is supported by Windows.FAT32: Windows is compatible with the FAT32 file system, which is used with compact hard drives and USB flash devices. Only small-capacity devices where switching between operating systems is crucial often employ FAT. FAT is not advised unless you are running an earlier version of Windows when selecting a file system for a hard disk.
NTFS : Windows supports the NTFS file system, which was created to take the place of the FAT32 file system. File and folder compression, disk quotas, and encryption are all supported by NTFS. For the volume on which Windows is installed, NTFS is also necessary. On all media that is typically utilized with current Windows systems, NTFS is advised. It shouldn't be utilized on media in devices that aren't NTFS compatible or for devices that Mac OS X systems require to write to.
To learn more about file system click here:
brainly.com/question/29812361
#SPJ4
you are the manager for the westsim domain. the network has a single subnet with five servers all running windows server. the 100 client computers are all windows desktops. one of the servers is configured as a dhcp server configured with a single scope for the 10.0.0.0/24 subnet. your network has three printers with built-in print servers. these printers are configured as dhcp clients. you want to make sure that each printer gets the same ip address each time it starts up. you configure an exclusion range of 10.0.0.12 to 10.0.0.14 for the printers. you also configure a reservation for each printer. you are informed that no one is able to connect to the printers. you use management software and find that none of the printers have been assigned appropriate ip addresses. what should you do?
Answers
You have to Delete the exclusion range on the DHCP server.
An IP address range that is specifically excluded from a DHCP range is known as an exclusion range. An exclusion range is a sub-object of a conventional DHCP range and is described as a start/end IP address pair within an ipam/range object. You can manually allocate certain addresses to servers by excluding them from the scope range.
An excluded address or range of addresses is one that the DHCP server is not permitted to distribute from a DHCP scope. A device on your network could only receive the address 192.168.0.4 if you assigned it statically, for instance, if you've configured a DHCP server to ignore the address range 192.168.0.1-192.168.0.10 on that apparatus. This is because DHCP is aware that it should NOT distribute this IP address range.
To learn more about DHCP click here:
brainly.com/question/10097408
#SPJ4
Is Unix proprietary OS?
Answers
A proprietary operating system is Unix.Although the Unix operating system uses a CLI ,a GUI for Unix computers.An OS that is popular in businesses, academic institutions, large corporations.
Web servers, mainframes, and supercomputers frequently employ proprietary Unix operating systems (and Unix-like variations) that run on a broad range of digital architectures. In recent years, versions or variations of Unix operating on smartphones, tablets, and personal computers have grown in popularity. UNIX comes in a variety of variations, yet they all have some characteristics. The three most widely used UNIX variants are Sun Solaris, GNU/Linux, and MacOS X. In turn, Linux is packaged in what is referred to as a Linux distribution. Numerous Linux distributions exist, both free and paid. Nonproprietary software is open source and accessible for free download and usage. It also makes its source code completely available. Software that is not proprietary can also be referred to as open-source software.
Learn more about operating system here:
https://brainly.com/question/6689423
#SPJ4
if you are a photographer and you frequently need to resize your images to a certain size and resolution to fit inside a gallery on your website, how can you create a reusable setting that you can quickly apply to new images in the future?
Answers
You can create a reusable setting to apply to new images in the future to resize your images to a certain size and resolution to fit inside a gallery on your website, by clicking on Image in Photoshop, then Image Size and entering your settings. Then click the Fit to.. drop down and choose Save Preset.
Photoshop is a raster graphic design and photo editing program that enables users to create, modify, and work with a variety of graphics as well as digital art. Additionally, it enables the creation and editing of multi-layered raster pictures, as well as the import of images in different file types. Adobe Systems creates Photoshop for both Windows and MacOS.
Image size is the measurement of an image's width and height, expressed in pixels. Although it also refers to the overall number of pixels in the image, what matters are the width and height. Based on its current picture size, image resolution determines how large or tiny the photo will print.
It's critical to realize up front that image resolution only influences how big an image will print. When you see the image on the screen, it has absolutely no impact.
To learn more about Resolution click here:
brainly.com/question/29576792
#SPJ4
what type of malicious code could be installed in a system's flash memory to allow an attacker to access the system at a later date?
Answers
There are several types of malicious code that could be installed in a system's flash memory to allow an attacker to access the system at a later date. One type of malicious code that could be used for this purpose is known as a rootkit.
Malware called a "rootkit" is made to access systems with elevated privileges while avoiding detection by security programs. Rootkits are frequently stored in a computer's flash memory or other persistent storage because they can stay hidden and continue to function even when the system is rebooted.
When a rootkit is planted in a system's flash memory, it can later enable remote access to the machine, allowing an attacker to carry out a variety of tasks like installing other malware, stealing confidential information, or taking over the system. Rootkits can also be used to get around security measures and enter restricted regions of the system without authorization.
It's crucial to maintain a system updated with the most recent security patches, use antivirus software, and take other security precautions to guard against malware in order to avoid rootkits and other forms of harmful code from being installed in the system's flash memory. Additionally, it's critical to exercise caution while downloading and installing software from unreliable sources and to be alert to any potential security risks.
To know more about malicious code kindly visit
https://brainly.com/question/29549959
#SPJ4
write a risc v program using instructions in the risc v isa to calculate the sum of the squares of all odd numbers between 0 and n where n is an integer < 100
Answers
The risc v program below calculates the sum of the squares of all odd numbers between 0 and n, where n is an integer 100, using instructions from the risc v isa.
FACTORIAL OF A NUMBER:
.text # recursive implementation of factorial
.globl __start
fact: # arg: n in a0, returns n! in a1
addi sp, sp, -8
sw ra, 0(sp)
li t0, 2
blt a0, t0, ret_one # 0! and 1! == 1
addi a0, a0, -1
jal fact # call fact (n-1)
# a1 <- fact(n-1)
lw t0, 4(sp) # t0 <- n
mul a1, t0, a1 # a1 <- n * fact(n-1)
j done
ret_one:
li a1, 1
done:
lw ra, 0(sp) # restore return address from stack
addi sp, sp, 8 # free our stack frame
jr ra # and return
__start:
li a0, 5 # compute 5!
jal fact
li a0, 1 # print it
ecall
li a0, 17
ecall # and exit
To know more about risc v program, visit: https://brainly.com/question/15583899
#SPJ4
__________is responsible for maintaining and administering computer networks and related computing environments including systems software, applications software, hardware, and configurations.
A. Network Administrator/Network Engineer
B. Network Security Analyst
C. Systems Engineer
D. Network Consultant
Answers
Answer: i think would be c but im not sure
im very sorry if you get it wrong!
A computer network that is restricted to the organization it serves; an internal internet.t/f
Answers
A computer network that is restricted to the enterprise it serves is called an internal internet. Therefore, the statement given is a true statement.
An internal internet also referred to as an intranet is a local network that is only accessible to people within an enterprise. The internal internet is the most restricted network. It can be stated as the internal internet is a private network setup within an enterprise that is used to securely share organizational information and computing resources among its employees.
Therefore, it is concluded that the internal internet or intranet is the restricted computer network to be used by the enterprise only.
You can learn more about intranet/internal internet at
brainly.com/question/13139335
#SPJ4
you have developed a new computer operating system and are considering whether you should enter the market and compete with microsoft. microsoft has the option of offering their operating system for a high price or a low price. once microsoft selects a price, you will decide whether you want to enter the market or not enter the market. if microsoft charges a high price and you enter, microsoft will earn $30 million and you will earn $10 million. if microsoft charges a high price and you do not enter, microsoft will earn $60 million and you will earn $0. if microsoft charges a low price and you enter, microsoft will earn $20 million and you will lose $5 million. if microsoft charges a low price and you do not enter, microsoft will earn $50 million and you will earn $0. In a simultaneous move game, Microsoft will and you will:___________
Answers
In a simultaneous move game, Microsoft will and you will If Microsoft asks for a higher price, it could be $30 million or $60 million. If the company were to charge the lower price, it would be $20 million or $50 million. The best strategy is to charge a higher price.
What is price market?Market price is the current price at which an asset or service can be bought or sold. The market price of an asset or service is determined by supply and demand. The market price is the price at which the quantity supplied equals the quantity demanded. Market prices depend on the interaction of supply and demand. Equilibrium price is the balance of demand and supply factors.
Learn more about market price: https://brainly.com/question/24877850
#SPJ4
Software license allows a predetermined number of people to use the account at the same time with same login info
Answers
Software license allows a predetermined number of people to use the account at the same time with same login info is called Concurrent license.
What is concurrent license?A concurrent software license is a kind of license based on the most users who will use it concurrently. For instance, if a business buys five concurrent licenses, it means that a maximum of five of its employees may use the software concurrently.
Therefore, through its used, you can put a limit on the number of concurrently running applications with concurrent licenses. As a result, each user is permitted to utilize the resource as many times as the limit has been established.
Learn more about license from
https://brainly.com/question/13502276
#SPJ1
briefly explain the differences and capabilities between various data recording/capture systems. compare and contrast the value between onboard capture systems and down-linking data systems. why are such systems usually not mandated on private general aviation aircraft?
Answers
Data recording/capture systems are used to store and record all kinds of aircraft data and usually include onboard recording systems and down-linking data systems.
Onboard recording systems capture and store data on the aircraft itself and can include Flight Data Recorders (FDRs) and Cockpit Voice Recorders (CVRs). FDRs capture data such as airspeed, altitude, and engine parameters, while CVRs capture audio data such as transmissions, conversations, and other sounds inside the cockpit.
Down-linking data systems involve real-time data transmission from the aircraft to a ground station or other aircraft. This data can include data from the FDR and CVR as well as other systems such as GPS and navigation systems.
The value of onboard capture systems is that they store data on the aircraft itself, which allows investigators to access the data in the event of an accident. On the other hand, down-linking data systems provide real-time data transmission from the aircraft and can be used to provide more detailed information about the aircraft’s activities.
This information can be used to monitor the aircraft, provide better situational awareness and provide more insight into the cause of an accident.
Private general aviation aircraft are usually not mandated to have data recording/capture systems due to the cost and complexity of the systems. Additionally, private general aviation aircraft are not typically used in commercial operations and therefore do not require the same level of data recording and monitoring as larger commercial aircraft.
For more questions like Data recording systems click the link below:
https://brainly.com/question/29806749
#SPJ4
If the input message is omitted when creating a data validation rule for a cell, no message will appear when the user selects the cell.
a. True
b. False
Answers
It is a true statement that if the input message is omitted while creating a data validation rule for a cell, no message will show when the user selects the cell.
A data validation rule is a process through which a user is restricted to input incorrect or invalid values cells. With the data validation rule, the user is prompted to enter a valid value in a selected cell. Since a data validation rule defines the type of data value that can be entered into a cell; the input message is an optional property that enables to provide with a custom message to appear to the user when the cell is selected. In case when an input message is not specified while creating a data validation rule for the cell, no message will appear when the user selects that cell.
You can learn more about data validation at
brainly.com/question/20411239
#SPJ4
baltimore mayor is planning a network to cover city of baltimore, such a network topology will be called
Answers
The correct answer to the given question of network coverage is option D) None of the above.
Mayor of Baltimore has used the RAN network to cover the city of Baltimore.
The component of a mobile network that links end-user devices, such as smartphones, to the cloud is called a radio access network (RAN). To do this, information is transmitted by radio waves from end-user devices to a RAN's transceivers, and then from the transceivers to the core network, which is connected to the internet worldwide.
Numerous servers or computers can access a shared storage pool that is provided by an interconnected network of storage devices known as a SAN (storage area network). Any computer linked to the network can access storage on the SAN as if it were local disks in that computer.
Question
Baltimore's mayor is planning a network to cover the city of Baltimore, such a network topology will be called
A. Secure area network (SAN)
B. Local area network (LAN)
C. Wide area network (WAN)
D. None of the above
To learn more about network click here
brainly.com/question/29588111
#SPJ4
how does the structure of an online analytical processing (olap) database shape its core functionality?
Answers
Online Analytical Processing, or OLAP, is a class of software that enables users to gather and analyze corporate data from many angles. To enhance the data analysis process, it uses pre-calculated and pre-aggregated data from many databases.
Multiple data structures called OLAP cubes are used to organize OLAP databases. A unique type of data structure called the OLAP cube or Hypercube is designed for extremely rapid multidimensional data analysis and storage. It is a snapshot of data taken at a particular moment in time.
A user can ask for a specific view of the hypercube using certain OLAP procedures. OLAP cubes enable users to run multidimensional analytical queries on the data as a result.
MOLAP is another name for OLAP in its traditional form. It stores data using a multi-dimensional array storage technology that has been optimized. To retrieve the data physically stored in multidimensional arrays, positional approaches are used.
To learn more about OLAP click here:
brainly.com/question/26691784
#SPJ4
declare and create a two-dimensional array of ints, plan, with 2 rows, and initialize the first row to 8, 20, 50 and the second row to 12, 30, 75.
Answers
To declare and create a two-dimensional array of integers called plan with 2 rows, you can use the following code:
int[][] plan = new int[2][3];
To initialize the first row of plan to the values 8, 20, 50, you can use the following code:
plan[0][0] = 8;
plan[0][1] = 20;
plan[0][2] = 50;
To initialize the second row of plan to the values 12, 30, 75, you can use the following code:
plan[1][0] = 12;
plan[1][1] = 30;
plan[1][2] = 75;
Code is a set of instructions or statements that are written in a computer programming language. It is used to create software and applications that can be run on computers, smartphones, and other devices. Code typically consists of commands, variables, and other elements that are written using a specific syntax and structure according to the rules of the programming language. It is used by programmers to create and control the behavior of computer programs.
Learn more about code, here https://brainly.com/question/497311
#SPJ4
describe an algorithm that takes as input a list of n distinct integers and finds the location of the largest even integer in the list or returns 0 if there are no even integers in the list.
Answers
An algorithm is a method for performing calculations or finding solutions to issues.
Algorithms perform as a precise set of instructions that carry out preset activities consecutively in either hardware-based or software-based routines.
Algorithms play a big role in information technology across the board. In mathematics and computer science, an algorithm is often referred to as a straightforward method that solves a recurrent problem. Automated systems require algorithms because they provide the guidelines for data processing.
For straightforward jobs like sorting lists of numbers, or for more difficult ones like recommending user content on social media, an algorithm may be used. An algorithm's initial input and computational instructions are frequently given. The result of the calculation is produced as an output.
Learn more about algorithm here-
https://brainly.com/question/22984934
#SPJ4
Assume that chessboard has been declared to be a two-dimensional array of strings. Write a statement that instantiates an 8x8 array of strings and assign it to chessboard.
Answers
The statement that instantiates an 8x8 array of strings is chessboard = new String[8][8]
Explain what an array is:This arrays is a grouping of identically typed items that are stored in adjacent memory regions and may each be separately referred to via a reference to a special identifier. There is no need to declare five distinct variables when declaring an array of five int values (each with its own identifier).
What does the Excel term array mean?A formula with numerous computations capabilities on one or maybe more elements in an array is known as that of an array formula. An assortment can be thought of as a row, column, or mix of rows or columns of values.
To know more about Array visit:
https://brainly.com/question/19570024
#SPJ4