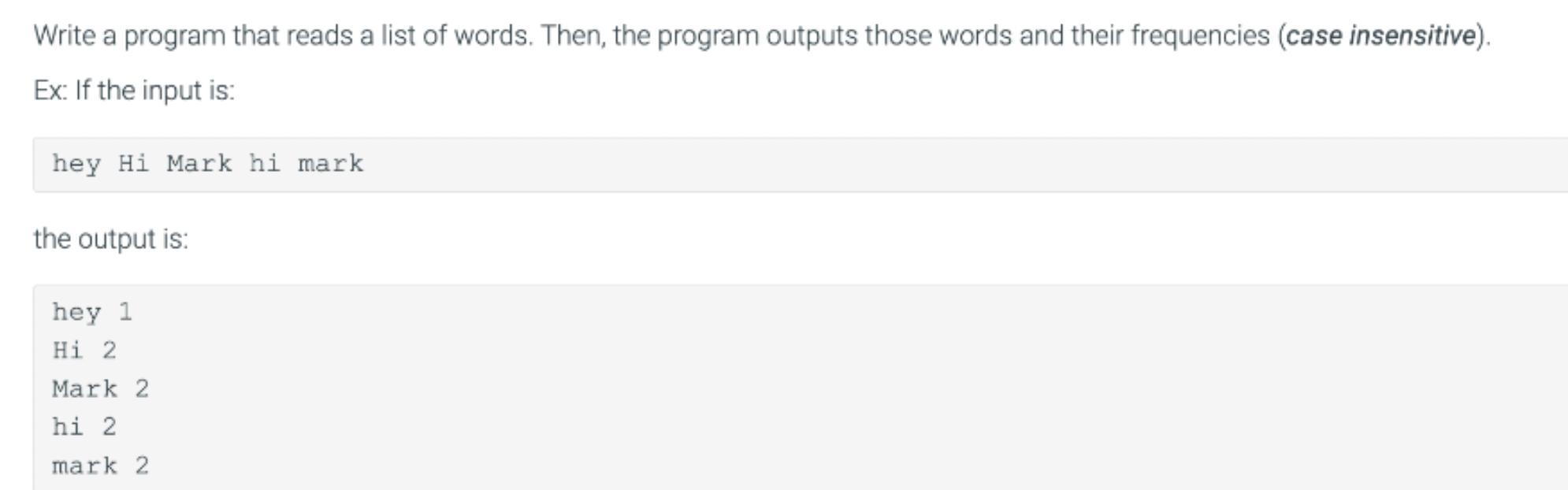
Write a program that reads a list of words. Then, the program outputs those words and their frequencies (case insensitive).
Answers
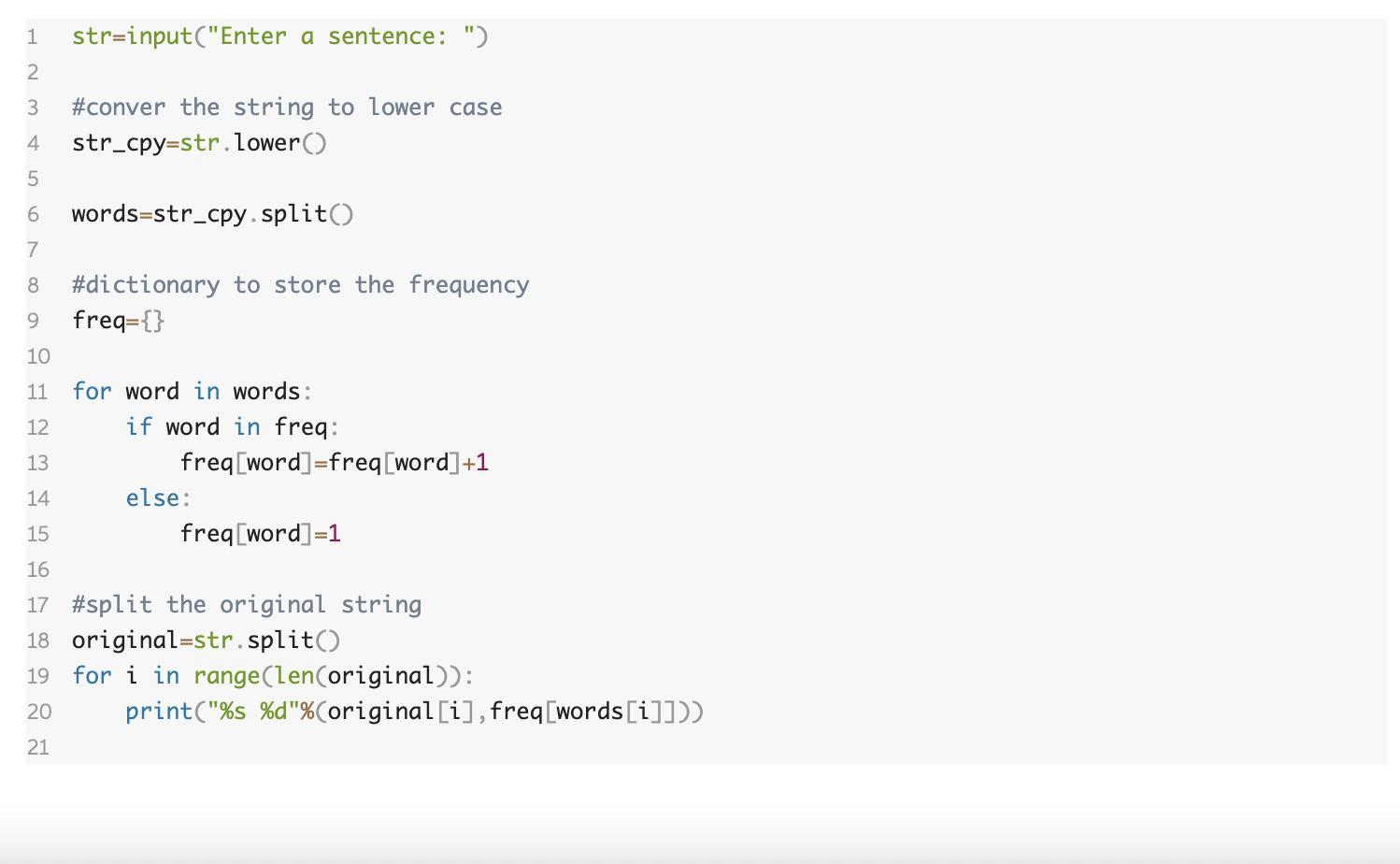
The program str= input (''Enter a sentence: reads a list of words. The program then outputs those words and their frequencies
Example Input: hey Hi Mark hi mark
Example Output: hey
1
Hi 2
Mark 2
hi 2
Mark 2
PROGRAM
1
str=input("Enter a sentence:
")
2
3
4
#conver the string to lower case
str_cpy=str.lower
5
6
words-str_cpy.splitO
7
8
9
#dictionary to store the frequency
freq-{z
10
11 for word in words:
12
if word in freq:
13
freg word]=freg word]+1
14
else:
15
freq[word]=1
16
17 #split the original string
18 original=str. splitO
19 for i in range(len(original)):
20
print("% %d"%(original[i],freq[wordsLi]]))
To learn more about the program
https://brainly.com/question/14368396
#SPJ4
Related Questions
An academic plan is a set of challenges relating to the things you don't want to accomplish while you are on a job.
TRUE
OR
FALSE
Answers
An academic plan is a set of challenges relating to the things you don't want to accomplish while you are on a job is false.
What exactly is a course of study?The fields of study within a program, including majors, minors, streams, and strands, as well as the study location, are referred to as the "Academic Plan" or "Plan." Samples 1 and 2 The term "academic plan" refers to a summary of the program credit requirements for finishing a certain program of study.
Therefore, student's desired course schedule for the following semester or for several semesters is outlined in an academic plan. A platform for academic planning ought to offer guidelines and boundaries based on students' major and degree requirements, upcoming course availability, and speed of degree completion.
Learn more about academic plan fromhttps://brainly.com/question/21300074
#SPJ1
) why did intel stop using numbers (286, 386, etc.) to identify their processors, and switch to using names (pentium, itanium, etc.)?
Answers
Intel stopped using numbers (such as 286, 386, etc.) to identify their processors and switched to using names (such as Pentium, Itanium, etc.) for a number of reasons.
The numerical naming approach had became complicated and challenging for consumers to understand, which was one reason for the move. Consumers found it more difficult to decide which processor was the most powerful or best suited for their needs as the variety of processor models grew.
Another reason was that using names helped Intel to better distinguish its CPUs from one another and to explain to customers the benefits of each model. Intel could highlight the distinctive qualities of each processor and establish a stronger corporate identity by employing names.
Finally, using names gave Intel additional flexibility and the ability to adjust to shifting market conditions. Intel could more readily release new models and phase out older ones if they had names.
To know more about Processors kindly visit
https://brainly.com/question/28902482
#SPJ4
What property of virtualization allows entire virtual machines to be saved as file that can moved or copied like any other file?
Isolation
Hardware Independence
Partitioning
Encapsulation
Answers
Property of virtualization that allows entire virtual machines to be saved as file that can moved or copied like any other file is known as encapsulation
What is encapsulation?Encapsulation describes the concept of encapsulating information and the strategies that perform on that information right into a single unit, like a class in Java. This idea is likewise frequently used to cover the internal representation or state of an object from the outside. This is called information hiding.
The general concept of this mechanism is simple. For example, you've a property that is not visible from outside an object. You bind it to methods that provide read or write access. Encapsulation lets in you to hide specific information and control access to an object's internal state.
Lean more about encapsulation https://brainly.com/question/29107336
#SPJ4
what are some challenges to software parallelism? (check all that apply) group of answer choices hardware parallelism is not well developed. algorithms must be analyzed to determine parallelizability. interconnection network overhead may outweigh the benefits of implementing parallelism.
Answers
The costs of the interconnection network may outweigh the advantages of using parallelism. To establish if an algorithm is parallelizable, it must be examined.
What kind of algorithm would that be?The process to do laundry, the way we solve a widely used for solving problem, the ingredients for making a cake, and the operation of a search service are all instances of algorithms.
What is an algorithm's straightforward definition?An algorithm is the method used to carry out a computation or solve a problem. In either hardware-based or software-based routines, algorithms function as a detailed sequence of instructions that carry out predetermined operations sequentially. All facets of data tech utilise algorithms extensively.
To know more about Algorithm visit :
https://brainly.com/question/15393908
#SPJ4
a standard user attempting to install software or make changes without sufficient permissions places the os in secure desktop mode. what do they need to continue?
Answers
It is to be noted that a standard user attempting to install software or make changes without sufficient permissions places the OS (Operating System) in secure desktop mode. In order to continue, they must enter a User Account Control Password.
What are windows permissions?When you configure permissions, you tell people what they can and cannot do within a folder, such as save and remove files or create new folders. You are not restricted to one of the normal permissions settings (Full Control, Modify, Read & Execute, List Folder Contents, Read, or Write)
User Account Control (UAC) assists enterprises in deploying a better-managed desktop by preventing malware from destroying a PC. Unless an administrator explicitly grants administrator-level access to the system, UAC programs and tasks always execute in the security context of a non-administrator account.
To disable Windows 10 UAC, just turn it off. Note that this technique puts your ecosystem in danger.
Learn more about Windows Permissions:
https://brainly.com/question/29219075?
#SPJ1
A website that relies heavily on word of mouth might consider including what element on its website.
Answers
A website that relies heavily on word of mouth might consider including link to social media accounts on its website.
What is website?A website is a collection of web pages and related content that are identified by a common domain name and published on at least one web server. All publicly accessible web pages together form the World Wide Web. There are also private websites that can only be accessed on a private network, such as the company's internal website for its employees.
Websites are often dedicated to a specific topic or purpose, such as news, education, business, entertainment, or social networking. Hyperlinks between web pages guide website navigation, usually starting with the home page. Users can access websites on a variety of devices, including desktops, laptops, tablets, and smartphones. The application used on these devices is called a web browser.
Learn more about website https://brainly.com/question/28431103
#SPJ4
which of the following actions occur at the beginning of an iteration of the data step? a. the automatic variables n and error are incremented by one. b. the values of variables created in programming statements are re-set to missing in the program data vector.
Answers
Answer:
Option (A)
Explanation:
The DATA step begins with a DATA statement. Each time the DATA statement executes, a new iteration of the DATA step begins, and the _N_ automatic variable is incremented by 1. SAS sets the newly created program variables to missing in the program data vector (PDV).
What does authoritarian mean? ruling authority is granted to individuals by the government ruling by aristocracy requiring acknowledgment of authorship requiring strict obedience to an authority, such as a dictator
Answers
Answer:
Authoritarian means requiring strict obedience to an authority, such as a dictator.
Question 1 of 20
"Once a business operations analysis is completed and change needs to
occur, many businesses will create a _________ that includes information
technology. A__________ is a long-term plan of action created to achieve a
certain goal." Which of the following answers fits into both blanks?
A. communication plan
B. business strategy
C. scheduling plan
D. technology strategy
Answers
Answer:
B.Business strategy
Explanation:
a user has two files open in microsoft word; one is named salary.docx and the other is named pay.docx. when the user makes a change to salary.docx, the pay.docx window updates with the change that was just made to salary.docx. why does this happen?
Answers
Note that where a user has two files open in Microsoft word; one is named salary.docx and the other is named pay.docx. Where the user makes a change to salary.docx, the pay.docx window updates with the change that was just made to salary.docx. This happened because "The pay.docx file is hard linked to the salary.docx file."
What does it mean for two files to be hard-linked?A hard link is a file system representation of a file in which many paths lead to the same file in the same drive.
The ls -li command is the true litmus test. The inode for each of the two files will be shown by this command. If the inodes match, the files are truly hard links, sharing disk space as well as the inode structure that holds their metadata (owner, permissions, etc.).
rm is the command used to remove a hard link. Remove (unlink) the FILE, according to the rm man page (s). Save this response.
Learn mroe about hard linking:
https://brainly.com/question/14100302
#SPJ1
How many possible combinations are there for a 3 digit lock?
Answers
The list of available combinations for this 3-dial lock, which has 3 functions having numbers 0-9 on all, is 1,000.
If repetition is forbidden, the numerals 1, 2, 3, 4, 5, 6, 7, 8, and 9 could be converted into 504 separate three - digit values. Remarkably, the multiplying concept can also be applied to the solution of this query. Seven different values can be assigned to the initial number of a three-digit number: 1, 2, 3, 4, 5, 7, and 9. There are a total of 777=343 possible variations of integers as duplication is permissible. The second figure can possibly incorporate 7 different possibilities, and also the final can have 7 different value systems as well.
Though all 3 digit figures are something that you're seeking, users got Ten possibilities on the first, Ten alternatives for such second, and 10 options for the third, bringing you a total of 10x10x10 = 1000.
To learn more about 3 DIGIT NUMBERS visit here :
https://brainly.com/question/6073713
#SPJ4
in the e-r model, if each entity in a set s can be associated with two or more entities in set t, but each entity in t can be associated with only one entity in s, then the binary relationship from s to t is called
Answers
Binary relationships involve two participants and are defined as such. The number of instances of an entity from a connection that can be linked to the relation is measured by its cardinality.
There may be various numbers of entities on each side of a relationship. For instance, any number of consumers can purchase any number of products, and any number of customers can purchase any number of products. A many-to-many relationship is what this is. A weak entity set connects to other (supporting) entity sets through one or more many-one relationships. By omitting the entity set (DbSet attribute) for the joining table in the CSDL and visual designer, Entity Framework displays many-to-many relationships. Instead, it uses mapping to control this.
Learn more about binary here-
https://brainly.com/question/18502436
#SPJ4
if i am using all features of my dataset and i achieve 100% accuracy on my training set but 70% on my testing set, what should i be correcting?
Answers
If i am using all features of my dataset and i achieve 100% accuracy on my training set but 70% on my testing set, I would be correcting Model overfit
What does high training accuracy mean?
Training accuracy means that identical images are used for both training and testing, and test accuracy means that the trained model identifies independent images that have not been used in training.
What is data overfitting?Overfitting occurs when a model fails to generalize and instead fits the training dataset tightly. Overfitting occurs for several reasons, including: The training data size is too small and does not contain enough data samples to accurately represent all possible input data values.
Does overfitting mean better accuracy?The high level of accuracy measured on the training set is the result of overfitting. Overfitting occurs when a machine learning model tries to cover all data points in a given database or beyond the required data points.
Learn more about overfitting data :
brainly.com/question/29382846
#SPJ4
you have a computer that runs windows 10. you use windows backup and restore to create a backup image. you need to perform a complete restore of the computer. what are the possible ways to begin the restore?
Answers
Select Control Panel > System and Maintenance > Backup and Restore by performing a right-click on the Start button. Select Create a system image in the left pane, and then go through the wizard's instructions.
A system image backup on Windows 10 is a dated feature that enables you to make a "full backup" to a USB drive. In other words, a full backup is a copy of the entire system disk and secondary drives (if appropriate), which includes all of the files and settings necessary for the installation of Windows as well as all apps, settings, and files. You can restore Windows 10 in the event of a hard drive failure by using the System Image Recovery tool from the Recovery Drive.
Learn more about system here-
https://brainly.com/question/14253652
#SPJ4
In what ways can the different forms of communication be enhanced with the aid of technology.
Answers
Technology can enhance the communication by making it faster.
How technology affects communication?Technology has changed everything in modern society. The way we communicate has been revolutionized by the advancement of new innovations in the telecommunications industry. Easily connecting with others is more possible in today's world, and that's because of the speed.
Centuries ago, books and newspapers reigned as the only choice of communication. Later, innovators brought radio and television before innovation took off with the arrival of the personal computer. With each new innovation, reliance on books as a means of mass communication continues to decrease. Over time, human culture has come to understand the forces and mechanisms involved in technology and invention. In today's world, information has permeated cycles of change and development.
Learn more about technology in communication https://brainly.com/question/18680753
#SPJ4
double-click the groups folder in the left pane to see a list of groups windows creates. double-click the users group and you see a list of users who are members of the users group, including newguest1. provide the required information true or false? users are prevented from making accidental or intentional system-wide changes and can run most applications.
Answers
Yes, it's true to avoid accidental changes by users, user groups are made. You can see members of the user groups newguest1, special groups like Authenticated Users, and INTERACTIVE, which are internal groups used by Windows.
Users and Administrators are the two built-in groups that are most frequently utilized. You have a high level of privilege on the system and are able to complete practically any job that isn't specifically protected by the operating system if your user account is a member of the Administrators group.
However, if your user account belongs to the Users Group, you are not allowed to install software into the restricted Program Files directory, alter protected areas of the registry, or change the Windows directory. Instead, you can run installed programs and make changes that won't affect the stability of the system. In Windows, the Power Users group was frequently utilized.
To learn more about User groups click here:
brainly.com/question/15500156
#SPJ4
bill has parkinson's disease and often experiences uncontrollable shaking. bill's lack of control over his motor movements is caused by low levels of the neurotransmitter:
Answers
Bill's lack of control over his motor movements is caused by low levels of the neurotransmitter dopamine.
What is Parkinson's disease?Parkinson's or Parkinsonism is brought on by a decline in dopamine levels in the brain. The most noticeable Parkinson's disease signs and symptoms are when the nerve cells in the basal ganglia of the brain, which control movement, are damaged or killed.
The brain cells that produce dopamine slowly deteriorate because, without it, the cells that regulate movement cannot properly communicate with the muscles.
Therefore, low levels of the neurotransmitter dopamine are the root cause of Bill's inability to control his motor actions.
To learn more about Parkinson's disease, refer to the link:
https://brainly.com/question/13508690
#SPJ1
when does your computer need to know the mac address of a host you are connecting to, how does it determine it?
Answers
Your computer needs to know the MAC (Media Access Control) address of a host when it wants to communicate with that host over a network.
Each device on a network is given a specific identifier called a MAC address, which is used to identify the device and initiate contact with it.
A computer can find the MAC address of a host it wants to connect to in a number different ways. One method is for the computer to broadcast a request over the network for the host's MAC address. All networked devices receive this message, but only the host with the desired MAC address will reply.
A computer can also use the Address Resolution Protocol to find out a host's MAC address (ARP).A computer can use ARP to identify the MAC address of a host based on its IP address when it wishes to interact with a host on the same network.
The MAC address of a host can also be found by a computer by looking up the address in a cache or table of previously known MAC addresses. In order to search up a host's MAC address fast in the future without having to broadcast a message or utilize ARP, a computer caches the host's MAC address when it connects with it.
To know more about MAC (Media Access Control) address kindly visit
https://brainly.com/question/29670807
#SPJ4
There is no ability to check or monitor if your email address was found on the dark web.
a. True
b. False
Answers
The statement " There is no ability to check or monitor if your email address was found on the dark web" is True.
What is the web?
The World Wide Web, or simply "the Web," is an information system that enables users to access papers and other web resources over the Internet. Through web servers, which can be accessed by software like web browsers, documents and downloadable media are made available to the network. Not just scientists had access to the internet before the advent of the world wide web. It unified the globe in a way that facilitated communication, sharing, and information access for everyone. The World Wide Web, sometimes known as the Web, the WWW, or just the Web, is a network of open websites that may be accessed online. The Web is not synonymous with the Internet: it is one of many applications created on top of the Internet.
To learn more about the web, use the link given
https://brainly.com/question/13211964
#SPJ4
which three layers of the osi model provide similar network services to those provided by the application layer of the tcp/ip model? (choose three.)
Answers
OSI uses three layers -- application, presentation and session -- to provide similar network services to those provided by the application layer of the tcp/ip model.
What is the OSI model?
The International Organization for Standardization (ISO), which was founded in the late 1970s, created the seven-layer Open System Interconnection (OSI) Model. The Open Systems Interconnection model, which is a conceptual framework, "provides a common basis for the coordination of [ISO] standards development for the purpose of systems interconnection."
The OSI reference model's goals are to promote a clear framework that explains the functions of an operational networking or telecommunications system and to provide direction to technology vendors and developers to ensure that the digital communications products and software programs they develop can interoperate.
To learn more about an OSI model, use the link given
https://brainly.com/question/13041596
#SPJ4
7. after the disk partition is first formatted, the beginning of a free space bitmap looks like this: 1000 0000 0000 0000 (the first block is used by the root directory). as we discussed during the lecture, the system always searches for free blocks starting at the lowest numbered block, so after writing file a, which uses six blocks, the bitmap would change to 1111 1110 0000 0000... . show the bitmap after each of the following actions: a) file b is written, using five blocks; b) file a is deleted; c) file c is written, using eight blocks; d) file b is deleted. (5 points)
Answers
File B is written, using five blocks 1111 1111 1111 0000 is the disk partition is first formatted, the beginning of a free space bitmap.
What is free space bitmap?Free space bitmap is defined as one technique some file systems employ to keep track of allocated sectors. The bitmap's key benefit is that it can quickly and accurately locate both the initial free block and subsequent free blocks on the disk.
File A is deleted 1000 0001 1111 0000
File C is written, using eight blocks 1111 1111 1111 1100
File B is deleted. 1111 1110 0000 1100
Thus, file B is written, using five blocks 1111 1111 1111 0000 is the disk partition is first formatted, the beginning of a free space bitmap.
To learn more about free space bitmap, refer to the link below:
https://brainly.com/question/23910641
#SPJ1
______ is a technique in which data are gathered about individuals and used to serve up personalized messages to prospective voters.
Answers
In the process of microtargeting, information about specific people is acquired and utilized to provide tailored messages to potential voters.
What happens to deleted texts?Text messages are stored by the operating system for Android there in phone's ram, so if they are erased, there is no way to get them back. However, you may download a text backups program from the Play store and use it to restore any lost texts.
Why are my mails failing to send?Typical causes of SMS message failures include the following: Unable to contact the intended handset. Text is really not allowed by the destination phone number. The Text message is longer than the allotted 160 characters.
To know more about Messages visit:
https://brainly.com/question/26928820
#SPJ4
write a statement that calls the function addtostock with parameters computerinfo and addstock. assign computerinfo with the value returned.
Answers
A statement that calls the function addtostock with parameters computerinfo and addstock is:
computerInfo=AddToStock(computerInfo,addQty);
What is parameters?In computer programming, a parameter is a particular type of variable that is used to pass data between functions or procedures. Arguments are exchanges of actual information.
The system and the programming language both have rules that govern how arguments are passed to functions. These rules specify whether the arguments will be passed using the stack, machine registers, or any other method.
It details the order of the arguments (from left to right or right to left); whether the arguments will be passed by value or by reference; and other details. Furthermore, only one argument is permitted per function in languages like Haskel and HL; in these languages, extra arguments must be passed through multiple functions.
Learn more about parameters
https://brainly.com/question/13794992
#SPJ4
Write a for loop to print the numbers 76, 70, 64, ...34 on one line.
Expected Output
76 70 64 58 52 46 40 34
Answers
A loop is a programming construct that is used to repeatedly run a given section of code. We loop from 1 to that number, for instance, to verify each student's grade in the class.
What loop to print the numbers in different program?Change the condition such that it evaluates to false after the increment expression has executed ten times if you want the loop to run ten times. A loop is repeated ten times. The condition evaluates to false after ten times.
You could use nested loops, the inner one being the loop you already constructed inside, and the outer for loop to instruct it to execute five times. That'd repeat it five times.
Therefore, One inner loop to count from 0 to the last element of the array, and one outside loop to count from 1 to 5.
Learn more about loop here:
https://brainly.com/question/14685092
#SPJ1
How do you expand a small window?
Answers
Answer: Get a new one...
Explanation: Use your brain...
ttl value was set to 64 at the beginning, what is the value of the ttl once it reaches its destination?
Answers
Each time an Internet Protocol (IP) packet passes through a router or gateway, the Time-To-Live (TTL) field's value is reduced by one. When a packet successfully reaches its destination and the TTL value, which was initially set to 64, is reduced by one, it will have the value 63.
In the event of routing loops or other issues, the TTL field is a time-based value that is used to stop IP packets from being transmitted endlessly. The sender sets the TTL value of an IP packet to a certain value (like 64) before it is sent. The router or gateway reduces the TTL value by one each time the packet goes through it.
The packet is rejected and a "Time Exceeded" message is issued back to the sender if the TTL value drops to 0 before it reaches its destination. As a result, routing loops and other issues that can develop when packets are transmitted endlessly are avoided.
To know more about Time-To-Live (TTL) kindly visit
https://brainly.com/question/16889398
#SPJ4
What property of virtualization allows entire virtual machines to be saved as file that can moved or copied like any other file?
a) Isolationb) Hardware Independencec) Partitioningd) Encapsulation
Answers
The property of virtualization that allows entire virtual machines to be saved as files that can move or be copied like any other file is encapsulation. The correct option is d.
What is encapsulation?Encapsulation is a technique for preventing direct user access to some object components, preventing users from seeing the state values for all of an object's variables.
Because of this, VMs are highly manageable and portable. Like any other software file, a virtual machine (VM) can be copied from one place to another and saved on any storage medium, including storage area networks (SANs) and regular USB flash drives.
Therefore, the correct option is d) Encapsulation.
To learn more about encapsulation, refer to the link:
https://brainly.com/question/29563804
#SPJ1
Of the following similar-sounding items, which one would you likely find on your keyboard?
Answers
Of the following similar-sounding items, which one would you likely find on your keyboard is Caps Lock.
What is a keyboard?
One of the main entry points for a computer is a keyboard. Similar to an electronic typewriter, a keyboard is made up of buttons that can be used to produce letters, numbers, and symbols as well as carry out other tasks. More detailed information and responses to some frequently asked questions concerning the keyboard are provided in the following sections.
More than just typing is possible with a computer keyboard. There are a few more things you can do with a keyboard that is listed below.
Fill either a command line or another CLI with your commands (command-line interface).To complete activities more rapidly, use keyboard shortcuts. As an illustration, press Ctrl+C to copy text and Ctrl+V to paste it somewhere else.To learn more about a keyboard, use the link given
https://brainly.com/question/26632484
#SPJ4
Complete Question
Of the following similar-sounding items, which one would you likely find on your keyboard?
A. Caps Lock
B. Cap Lock
C. Clip Lock
D. Clap Lock
if jose is using routing on his network, he must assign this address to all of the hosts on the network?
Answers
Jose must assign an IP address to each host on the network. This address should be unique and not conflict with any other addresses on the network. The IP address should also be within the same subnet as the router itself.
What is IP address?
An Internet Protocol address (Ip) is indeed a numerical label that identifies a computer network that employs the Internet communication protocol. An example of such an IP address is 192.0.2.1. Identification of the network interface and location addressing are the two primary purposes of an IP address.
A 32-bit number is what the Internet Protocol Version 4 (IPv4) characterises as an IP address. However, a latest version of IP (IPv6), utilising 128 bits for such IP address, was standardised in 1998 in response to the expansion of the Internet and the exhaustion of IPv4 addresses. Deployment of IPv6 has been ongoing that since middle of the 2000s. Human-readable notations are used to write and display IP addresses, such as 192.0.2.1 for IPv4 and 2001:db8:0:1234:0:567:8:1 for IPv6.
To learn more about IP address
https://brainly.com/question/14219853
#SPJ4
which kind of attack exploits previously unknown vulnerabilities in software applications, hardware, and operating system program code?
Answers
The type of attack exploits previously unknown vulnerabilities in software applications, hardware, and operating system program code, it is known as zero-day exploits.
Exploring the Dangers of Zero-Day ExploitsAs technology continues to advance, we are becoming more and more dependent on computers, networks, and other digital systems. As the name implies, these vulnerabilities can be exploited before they are known to the public or before a patch or security update can be applied.
Zero-day exploits are particularly dangerous because they can often go undetected for long periods of time. This gives the attacker a longer window of opportunity to cause damage and steal data or gain access to privileged systems. It also presents a unique challenge for security professionals, who must identify and mitigate the risk before it can cause harm.
Learn mores about the Dangers of Zero-Day Exploits:
https://brainly.com/question/27715022
#SPJ4