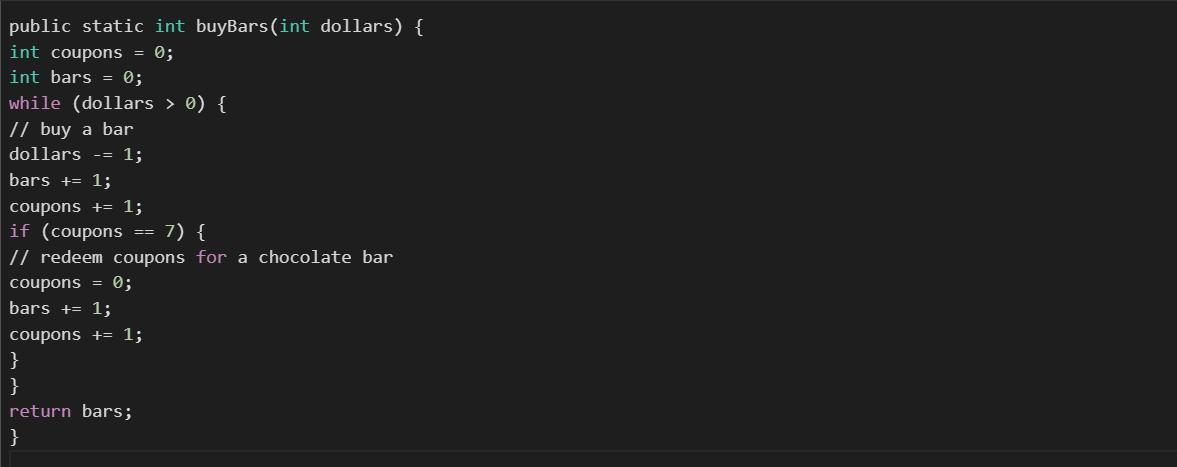
suppose you can buy chocolate bars from a vending machine for $1 each. inside every chocolate bar is a coupon. you can redeem 7 coupons for 1 chocolate bar from the machine. for example, if you have $20, you can initially buy 20 chocolate bars. this gives you 20 coupons. you can redeem 14 coupons for 2 additional chocolate bars. these 2 chocolate bars have 2 more coupons, so you now have a total of 8 coupons. this gives you enough to redeem for 1 final chocolate bar. write a recursive function that would accept the amount of dollars and coupons as its parameters and output the total number of chocolate bars that can be bought (including those redeemed via coupons). write a test program that would allow the user to enter amount of dollars and then use the recursive function to compute the number of chocolate bars the user can buy, and output the number to the screen.
Answers
Using knowledge in computational language in JAVA it is possible to write a code that suppose you can buy chocolate bars from a vending machine for $1 each and inside every chocolate bar is a coupon.
Writting the code:public static int buyBars(int dollars) {
int coupons = 0;
int bars = 0;
while (dollars > 0) {
// buy a bar
dollars -= 1;
bars += 1;
coupons += 1;
if (coupons == 7) {
// redeem coupons for a chocolate bar
coupons = 0;
bars += 1;
coupons += 1;
}
}
return bars;
}
See more about JAVA at brainly.com/question/12975450
#SPJ1
Related Questions
Rfid eliminates the need for manual counting and bar-code scanning of goods at receiving docks.
a. true
b. false
Answers
The statement "RFID eliminates the need for manual counting and bar-code scanning of goods at receiving docks" is a true statement. This is because RFID technology can assist cashiers in scanning codes on products purchased by customers so that their work can be assisted
What is RFID?Radio Frequency Identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a small radio transponder, a receiver and a radio transmitter. When triggered by an electromagnetic interrogation pulse from a nearby RFID reader, the tag transmits digital data, typically an identifier number, to the reader. This number can be used to track goods in stock.
Passive tags are powered by interrogating radio wave energy from an RFID reader. Active tags are battery-powered and can therefore be read at longer distances than RFID readers, up to hundreds of meters. Unlike barcodes, tags do not need to be in the reader's line of sight, so tags can be embedded in the tracked object. RFID is an automated identification and data collection (AIDC) method.
Learn more about RFID https://brainly.com/question/29554696
#SPJ4
working together, it takes two computers 10 minutes to send out a company's email. if it takes the slower computer 35 minutes to do the job on its own, how long will it take the faster computer to do the job on its own?
Answers
It takes the faster computer 70 minutes to do the job on its own.
To solve this problem, we can use the formula for solving for the time it takes two people working together to complete a task:
Time = (Time of slower worker * Number of workers) / (Number of workers - 1)
This formula is based on the idea that the slower worker determines the overall time it takes to complete the task, and the faster worker helps to reduce the overall time. The formula takes into account the time that the slower worker takes to complete the task on their own, as well as the number of workers involved.
In this case, we are given that it takes the slower computer 35 minutes to do the job on its own, and that it takes the two computers working together 10 minutes to send out the company's email. We can plug these values into the formula as follows:
Time = (35 minutes * 2) / (2 - 1)
= 70 minutes / 1
= 70 minutes
Learn more about time here https://brainly.com/question/29733295
#SPJ4
assign isteenager with true if kidage is 13 to 19 inclusive. otherwise, assign isteenager with false.
Answers
The required program is written in C++ that assigns the variable isTeenager with 'true' if the variable 'kidAge' has values between 13 to 19 inclusively; otherwise, assigns 'isTeenager' with 'false'.
#include <iostream>
using namespace std;
int main()
{
bool isTeenager;
int kidAge;
cout << "Enter Kid Age = " ;
cin>> kidAge;
if ((kidAge >= 13) && (kidAge <= 19))
{
isTeenager = true;
}
else
{
isTeenager = false;
}
if (isTeenager)
{
cout << "Teen" << endl;
}
else
{
cout << "Not teen" << endl;
}
return 0;
}
The output of the program is attached below:
You can learn more about C++ programs at
https://brainly.com/question/13441075
#SPJ4
Someone Please help with IT work
When sending personally identifiable information in an email, ______ the message.
A. snail mail
B. label as anonymous
C. encrypt
D. call to relay
A strong password should be at least ____ characters long.
A. 4
B. 3
C. 8
D. 20
I appreciate it thank you
Answers
suppose you have a network with 1,000 routers where each router is connected to 3 other routers on average. (a) if link state routing is used in this network, how many entries a routing update will carry? what information will each entry contain? explain. (4 points)
Answers
The IP ranges inside and outside must be known. I'll only utilize a class A outside range and a class C interior range on the router for this example.
Class B outside and Class C internal addresses are assigned to routers A and B.
The Configuration: Router A, Interfaces 0 and 1 (Int0), and Router B, Interfaces 0 and 1 (Int1) (Int1)
Router A 192.168.0.1 Int0 IP addr Mask 255.255.255.0 Int1 IP addr 10.0.0.1 Mask Add this to the route table for 255.0.0.0:
Routes 0.0.0.0 0.0.0.0 10.0.0.1 and 172.128.0.0 255.255.255.0 and 192.168.0.2 are used.
In either DHCP or static entries, each network device must utilize router A or router B as its default gateway (GW). your direction from here.
Learn more about router here-
https://brainly.com/question/14291670
#SPJ4
if you want to make a fuel cell stack of size 500 w with the stack voltage 20 v, how many fc do you need?
Answers
if you want to make a fuel cell stack of size 500 w with the stack voltage 20 v, you need 100 fuel cells.
What is a fuel cell?In a variety of settings, including transportation, industrial, commercial, and residential buildings, and long-term energy storage for the grid in reversible systems, fuel cells can be used to generate electricity.
Compared to traditional combustion-based technologies, which are still widely used in many power plants and automobiles, fuel cells offer a number of advantages. Compared to combustion engines, fuel cells can operate more efficiently and convert the chemical energy in the fuel directly into electrical energy with efficiencies that can reach over 60%.
Compared to combustion engines, fuel cells emit less or none at all. Because there are no carbon dioxide emissions from hydrogen fuel cells, they can effectively address serious climate challenges. Additionally, the point of operation is free of air pollutants that lead to smog and health issues.
Learn more about fuel cells
https://brainly.com/question/13603874
#SPJ4
true or false: it is more cost effective for a small start-up company to purchase its own server than to pay for a web hosting company's services.
Answers
It is more cost effective for a small start up company to purchase their own server rather than to pay for a web hosting company's services. (Flase)
What is a web hosting company?A web hosting service is a type of Internet hosting service that provides clients with the tools they need to build and maintain websites and makes them available on the World Wide Web. Sometimes, web hosting company that offer web hosting services are referred to as web hosts.
Usually, web hosting calls for the following:
the hosting of the websites by one or more servers; Colocation, which provides physical space, electricity, and Internet connectivity for the server(s), may be physical or virtual;setting up the domain name system to give the websites a name and point them to the hosting server(s);running on the host is a web server;Learn more about web hosting
https://brainly.com/question/16193666
#SPJ4
The methods defined in the custom queue class are identical to the ones in the queue class in the python standard library.
a. True
b. False
Answers
The given statement is true in that the methods defined in the custom queue class are identical to the ones in python's standard library queue class.
The queue class represents a first in first out (FIFO) strategy. The queue class supports the usual enqueue and dequeue operations, along with methods for peeking at the top item, checking if the queue is empty, getting the number of items in the queue, and iterating over the elements in FIFO order. In Pythons standard library, there is also available a queue class that is the same as the one implemented as a custom queue class. There fore, the given statement reflects a true statement.
You can learn more about queue at
https://brainly.com/question/29738296
#SPJ4
How to Fix ""Your PHP Installation Appears to Be Missing the MySQL Extension Which Is Required by WordPress"" Error?
Answers
Update WordPress, Check your PHP version, Ensure the MySQL extension is installed, Verify that the PHP extension is properly configured.
What does a computer install?Making a computer software (including peripherals and plugins) ready for use involves installing (or setting up) the application. Installation is the process of specifically configuring hardware or software so that it may be used with a computer.
How do I install a device?This occurs when the user plugs on (or explicitly installs) a Plug- and-Play (PnP) device, as well as when the system boots for all currently connected devices. Windows is able to identify the devices that are there thanks to drivers like the ACPI driver as well as other PnP bus drivers.
To know more about Installation visit:
https://brainly.com/question/13267432
#SPJ4
you have a user who cannot connect to the network. what is the first thing you could check to determine the source of the problem?
Answers
The first thing you could check to determine the source of the problem when you have a user who cannot connect to the network is Connectivity. It is using routers, switches, and gateways as well as other devices is one approach to linking diverse network components to one another.
Simple issues like a modem, router, or network cable that is loose or unplugged might occasionally cause an internet connection to drop. Your computer's wireless network interface card can be off if you're connected to a wireless network. Check your Wi-Fi settings first by going to Settings > Network & Internet > Wi-Fi, and then turn Wi-Fi on. Check the settings that switch Wi-Fi on and off to make sure it's turned on before browsing from your phone or tablet.
Check the Ethernet cables that connect to your router for wired connections. Try replacing any problematic cables with fresh ones or switching ports if you have any suspicions that they are to blame.
The device's port or interface could be physically down or malfunctioning, which would prevent the source host from being able to interact with the destination host.
To learn more about network click here:
brainly.com/question/6497546
#SPJ4
a thread (say tb) signals completion of some task by setting a memory variable done to 1. another thread (say ta ) waits for completion of the task. can this be achieved safely without using condition variables?
Answers
The solution instructs threads to test a condition, and if it is satisfied, the threads sleep.
The wait subroutine's return value does not necessarily indicate whether the predicate is true or false. It is advised to contain a condition wait in a "while loop" that verifies the predicate. The scheduler can decide which of the several threads that are awaiting the same condition variable should be woken up (assuming that all threads have the same priority level). All threads that are blocked on the supplied condition variable at the time of the call are unblocked by the cnd broadcast() function.
Learn more about condition here-
https://brainly.com/question/14619759
#SPJ4
how to set new password for spectrum wireless router sagemcom fast 5285 advanced home wifi 6 router sax1v1s
Answers
You can a special network name and an alphanumeric password to protect your home wireless router. You can do this action on Spectrum.net or the My Spectrum App.
What is wireless router?The hardware that Internet service providers use to link you to their cable or xDSL Internet network is known as a wireless router and is frequently found in homes. Combining the networking capabilities of a wireless access point and a router, a wireless router, also known as a Wi-Fi router, performs both tasks.
Local networks are connected to one another or to the Internet by routers. The 900 MHz, 2.4, 3.6, 5, and 60 GHz radio frequency bands are used by a wireless access point to wirelessly connect devices to the network. The IEEE 802.11ac Wave 2 standard, frequently abbreviated as Wave 2, is the foundation for the most recent wireless routers.
As a WLAN (wireless local area network) device, a wireless router is sometimes referred to. Similarly, a Wi-Fi network is a wireless network.
Learn more about wireless router
https://brainly.com/question/29243900
#SPJ4
A favorably adjudicated background investigation is required for access to classified information.t/f
Answers
A favorably adjudicated background investigation is required for access to classified information is true statement.
What is background investigation?Background assessments, also known as background investigations, look into a candidate's professional, criminal, and personal histories to assess their behavioral dependability, honesty, and personal growth. The background investigation will involve checks of the applicant's credit and criminal histories, records checks to confirm the citizenship of family members, and verification of the applicant's birthdate, academic credentials, employment history, and military service.
Learn more about background investigation: https://brainly.com/question/29937527
#SPJ4
lansing company’s current-year income statement and selected balance sheet data at december 31 of the current and prior years follow.
Answers
The net cash that is provided by operating activities is $17780.
How to calculate the net cash?The net cash that is provided by operating activities will be calculated thus:
Cash flow from operating activities
Net income = $6000
Adjustment to reconcile net income to net cash
Depreciation expense = $12000
Account receivable = $5800 - $5600 = $200
Inventory increase = $1540 - $1980) = $-440
Prepaid insurance = $280 - $260 = $20
Prepaid rent increase = $180 - $220 = $-40
Salaries payable increase = $880 - $700 = $180
Utilities payable increase = $220 - $160 = $60
Account payable decrease = $4400 - $4600 = $-200
The net cash that is provided by operating activities will be:
= $6000 + $11780
= $17780
The net cash is $17780.
Learn more about net cash on:
brainly.com/question/25716101
#SPJ1
which command adds a rule to the linux netfilter firewall that prevents incoming ping packets from being processed?
Answers
The command that adds a rule to the linux netfilter firewall that prevents incoming ping packets from being processed is iptables -A INPUT -p icmp -j DROP
The iptables -A INPUT -p icmp -j DROP command is valid syntax for adding a network filter rule that prevents incoming ping packets from being processed.
What is the name of the firewall built into most Linux distributions?Linux has a built-in firewall called iptables. This is an easy-to-use program that allows you to configure the tables provided by the Linux kernel firewall. The default firewall installed by Red Hat, CentOS, Fedora Linux, and other distributions is iptables.
What are Linux firewall rules?A firewall creates a barrier between trusted and untrusted networks. A firewall works by defining rules that control both allowed and blocked traffic. A firewall utility developed for Linux systems is iptables.
Learn more about Linux firewall :
brainly.com/question/13025207
#SPJ4
What are the 3 attributes of information?
Answers
As previously said, the three highly important qualities of validity, accuracy, and completeness can be expanded into the information quality of integrity.
For information to be valuable and to meet the definition of information, it must largely have the characteristics of relevance, availability, and timeliness. Accuracy, completeness, consistency, distinctiveness, and timeliness are five qualities of high-quality information. For information to be accurate and valuable, it must be of high quality. Standard attributes, commonly referred to as global attributes, work with a wide variety of elements. The essential attributes such as accesskey, class, contenteditable, contextmenu, data, dir, hidden, id, lang, style, tabindex, and title are included in them.
Learn more about information here-
https://brainly.com/question/5042768
#SPJ4
a server operates with 80% utilization. the coefficient of a server operates with 80% utilization. the coefficient of variation for the service process is 0.5 and the coefficient of variation of the arrival process is 1. the average processing time is 3 minutes. what is the average time a customer spends in the system according to the single-server queue model? for the service process is 0.5 and the coefficient of variation of the arrival process is 1. the average processing time is 3 minutes. what is the average time a customer spends in the system according to the single-server queue model?
Answers
For the Single-server queue model:
average time = 3 ×(0.8/(1 - 0.8) ×((1 + (0.5 ×0.5))/2) = 7.5 minutes.
So, average time= PROCESSING TIME ×(utilization/(1 - utilization) ×((1 + (coefficient of variation ×coefficient of variation))/2)
Where utilization=80%=0.8, Processing time in minutes =3 and
coefficient of variation=0.5
It is the simplest queue is a line of customers, where the person at the front of the line gets served by a single server before leaving, and new customers join the back of the line as they arrive.
Physical or virtual, a single queue is the easiest sort of queue to understand. When everyone in a line is waiting for the same thing, they are more efficient and generally easier to set up than many queues.
Simple enough to be widely published, single-server waiting line models allow for the mathematical derivation of predicted waiting times, expected numbers of tasks awaiting servicing, and time and number in the entire system. It is also possible to calculate the ratio of working to idle time spent by the system.
To learn more about single-server queue model click here:
brainly.com/question/15024311
#SPJ4
what is a proxy? a. a standard that specifies the format of data as well as the rules to be followed during transmission b. a simple network protocol that allows the transfer of files between two computers on the internet c. a standard internet protocol that provides the technical foundation for the public internet as well as for large numbers of private networks d. software that prevents direct communication between a sending and receiving computer and is used to monitor packets for security reasons
Answers
An intermediary proxy server serves as your connection to the internet. End consumers are separated from the websites they visit by an intermediary server.
What is the purpose of a proxy?Proxies are frequently used for system optimization, such as load balancing and caching comparable requests for faster response times, as well as information security against threats. They can handle authentication requests and act as a firewall.
What kind of proxy would that be?Some proxy servers consist of a collection of programs or servers that obstruct popular internet services. An SMTP proxy, for instance, intercepts email, whereas an HTTP proxy intercepts online access. An organization's single IP address is shown to the internet through a proxy server using a network addressing system.
To know more about proxy here:
brainly.com/question/14403686
#SPJ4
What are the 3 types of software security?
Answers
The security of the software itself, the security of the data handled by the software, and the security of networked connections with other systems are the three types of software security.
The security of the software itself, the security of the data handled by the software, and the security of networked connections with other systems are the three types of software security. Computer antivirus, network security, SaaS security, content management systems, e-commerce software, payment gateway software, content delivery networks, bot mitigation, and monitoring tools are some of the security software categories for business websites.
Learn more about security here-
https://brainly.com/question/5042768
#SPJ4
What dimension focuses on the way that smart products are equipped with computing power that enables autonomous decision-making and self-learning processes based on algorithms?
Answers
Intelligent dimension looks at how products can become smarter by being equipped with computing power, which allows them to make decisions and learn by themselves using algorithms. Correct answer: letter B.
For, The intelligent dimension studies how products can become smarter if they are endowed with computing power and artificial intelligence capabilities. Through algorithms, products can learn from their experiences, identify patterns and make decisions autonomously.
How Artificial Intelligence is Transforming Products: A Look at the Intelligent DimensionIn recent years, technological advancement has enabled products to become increasingly intelligent. This new dimension of technology is known as the intelligent dimension.
The smart dimension is revolutionizing the world of products, as, they can react to various external factors, such as weather, time of day, user behavior and others. This means that products can respond to user needs more efficiently, more accurately and more quickly.
In the CapGemini IOT Industry 4.0, What dimension focuses on the way that smart products are equipped with computing power that enables autonomous decision-making and self-learning processes based on algorithms?
A) Connected
B) Intelligent
C) Responsive
D) Aware
Learn more about the Intelligent Dimension:
https://brainly.com/question/28862426
#SPJ4
as a penetration tester, you want to improve your password cracking speed by building a specialized system with multiple video boards installed. which tool can take advantage of multiple gpus for password cracking?
Answers
There are many ways an account. Password cracking is one of them, and it entails using various computational and other approaches to get past the password authentication procedure.
This essay will discuss a variety of password cracking techniques. Nowadays, you might even come across specialized password cracking tools that aren't only designed to be harmful. Before we go into the intricacies, let's first define what password cracking is. Password cracking is the technique of recovering passwords from a computer or from data that a computer transmits. This doesn't have to be a difficult method. In order to crack a password, a brute-force strategy that looks at every possible combination is also used.
Learn more about transmits here-
https://brainly.com/question/28643101
#SPJ4
you have ten servers in your datacenter running windows server and linux. you recently performed performance monitoring tests and found that you have two high-performance windows servers that are underutilized with respect to processing, memory and storage. you have several other lower performance servers that are running windows server and linux on older hardware that is out of warranty and is becoming unreliable. using your existing resources, what can you do to better utilize the high performance servers while being able to retire the older servers?
Answers
Install a bare-metal virtualization product on the high-performance servers and transfer the workload of the older servers to VM.
How do I check the performance of a server in Windows?Select Start > Run from the Wind ows taskbar. In the Run dialogue box, type perfmon, and then click OK. In Performance Monitor, enter: Expand Data Collector Sets in the left-hand panel.
Gathering Windows Server Performance Monitor Information
Select Make data logs.
Check the Performance counter box.
Next, click.
How do I check the performance of a Linux server?top - Monitor process activity.... vmstat - Virtual memory statistics.... w - Determine who is logged in and what they are doing.
ps - Displays the Linux processes. ... free - Show Linux server memory usage. ...\siostat - Montor Linux average CPU load and disc activity. ...
sar - This programme monitors, collects, and reports on Linux system activity.
learn more about linux visit:
brainly.com/question/15122141
#SPJ4
sometimes it is necessary to use untrusted self-signed certificates in practice. when might this be the case? what security guarantees would doing this provide?
Answers
Organizations may prohibit the use of self-signed certificates for a variety of reasons, including:
It is trivially simple to generate a certificate's key pair with insufficient entropy, to fail to protect the private key of the key pair appropriately for its use, to invalidate the certificate when it is used, and so on.When a certificate authority should have been used instead of a self-signed certificate.In some cases, a self-signed certificate provides adequate security.
There are several significant limitations to self-signed certificates. The most important of these are:
Certificates that have been self-signed cannot be revoked.Self-signed certificates have no expiration date.However, in some cases, a self-signed certificate may be sufficient, and may even be preferable to a certificate signed by a CA.
To know more about self-signed certificates, visit: https://brainly.com/question/29576482
#SPJ4
you are the administrator of the eastsim domain, which has two domain controllers. your active directory structure has organizational units (ous) for each company department. you have assistant administrators who help manage active directory objects. for each ou, you grant one of your assistants full control over the ou. you come to work one morning to find that while managing some user accounts, the administrator in charge of the sales ou has deleted the entire ou. you restore the ou and all of its objects from a recent backup. you want to configure the ou to prevent accidental deletion. you edit the ou properties, but can't find the protect object from accidental deletion setting. what should you do so you can configure this setting?
Answers
1 ) Edit the properties for each OU to prevent accidental deletion.
2) Remove full control permissions from each OU. Run the Delegation of Control wizard for each OU, granting permissions to perform the necessary management tasks.
What is OU?An organizational unit (OU) is a container that houses users, groups, and computers within a Microsoft Active Directory domain. It is the smallest unit to which an administrator can apply account permissions or Group Policy settings. Multiple organizational units may be contained within one another, but each containing OU's attributes must be distinct from the others. Other domain objects cannot be included in Active Directory organizational units.
"Organizational unit" is frequently abbreviated to "OU" in everyday speech. Even in Microsoft's own documentation, "container" is frequently used in its place. All terms are accepted as being accurate and interchangeable.
The majority of OUs at Indiana University are structured first around campuses, then around departments, and sub-OUs are then distinct divisions within departments.
Learn more about organizational units
https://brainly.com/question/13440440
#SPJ4
bluetooth is a wireless pan technology that transmits signals over short distances among cell phones, computers, and other devices. group of answer choices true false
Answers
True, Bluetooth is a wireless PAN technology that transmits signals over short distances among cell phones, computers, and other devices. The operating range of Bluetooth technology is around 10 meters (30 feet).
It is typical to link two devices when necessary, however, certain devices can simultaneously connect to several other devices. With infrared technology, there is no requirement for a wire or for the devices to be facing one another in order to connect. You could put such a device in your pocket or purse, for instance.
The Bluetooth standard is a widely adopted international standard that is supported by tens of thousands of businesses worldwide. The function of any Bluetooth device specification is standardized by a profile. The following circumstances may result in a shorter maximum communication range.
Between the unit and the Bluetooth device, there is an obstruction like a person, a wall, a piece of metal, etc.Nearby, there is a Wi-Fi access point in use.Nearby, a microwave oven is in operation.To learn more about Bluetooth click here:
brainly.com/question/28258590
#SPJ4
Identify the reaction type for each generic chemical equation. a b → ab: ab → a b: hydrocarbon o2 → co2 h2o: ab cd → ad cb:
Answers
The type for each generic chemical equation is:
A + B → AB is synthesis.AB → A + B is decomposition.Hydrocarbon + O₂ → CO₂ + H₂O is combustion.AB + CD → AD + CB is double displacement.A chemical equation refers to the symbolic that perform of a chemical reaction in the form of symbols and chemical formulas. A chemical equation can also be meant by equations that is use to show chemical formula and symbols to show chemical reactions. The reactants in the chemical equation is located in the left hand side. The products in the chemical equations is located in the right-hand side. The example of chemical equation is 2H₂ + O₂ → 2H₂O.
The missing part in the question is shown below:
Identify the reaction type for each generic chemical equation.
1. A + B → AB:
2. AB → A + B:
3. Hydrocarbon + O₂ → CO₂ + H₂O:
4. AB + CD → AD + CB:
Learn more about chemical reaction here https://brainly.com/question/29039149
#SPJ4
Using the what-if function in excel to make a decision is considered a type of __________.
Answers
Using the what-if function in excel to make a decision is considered a type of forecast and scenario model
In Excel, which function is used for decision making?The IF function is one of the most commonly used in Excel. It enables you to make logical comparisons between a value and your expectations. In its simplest form, the IF function says something like: If the value in a cell is what you expect (true) - do this.
What exactly is an Excel what-if analysis?What-If Analysis is the process of changing the values in cells to see how those changes affect the results of worksheet formulas. Three kinds of What-If Analysis tools come with Excel: Scenarios, Goal Seek, and Data Tables. Scenarios and data tables take input values and generate possible outcomes.
What function is responsible for decision-making?Decision-making is an essential component of modern management. Essentially, the primary function of management is rational or sound decision making. Every manager makes hundreds of decisions, either subconsciously or consciously, as the key component in the role of a manager.
learn more about Excel visit:
brainly.com/question/3441128
#SPJ4
Which values, in order, will complete the table? negative one-half, negative startfraction startroot 2 endroot over 2 endfraction, negative startfraction startroot 3 endroot over 2 endfraction negative startfraction startroot 3 endroot over 2 endfraction, negative startfraction startroot 2 endroot over 2 endfraction, negative one-half one-half, startfraction startroot 2 endroot over 2 endfraction, startfraction startroot 3 endroot over 2 endfraction startfraction startroot 3 endroot over 2 endfraction, startfraction startroot 2 endroot over 2 endfraction, one-half.
Answers
The values [tex]\frac{-1}{2} , \frac{\sqrt{2}}{2} , \frac{\sqrt{3}}{2}[/tex] will complete the table.
What is a table?
A database table is a collection of connected data that is stored in a table format. A table is mainly composed of rows or columns. A table is a group of data components that are organized using a model of vertical columns and horizontal rows in relational databases and flat file databases. A cell is a place where a row and a column cross. Because they store all the data or information, tables are fundamental database objects. The names, e-mail addresses, and phone numbers of a company's suppliers could be kept in a database's Contacts table, for instance.
To learn more about a table, use the link given
https://brainly.com/question/22080218
#SPJ4
Answer:
^^
Explanation:
for the past 10 years, a restaurant has been running a customer loyalty program, rewarding customers with discounts and treats. records of these rewards have been kept in odd notes and multiple spreadsheets used in different ways by various employees who have come and gone over the years. because of this, some customers are not getting their rewards, while others are receiving rewards they have not earned. overall, the restaurant is losing money and business with this program. how can a database management system (dbms) help with this problem?
Answers
A DBMS will help the owners manage the data they already have to run their customer loyalty program more efficiently.
Which of the following is an example of something an information policy might specify?A website's user agreement states that it will keep the browsing history associated with the IP address for an indefinite period of time and reserves the right to sell that information to interested parties.
Which data type is best suited for a field containing customer email addresses?Names and email addresses are always of the string type, whereas numbers can be stored as either a numerical type or as a string because a string is a collection of characters that includes digits.
How would the dashboards you recommend help them achieve their objectives more effectively?A TV dashboard's primary function is to make key goals and metrics visible and understandable. This helps teams stay focused on their objectives and achieve the goals they set out at the start of a business cycle. This effect is unlikely to be achieved by a cluttered dashboard with irrelevant information.
learn more about database management visit:
brainly.com/question/13467952
#SPJ4
he risk of ddos attacks, sql injection attacks, phishing, etc., is classified under which threat category? compliance operational technical strategic
Answers
He risk of DDOS attacks, SQL injection attacks, phishing, etc., is classified under technical threat category. Hence option c is correct.
What is technical threat?Technical threat is defined as modifications' potential effects on a project, system, or overall infrastructure in the event that a deployment does not go as planned. Technical flaws are issues that are purposefully designed into technology.
These databases are the subject of a sort of cybersecurity attack known as SQL injection (SQLi), which uses carefully prepared SQL statements to fool the systems into doing unforeseen and undesirable actions. The attack types that are included are TCP-SYN, UDP Flood, and benign traffic.
Thus, he risk of DDOS attacks, SQL injection attacks, phishing, etc., is classified under technical threat category. Hence option c is correct.
To learn more about technical threat, refer to the link below:
https://brainly.com/question/29644021
#SPJ1