C++assign isteenager with true if kidage is 13 to 19 inclusive. otherwise, assign isteenager with false.public class TeenagerDetector {publicstaticvoidmain (String [] args) {Scannerscnr=newScanner(System.in);booleanisTeenager;intkidAge;kidAge=scnr.nextInt();if ( (kidsAge>13) && (kidsAge<19), {isTeenager=true;}elseif {isTeenager=false;} if (isTeenager) {System.out.println("Teen");}else {System.out.println("Not teen");}
Answers
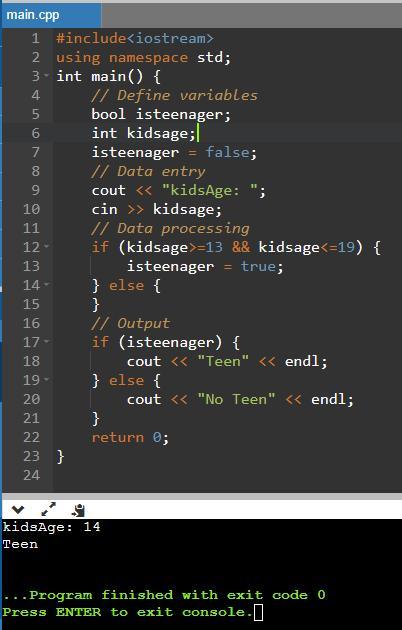
C++ program with simple conditional structures that indicate whether or not you are a teenager based on your age. Below is an output image of the algorithm.
C++ code#include<iostream>
using namespace std;
int main() {
// Define variablesbool isteenager;
int kidsage;
isteenager = false;
// Data entrycout << "kidsAge: ";
cin >> kidsage;
// Data processingif (kidsage>=13 && kidsage<=19) {
isteenager = true;
} else {
}
// Outputif (isteenager) {
cout << "Teen" << endl;
} else {
cout << "No Teen" << endl;
}
return 0;
}
To learn more about conditional structure in C++ see: https://brainly.com/question/27839142
#SPJ4
Related Questions
a standard user attempting to install software or make changes without sufficient permissions places the os in secure desktop mode. what do they need to continue?
Answers
It is to be noted that a standard user attempting to install software or make changes without sufficient permissions places the OS (Operating System) in secure desktop mode. In order to continue, they must enter a User Account Control Password.
What are windows permissions?When you configure permissions, you tell people what they can and cannot do within a folder, such as save and remove files or create new folders. You are not restricted to one of the normal permissions settings (Full Control, Modify, Read & Execute, List Folder Contents, Read, or Write)
User Account Control (UAC) assists enterprises in deploying a better-managed desktop by preventing malware from destroying a PC. Unless an administrator explicitly grants administrator-level access to the system, UAC programs and tasks always execute in the security context of a non-administrator account.
To disable Windows 10 UAC, just turn it off. Note that this technique puts your ecosystem in danger.
Learn more about Windows Permissions:
https://brainly.com/question/29219075?
#SPJ1
There is no ability to check or monitor if your email address was found on the dark web.
a. True
b. False
Answers
The statement " There is no ability to check or monitor if your email address was found on the dark web" is True.
What is the web?
The World Wide Web, or simply "the Web," is an information system that enables users to access papers and other web resources over the Internet. Through web servers, which can be accessed by software like web browsers, documents and downloadable media are made available to the network. Not just scientists had access to the internet before the advent of the world wide web. It unified the globe in a way that facilitated communication, sharing, and information access for everyone. The World Wide Web, sometimes known as the Web, the WWW, or just the Web, is a network of open websites that may be accessed online. The Web is not synonymous with the Internet: it is one of many applications created on top of the Internet.
To learn more about the web, use the link given
https://brainly.com/question/13211964
#SPJ4
double-click the groups folder in the left pane to see a list of groups windows creates. double-click the users group and you see a list of users who are members of the users group, including newguest1. provide the required information true or false? users are prevented from making accidental or intentional system-wide changes and can run most applications.
Answers
Yes, it's true to avoid accidental changes by users, user groups are made. You can see members of the user groups newguest1, special groups like Authenticated Users, and INTERACTIVE, which are internal groups used by Windows.
Users and Administrators are the two built-in groups that are most frequently utilized. You have a high level of privilege on the system and are able to complete practically any job that isn't specifically protected by the operating system if your user account is a member of the Administrators group.
However, if your user account belongs to the Users Group, you are not allowed to install software into the restricted Program Files directory, alter protected areas of the registry, or change the Windows directory. Instead, you can run installed programs and make changes that won't affect the stability of the system. In Windows, the Power Users group was frequently utilized.
To learn more about User groups click here:
brainly.com/question/15500156
#SPJ4
What property of virtualization allows entire virtual machines to be saved as file that can moved or copied like any other file?
Isolation
Hardware Independence
Partitioning
Encapsulation
Answers
Property of virtualization that allows entire virtual machines to be saved as file that can moved or copied like any other file is known as encapsulation
What is encapsulation?Encapsulation describes the concept of encapsulating information and the strategies that perform on that information right into a single unit, like a class in Java. This idea is likewise frequently used to cover the internal representation or state of an object from the outside. This is called information hiding.
The general concept of this mechanism is simple. For example, you've a property that is not visible from outside an object. You bind it to methods that provide read or write access. Encapsulation lets in you to hide specific information and control access to an object's internal state.
Lean more about encapsulation https://brainly.com/question/29107336
#SPJ4
Write a for loop to print the numbers 76, 70, 64, ...34 on one line.
Expected Output
76 70 64 58 52 46 40 34
Answers
A loop is a programming construct that is used to repeatedly run a given section of code. We loop from 1 to that number, for instance, to verify each student's grade in the class.
What loop to print the numbers in different program?Change the condition such that it evaluates to false after the increment expression has executed ten times if you want the loop to run ten times. A loop is repeated ten times. The condition evaluates to false after ten times.
You could use nested loops, the inner one being the loop you already constructed inside, and the outer for loop to instruct it to execute five times. That'd repeat it five times.
Therefore, One inner loop to count from 0 to the last element of the array, and one outside loop to count from 1 to 5.
Learn more about loop here:
https://brainly.com/question/14685092
#SPJ1
a packet of gum, an office cleaning, lawn care maintenance, payroll management, and telecommunications are all examples of what?
Answers
A packet of gum, an office cleaning, lawn care maintenance, payroll management, and telecommunications are all examples of goods and services.
Products or materials are examples of tangible commodities that can be purchased and sold as goods. They are touchable, transportable, and have physical characteristics. Items like a pack of gum, a car, or a piece of furniture are examples of goods.
Services are intangible goods that one party does or offers to another. They are not touchable or graspable since they lack physical attributes. Services can be provided for things like office cleaning, lawn care, payroll administration, and telecommunications.
The two basic types of economic production are goods and services, which are frequently produced and consumed simultaneously. Many businesses produce and sell both goods and services, and consumers often purchase a combination of goods and services in order to meet their needs and wants.
To know more about payroll management kindly visit
https://brainly.com/question/14595534
#SPJ4
a port in what state below implies that an application or service assigned to that port is listening for any instructions?
Answers
Any TCP or UDP service port that receives traffic and provides services at that port address is said to be open.
Virtual points where network connections begin and stop are called ports. Ports are controlled by the operating system of a computer and are software-based. Each port is connected to a distinct procedure or service. Computers can quickly distinguish between different types of traffic thanks to ports: despite using the same Internet connection, emails go to a different port than webpages.
All network-connected devices use the same ports, and each port has a unique number. The majority of ports are set aside for specific protocols; for instance, port 80 is the designated location for all HTTP transmissions. Port numbers enable the targeting of particular services or applications within those devices, whereas IP addresses enable messages to move to and from specific devices.
To know more about Port kindly visit
https://brainly.com/question/10868915
#SPJ4
what is the purpose of an index? group of answer choices increasing the speed of queries increasing the speed of update operations
Answers
An index is a type of data structure that accelerates database update and query operations. In general, the main function of an index is to give a way to rapidly discover specific records in a table without having to browse through the entire table. There are various types of indexes that can be used for different purposes.
Here are several specific methods via which indexes might boost a database's performance:
Speeding up queries: Instead of having to scan the entire table, an index enables the database to quickly find the rows that meet a certain search criterion. By doing this, queries that require to retrieve enormous volumes of data can operate much more quickly.
Enhancing update performance: Update operations, such as inserting, deleting, or updating records, can be made faster by using an index. Instead of having to search through the entire table, the database may rapidly find the records that need to be updated by utilizing an index.
To know more about Index kindly visit
https://brainly.com/question/14297987
#SPJ4
__________ are a part of big data analytics that allow a company the opportunity to analyze location data from mobile phones of employees.
Answers
Location analytics are a part of big data analytics that allow a company the opportunity to analyze location data from mobile phones of employees.
What is location analytics?Location analytics extract additional insights from a business data by adding a layer of geolocation information. Typically used for transactional data such as sales, logistics, and supply chain, this allows for new dimensions that help contextualize specific numbers.
More importantly, we can visualize the flow of goods, sales and deliveries by depth and distance. In general, most of the information generated across industries today already has at least a geographic component. Product route, origin, and point of sale information are already partially used for data classification and segmentation.
Learn more about location analytics brainly.com/question/29422971
#SPJ4
you have a computer that runs windows 10. you use windows backup and restore to create a backup image. you need to perform a complete restore of the computer. what are the possible ways to begin the restore?
Answers
Select Control Panel > System and Maintenance > Backup and Restore by performing a right-click on the Start button. Select Create a system image in the left pane, and then go through the wizard's instructions.
A system image backup on Windows 10 is a dated feature that enables you to make a "full backup" to a USB drive. In other words, a full backup is a copy of the entire system disk and secondary drives (if appropriate), which includes all of the files and settings necessary for the installation of Windows as well as all apps, settings, and files. You can restore Windows 10 in the event of a hard drive failure by using the System Image Recovery tool from the Recovery Drive.
Learn more about system here-
https://brainly.com/question/14253652
#SPJ4
How do you find maximum volume at STP?
Answers
One mole of gas has a 22.4 L volume at STP. 1 mole of any gas will take up 22.4 L of space at Standard Temperature and Pressure (STP).
0°C (273.15 K) and 1 atm of pressure are considered standard temperature and pressure (STP). The volume of one mole of a gas at STP is its molar volume. A mole (6.02 1023 typical particles) of any gas at STP takes up 22.4 L of space. In other words, the gas that has the most moles of a given gas molecule at a given temperature and pressure will take up the most space. We discover that Ar contains the most moles of gasatSTP based on the calculations mentioned above.
Learn more about Calculations here-
https://brainly.com/question/28565438
#SPJ4
Mickey mantle played for the new york yankees for 18 years. Here is the number of home runs by mantle per year: 13, 23, 21, 27, 37, 52, 34, 42, 31, 40, 54, 30, 15, 35, 19, 23, 22, 18 compute the five-number summary of the data and determine which boxplot would best represent the data. A. A box-and-whisker plot. The number line goes from 0 to 55. The whiskers range from 13 to 54, and the box ranges from 15 to 50. A line divides the box at 28. B. A box-and-whisker plot. The number line goes from 0 to 55. The whiskers range from 13 to 54, and the box ranges from 30 to 50. A line divides the box at 40. C. A box-and-whisker plot. The number line goes from 0 to 55. The whiskers range from 13 to 54, and the box ranges from 21 to 37. A line divides the box at 28. D. A box-and-whisker plot. The number line goes from 0 to 55. The whiskers range from 5 to 50, and the box ranges from 10 to 20. A line divides the box at 15.
Answers
Based on these values, the best boxplot to represent the data would be a box-and-whisker plot with the number line going from 0 to 55, the whiskers ranging from 13 to 54, and the box ranging from 21 to 37, with a line dividing the box at 31. Therefore, the correct answer is option C.
A box-and-whisker plot, also known as a box plot, is a type of graphical representation of a dataset that shows the minimum, first quartile, median, third quartile, and maximum of the data. It is a way to visualize the distribution of the data by showing the range, interquartile range, and the symmetry or skewness of the data. Box plots can be useful for comparing multiple datasets or for identifying potential outliers in a dataset. To create a box plot, a horizontal number line is used to represent the range of the data, with the minimum and maximum values marked on the line. A box is then drawn around the middle 50% of the data, with the median marked in the center of the box. The first quartile is marked at the bottom of the box, and the third quartile is marked at the top of the box. Whiskers are then drawn from the bottom and top of the box to the minimum and maximum values, respectively.
The five-number summary of a set of data is the minimum, first quartile, median, third quartile, and maximum of the data. To compute the five-number summary, we first need to sort the data in ascending order: 13, 15, 18, 19, 21, 22, 23, 23, 27, 30, 31, 34, 35, 37, 40, 42, 52, 54.
The minimum of the data is 13, the first quartile is 21, the median is 31, the third quartile is 40, and the maximum is 54.
Learn more about box-and-whisker plot, here https://brainly.com/question/11859288
#SPJ4
write a statement that calls the function addtostock with parameters computerinfo and addstock. assign computerinfo with the value returned.
Answers
A statement that calls the function addtostock with parameters computerinfo and addstock is:
computerInfo=AddToStock(computerInfo,addQty);
What is parameters?In computer programming, a parameter is a particular type of variable that is used to pass data between functions or procedures. Arguments are exchanges of actual information.
The system and the programming language both have rules that govern how arguments are passed to functions. These rules specify whether the arguments will be passed using the stack, machine registers, or any other method.
It details the order of the arguments (from left to right or right to left); whether the arguments will be passed by value or by reference; and other details. Furthermore, only one argument is permitted per function in languages like Haskel and HL; in these languages, extra arguments must be passed through multiple functions.
Learn more about parameters
https://brainly.com/question/13794992
#SPJ4
Which of these should a company consider before implementing cloud computing technology?.
Answers
The options that a company consider before implementing cloud computing technology is is I, II, and III
I: Employee satisfaction
II: Potential cost reduction
III: Information sensitivity
What technology is used in the cloud?In order to bring about quicker innovation, adaptable resources, and scale economies, cloud computing, in its simplest form, is the supply of computing services via the Internet ("the cloud"), encompassing servers, storage, databases, networking, software, analytics, and intelligence.
Therefore, the Steps for Implementing Cloud Computing Successfully are:
Establish the objectives.Determine the current situation.Consider Things Beyond Technology.Start off cautiously.Pick Your Cloud Migration Partner Carefully.Avoid putting all your eggs in one basket.Learn more about computing technology from
https://brainly.com/question/17369247
#SPJ1
See full question below
7. Which of these should a company consider before implementing cloud computing technology. I: Employee satisfaction, II: Potential cost reduction, III: Information sensitivity
• Only I
• Only II
• Only III
• I, II, and III
which type of software license allows a predetermined number of people to use the account at the same time?
Answers
The 'concurrent license' type of software license permits a predetermined number of people to use the account at the same time.
A concurrent license is a type of software license that is based on the maximum number of people who will use the software or account simultaneously. For instance, if an organization purchases five concurrent licenses, it means that up to five number of its employees can use the software at any given time simultaneously; the sixth user is prohibited from the use of this software which is being allowed to use for only the five users. A concurrent license typically deals with software that runs on the server where users connect via the network
You can learn more about concurrent license at
https://brainly.com/question/13502276
#SPJ4
what means fake code, an information description of how the computer program should work? group of answer choices object-oriented language. scripting language. fourth-generation language. pseudocode.
Answers
Pseudocode implies fake code, it is an information description of how the computer program should work.
What do you mean by pseudocode?Whether we're working on apps, data research, or websites, we employ pseudocode in many different programming disciplines. Pseudocode is a technique used to explain the many parts of an algorithm in a way that anyone with a basic understanding of programming can comprehend.
Although pseudocode is a syntax-free description of an algorithm, it must fully describe the logic of the algorithm so that translating from pseudocode to implementation only requires translating each line into code using the syntax of any particular programming language.
Pseudocode can represent the following six programming structures: SEQUENCE, CASE, WHILE, REPEAT-UNTIL, FOR, and IF-THEN-ELSE. These six constructions are always expressed in uppercase.
To learn more about Algorithms refer to:
https://brainly.com/question/24268720
#SPJ1
bill has parkinson's disease and often experiences uncontrollable shaking. bill's lack of control over his motor movements is caused by low levels of the neurotransmitter:
Answers
Bill's lack of control over his motor movements is caused by low levels of the neurotransmitter dopamine.
What is Parkinson's disease?Parkinson's or Parkinsonism is brought on by a decline in dopamine levels in the brain. The most noticeable Parkinson's disease signs and symptoms are when the nerve cells in the basal ganglia of the brain, which control movement, are damaged or killed.
The brain cells that produce dopamine slowly deteriorate because, without it, the cells that regulate movement cannot properly communicate with the muscles.
Therefore, low levels of the neurotransmitter dopamine are the root cause of Bill's inability to control his motor actions.
To learn more about Parkinson's disease, refer to the link:
https://brainly.com/question/13508690
#SPJ1
when does your computer need to know the mac address of a host you are connecting to, how does it determine it?
Answers
Your computer needs to know the MAC (Media Access Control) address of a host when it wants to communicate with that host over a network.
Each device on a network is given a specific identifier called a MAC address, which is used to identify the device and initiate contact with it.
A computer can find the MAC address of a host it wants to connect to in a number different ways. One method is for the computer to broadcast a request over the network for the host's MAC address. All networked devices receive this message, but only the host with the desired MAC address will reply.
A computer can also use the Address Resolution Protocol to find out a host's MAC address (ARP).A computer can use ARP to identify the MAC address of a host based on its IP address when it wishes to interact with a host on the same network.
The MAC address of a host can also be found by a computer by looking up the address in a cache or table of previously known MAC addresses. In order to search up a host's MAC address fast in the future without having to broadcast a message or utilize ARP, a computer caches the host's MAC address when it connects with it.
To know more about MAC (Media Access Control) address kindly visit
https://brainly.com/question/29670807
#SPJ4
we want to save the keys of a bst into an array. then later we want to rebuild exactly the same bst by reading in the keys sequentially from the saved array. describe a way to save the keys systematically.
Answers
To save the keys of a binary search tree (BST) systematically, you can perform a traversal of the tree and save the keys in the order that they are visited. There are several different traversal algorithms that you can use to visit the nodes of a BST in a specific order, such as in-order traversal, pre-order traversal, and post-order traversal.
What is an example of the above?For example, if you want to save the keys of a BST using an in-order traversal, you can perform the following steps:
Start at the root node of the tree and visit the left subtree, saving the keys of the left subtree in the order that they are visited.Save the key of the root node.Visit the right subtree, saving the keys of the right subtree in the order that they are visited.By following this process, you can save the keys of the BST in the order that they would be visited by an in-order traversal, which is known as the "natural" order for a BST. You can then rebuild the BST by reading in the keys from the saved array and inserting them into the tree in the same order that they were saved.
Learn mroe about Binary Search Trees:
https://brainly.com/question/12946457
#SPJ1
which kind of attack exploits previously unknown vulnerabilities in software applications, hardware, and operating system program code?
Answers
The type of attack exploits previously unknown vulnerabilities in software applications, hardware, and operating system program code, it is known as zero-day exploits.
Exploring the Dangers of Zero-Day ExploitsAs technology continues to advance, we are becoming more and more dependent on computers, networks, and other digital systems. As the name implies, these vulnerabilities can be exploited before they are known to the public or before a patch or security update can be applied.
Zero-day exploits are particularly dangerous because they can often go undetected for long periods of time. This gives the attacker a longer window of opportunity to cause damage and steal data or gain access to privileged systems. It also presents a unique challenge for security professionals, who must identify and mitigate the risk before it can cause harm.
Learn mores about the Dangers of Zero-Day Exploits:
https://brainly.com/question/27715022
#SPJ4
How do you expand a small window?
Answers
Answer: Get a new one...
Explanation: Use your brain...
ttl value was set to 64 at the beginning, what is the value of the ttl once it reaches its destination?
Answers
Each time an Internet Protocol (IP) packet passes through a router or gateway, the Time-To-Live (TTL) field's value is reduced by one. When a packet successfully reaches its destination and the TTL value, which was initially set to 64, is reduced by one, it will have the value 63.
In the event of routing loops or other issues, the TTL field is a time-based value that is used to stop IP packets from being transmitted endlessly. The sender sets the TTL value of an IP packet to a certain value (like 64) before it is sent. The router or gateway reduces the TTL value by one each time the packet goes through it.
The packet is rejected and a "Time Exceeded" message is issued back to the sender if the TTL value drops to 0 before it reaches its destination. As a result, routing loops and other issues that can develop when packets are transmitted endlessly are avoided.
To know more about Time-To-Live (TTL) kindly visit
https://brainly.com/question/16889398
#SPJ4
What does authoritarian mean? ruling authority is granted to individuals by the government ruling by aristocracy requiring acknowledgment of authorship requiring strict obedience to an authority, such as a dictator
Answers
Answer:
Authoritarian means requiring strict obedience to an authority, such as a dictator.
In what ways can the different forms of communication be enhanced with the aid of technology.
Answers
Technology can enhance the communication by making it faster.
How technology affects communication?Technology has changed everything in modern society. The way we communicate has been revolutionized by the advancement of new innovations in the telecommunications industry. Easily connecting with others is more possible in today's world, and that's because of the speed.
Centuries ago, books and newspapers reigned as the only choice of communication. Later, innovators brought radio and television before innovation took off with the arrival of the personal computer. With each new innovation, reliance on books as a means of mass communication continues to decrease. Over time, human culture has come to understand the forces and mechanisms involved in technology and invention. In today's world, information has permeated cycles of change and development.
Learn more about technology in communication https://brainly.com/question/18680753
#SPJ4
which utility is used to prepare computers for imaging by removing specific information, such as the computer name and computer sid?
Answers
The utility that is used to prepare computers for imaging by removing specific information, such as the computer name and computer sid, is known as Sysprep.
Microsoft Windows operating systems come with an utility called Sysprep that is used to get a system ready for imaging or cloning.
The computer name, the security identification (SID), and other system-specific data are all removed from the system when Sysprep is executed on the machine. This eliminates conflicts and issues and enables the system to be imaged or cloned and distributed to other computers.
System administrators and other IT experts frequently utilize Sysprep to get systems ready for deployment in a big environment. When setting up a new network or adding new systems to an existing one, it can be used to create a standard image that can be quickly deployed to numerous computers, which can save time and effort.
To know more about Imaging kindly visit
https://brainly.com/question/29347554
#SPJ4
Write a program that reads a list of words. Then, the program outputs those words and their frequencies (case insensitive).
Answers
The program str= input (''Enter a sentence: reads a list of words. The program then outputs those words and their frequencies
Example Input: hey Hi Mark hi mark
Example Output: hey
1
Hi 2
Mark 2
hi 2
Mark 2
PROGRAM
1
str=input("Enter a sentence:
")
2
3
4
#conver the string to lower case
str_cpy=str.lower
5
6
words-str_cpy.splitO
7
8
9
#dictionary to store the frequency
freq-{z
10
11 for word in words:
12
if word in freq:
13
freg word]=freg word]+1
14
else:
15
freq[word]=1
16
17 #split the original string
18 original=str. splitO
19 for i in range(len(original)):
20
print("% %d"%(original[i],freq[wordsLi]]))
To learn more about the program
https://brainly.com/question/14368396
#SPJ4
) why did intel stop using numbers (286, 386, etc.) to identify their processors, and switch to using names (pentium, itanium, etc.)?
Answers
Intel stopped using numbers (such as 286, 386, etc.) to identify their processors and switched to using names (such as Pentium, Itanium, etc.) for a number of reasons.
The numerical naming approach had became complicated and challenging for consumers to understand, which was one reason for the move. Consumers found it more difficult to decide which processor was the most powerful or best suited for their needs as the variety of processor models grew.
Another reason was that using names helped Intel to better distinguish its CPUs from one another and to explain to customers the benefits of each model. Intel could highlight the distinctive qualities of each processor and establish a stronger corporate identity by employing names.
Finally, using names gave Intel additional flexibility and the ability to adjust to shifting market conditions. Intel could more readily release new models and phase out older ones if they had names.
To know more about Processors kindly visit
https://brainly.com/question/28902482
#SPJ4
7. after the disk partition is first formatted, the beginning of a free space bitmap looks like this: 1000 0000 0000 0000 (the first block is used by the root directory). as we discussed during the lecture, the system always searches for free blocks starting at the lowest numbered block, so after writing file a, which uses six blocks, the bitmap would change to 1111 1110 0000 0000... . show the bitmap after each of the following actions: a) file b is written, using five blocks; b) file a is deleted; c) file c is written, using eight blocks; d) file b is deleted. (5 points)
Answers
File B is written, using five blocks 1111 1111 1111 0000 is the disk partition is first formatted, the beginning of a free space bitmap.
What is free space bitmap?Free space bitmap is defined as one technique some file systems employ to keep track of allocated sectors. The bitmap's key benefit is that it can quickly and accurately locate both the initial free block and subsequent free blocks on the disk.
File A is deleted 1000 0001 1111 0000
File C is written, using eight blocks 1111 1111 1111 1100
File B is deleted. 1111 1110 0000 1100
Thus, file B is written, using five blocks 1111 1111 1111 0000 is the disk partition is first formatted, the beginning of a free space bitmap.
To learn more about free space bitmap, refer to the link below:
https://brainly.com/question/23910641
#SPJ1
upon import, you notice the column headings are number instead of the field name but row 1 had the correct names, what should you do?
Answers
When importing in Spreadsheets, we see that the column headings are numbers, not field names, but row 1 has the correct names, all we have to do is Double click on each column name and rename the column (D).
Definition of SpreadsheetsSpreadsheet is a computer program that is used to store, display, and process data in the form of rows and columns. Rows usually use the number labels 1,2,3 and so on.
While columns use alphabetic labels such as A, B, C, and so on. Data processing in a spreadsheet is stored in a cell. The cell naming corresponds to the use of labels in the columns and rows used, for example A1, A2, A3 and so on.
The definition of a spreadsheet itself is tables on a computer that contain rows and columns that can be used to manipulate and organize data. The meeting between rows and columns is called a cell.
Each cell contained in the spreadsheet is very closely related and interrelated. So when one cell is changed, the other cells will also change.
Number processing is the meaning of the word spreadsheet itself, because the spreadsheet functions to process the numbers contained in the cells.
Complete Question:
a. Remove Row 1 and I will make it the column names
b. Start the query over because you did something wrong
c. Select the Use First Row as Headers option
d. Double click on each columin name and rename the column
Learn more about Spreadsheets at: brainly.com/question/26919847
#SPJ4
What is the first step of integrating security in the SDLC?
Answers
Answer: Gathering requirements and analysis.
Explanation: