You wrote a program where the computer's choices changed based on experience and used a list to store the
options.
options = ["rock", "paper", "scissors"]
Finish the code to randomly select one of the options for the computer's play.
compPlay options[randint(__,___)]
Answers
Using the knowledge in computational language in python it is possible to write a code that computer's choices changed based on experience and used a list to store the options.
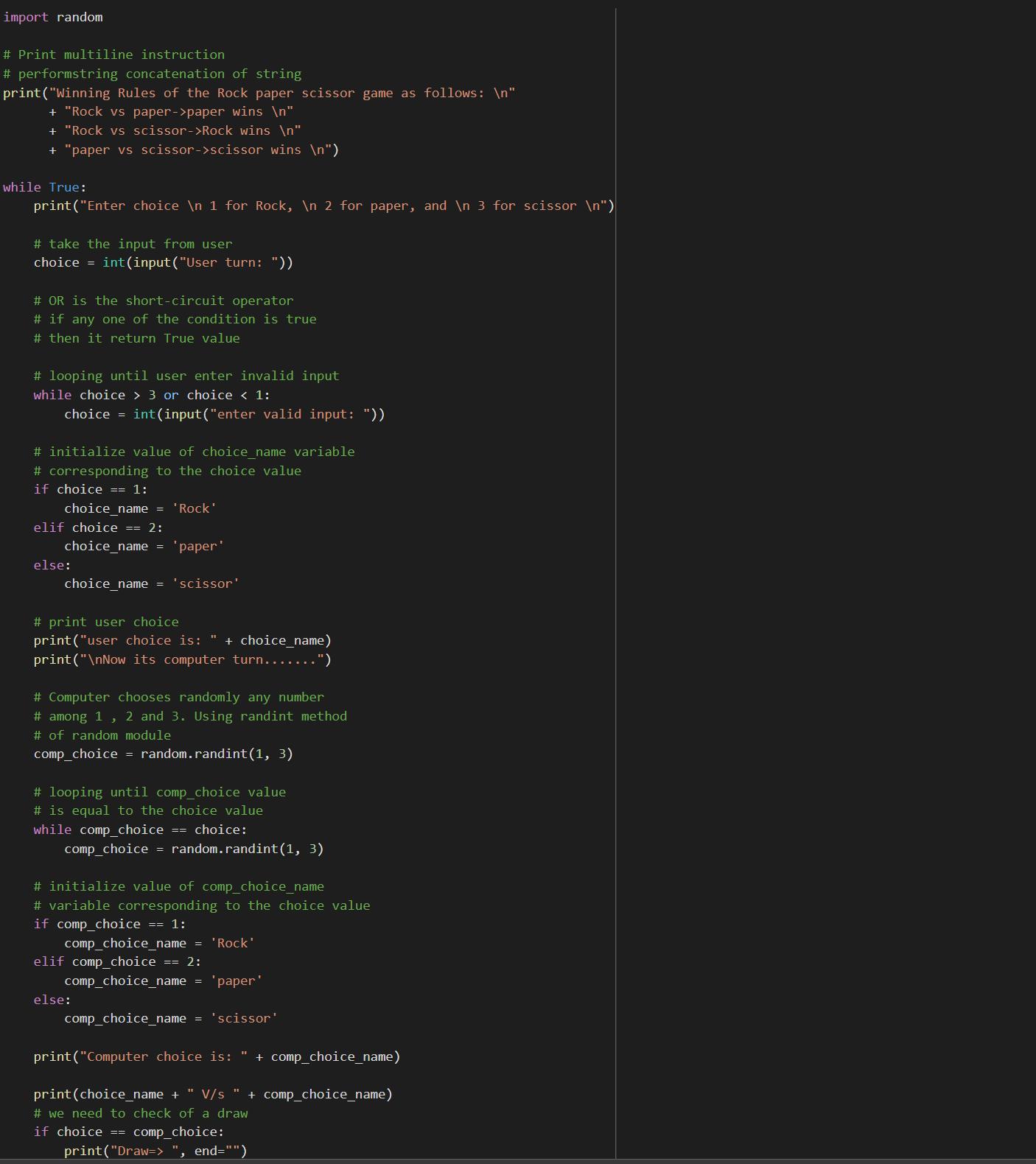
Writting the code:import random
# Print multiline instruction
# performstring concatenation of string
print("Winning Rules of the Rock paper scissor game as follows: \n"
+ "Rock vs paper->paper wins \n"
+ "Rock vs scissor->Rock wins \n"
+ "paper vs scissor->scissor wins \n")
while True:
print("Enter choice \n 1 for Rock, \n 2 for paper, and \n 3 for scissor \n")
# take the input from user
choice = int(input("User turn: "))
# OR is the short-circuit operator
# if any one of the condition is true
# then it return True value
# looping until user enter invalid input
while choice > 3 or choice < 1:
choice = int(input("enter valid input: "))
# initialize value of choice_name variable
# corresponding to the choice value
if choice == 1:
choice_name = 'Rock'
elif choice == 2:
choice_name = 'paper'
else:
choice_name = 'scissor'
# print user choice
print("user choice is: " + choice_name)
print("\nNow its computer turn.......")
# Computer chooses randomly any number
# among 1 , 2 and 3. Using randint method
# of random module
comp_choice = random.randint(1, 3)
# looping until comp_choice value
# is equal to the choice value
while comp_choice == choice:
comp_choice = random.randint(1, 3)
# initialize value of comp_choice_name
# variable corresponding to the choice value
if comp_choice == 1:
comp_choice_name = 'Rock'
elif comp_choice == 2:
comp_choice_name = 'paper'
else:
comp_choice_name = 'scissor'
print("Computer choice is: " + comp_choice_name)
print(choice_name + " V/s " + comp_choice_name)
# we need to check of a draw
if choice == comp_choice:
print("Draw=> ", end="")
result = Draw
# condition for winning
if((choice == 1 and comp_choice == 2) or
(choice == 2 and comp_choice == 1)):
print("paper wins => ", end="")
result = "paper"
elif((choice == 1 and comp_choice == 3) or
(choice == 3 and comp_choice == 1)):
print("Rock wins =>", end="")
result = "Rock"
else:
print("scissor wins =>", end="")
result = "scissor"
# Printing either user or computer wins or draw
if result == Draw:
print("<== Its a tie ==>")
if result == choice_name:
print("<== User wins ==>")
else:
print("<== Computer wins ==>")
print("Do you want to play again? (Y/N)")
ans = input().lower
# if user input n or N then condition is True
if ans == 'n':
break
# after coming out of the while loop
# we print thanks for playing
print("\nThanks for playing")
See more about python at brainly.com/question/18502436
#SPJ1
Answer:
(0,2)
Explanation:
I took the test!
Related Questions
in recursion, what is the term to describe when the new stack frames for these recursive function calls extend beyond the allocated space in the stack?
Answers
in recursion, stack overflow is the term used to describe when the new stack frames for these recursive function calls extend beyond the allocated space in the stack.
What are stack frames?
Some computer languages generate and get rid of temporary variables using a stack frame, a memory management approach. To put it another way, it could be thought of as the accumulation of all data related to a subprogram call that is present on the stack. The runtime process is the only time that stack frames exist.
The local variables and function calls of the function are stored on the stack, one of the application memory segments. In our software, the stack frame is where other function calls or subroutines are placed as well as the memory for the local variables whenever a function is called.
To learn more about stack frames, use the link given
https://brainly.com/question/9978861
#SPJ4
Ava, a system administrator, configures 45 remote access clients to use the VPN server in the organization using the SSTP protocol. On any day, the number of users that work remotely does not exceed 15, so AVA configures the SSTP VPN protocol for 25 connections on the server. One day, owing to extreme weather, many employees are asked to work from home. When more than 25 users try to connect to the organization's servers, they are not allowed access. Ava uses the Routing and Remote Access tool to increase the number of connections for the SSTP protocol to 45. When she asks these additional users to confirm if they have received access, the users tell her that they are unable to connect to the organization's servers.
Required:
If some or all of these users were able to remotely connect on a previous occasion, what is the most likely issue in this scenario?
Answers
After the most recent updates, the remote access server was not rebooted, the most likely problem in this circumstance if some or all of these users were able to remotely connect in the past.
Rebooting is the act of purposefully or unintentionally restarting a previously operational computer system. Warm reboots, in which the system restarts while still powered on, and cold reboots, in which the power to the system is physically turned off and back on, are the two types of reboots. The reboot is known as a restart when the operating system closes all running programmes and completes all pending input and output tasks before beginning a soft reboot. Early electrical computers lacked an operating system and had limited internal memory. The input was often a Switch Register or a stack of punch cards. On systems using cards, turning on the computer was accomplished by pressing a start button, which issued a single command.
Learn more about rebooted from
brainly.com/question/13869329
#SPJ4
with respect to expanding opportunities for ict environmental contributions, what term is associated with the issues such as leed certified buildings, smart motors, and industrial robots?
Answers
In regard to expanding opportunities for ICT environmental contributions, the term 'automation' is associated with the issues such as Smart Motors, Industrial Robots, and LEED Certified Buildings.
In the context of ICT environmental contributions, the term automation refers to the method of designing software and systems to replace repeatable processes and reduce actions of manual intervention. Automation accelerates the delivery of applications and ICT infrastructure by automating manual steps that previously required a human touch. In today's technologically advanced era, automation has contributed largely in order to addressing the issues related to Smart Motors, Industrial Robots, and LEED Certified Buildings.
You can learn more about automation at
brainly.com/question/28126452
#SPJ4
write a function f to c that accepts a temperature in degrees fahrenheit and returns the temperature in degrees celsius. the equation is
Answers
The formula used to convert between Fahrenheit and Celsius is °C = 5/9(°F - 32). The temperature in Fahrenheit can be readily converted to Celsius using the Fahrenheit to Celsius method (F to C formula).
This math tells us that 37.78 degrees Celsius is equal to 100 degrees Fahrenheit.
temp = input("Input the temperature you like to convert? (e.g., 45F, 102C etc.) : ")
degree = int(temp[:-1])
i_convention = temp[-1]
if i_convention.upper() == "C":
result = int(round((9 * degree) / 5 + 32))
o_convention = "Fahrenheit"
elif i_convention.upper() == "F":
result = int(round((degree - 32) * 5 / 9))
o_convention = "Celsius"
else:
print("Input proper convention.")
quit()
print("The temperature in", o_convention, "is", result, "degrees.")
Learn more about method here-
https://brainly.com/question/18088056
#SPJ4
Layton is retired and sells hand-crafted fishing rods as a home-based business for a little extra spending money. because he processes less than a dozen credit card payments per year, he does not need to worry about pci compliance requirements for handling his customers’ payment information.
a. Trueb. False
Answers
It is False that Layton does not need to worry about PCI compliance requirements for handling his customers’ payment information as for his home-based business uses less than a dozen credit card payments per year.
When receiving, sending, processing, and storing credit card data, organizations are required to adhere to a set of 12 security standards known as PCI compliance, or payment card industry compliance. PCI compliance demands that small firms manage firewalls, maintain antivirus software, assign unique IDs to each employee with computer access, and encrypt cardholder data.
The PCI Security Standards are managed by the Payment Card Industry Security Standards Council, an independent organization established by the card networks in 2006. The card networks and payment processors are responsible for enforcing these standards. No matter how many card transactions are performed, every merchant needs to be PCI compliant.
To learn more about PCI compliance click here:
brainly.com/question/28335079
#SPJ4
you have been asked to install a wi-fi network in a building that is approximately 100 meters long and 25 meters wide. because of cost considerations, you will be using 802.11ac. at a minimum, how many wireless access points will you need?
Answers
For 802.11ac, wireless access points(AP) are three. Wi-fi network coverage is up to 150 feet indoors; the range can be affected by building materials and other factors as well.
Requirements for capacity/throughput per user/application Knowing the user count will help with improving the above coverage estimates. When the location is intended for a high number of users, such as lecture halls, auditoriums, and stadiums, estimating the access point count using the number of people or devices is preferable.
For instance, a large sports arena with a rectangle-shaped seating bowl and 80,000 people has dimensions of 650 feet by 750 feet. An access point can easily cover 10,000 square feet thanks to outdoor WiFi signal dispersion, but we'll go with the more typical figure of 1600 square feet per access point from earlier. 487,500 square feet / 1600 = 305 access points when calculating coverage alone.
To determine the necessary AP when developing a WiFi project, one need to be aware of the following:
Area of Coverage and Floor PlanArea's dimensions and floor planMaterial for buildings or wallsUsers in numberTo learn more about 802.11ac click here:
brainly.com/question/18370953
the series of fibonacci numbers contains the sequential values of 610 and 987. what is the next number in this series? 1,419 1,364 1,597 1,633 1,264
Answers
The next number in the sequence would be 1,597.
What is sequence?
Sequence is the order in which things occur. It is an arrangement of events, objects, or ideas in a specific order. For example, when you count from one to ten, you are following a sequence. Events in a story can also be arranged in a sequence. In mathematics, sequences are sets of numbers that follow a pattern. In music, a sequence is a progression of notes, chords, or tones. In biology, a sequence refers to the order of nucleotides in a gene. Sequence is used to organize information and make it easier to understand.
The next number in the series of Fibonacci numbers is 1,597. This is because the Fibonacci sequence is a series of numbers where each number is the sum of the two numbers before it. So, the next number in the sequence would be 610 + 987 = 1,597.
To learn more about sequence
https://brainly.com/question/28644020
#SPJ4
PLEASE HELP THIS IS SERIOUS 1000 POINTS!!!!!!! ALSO GIVING BRANLIEST!!!!!!!!
You are doing an Internet search for vegetarian recipes. One Web site you visit is called "Don't Be an Animal Murderer." What is the likely primary goal of this Web site? to entertain the viewer to provide clear, balanced, and unbiased information about the topic to sell a product to persuade or change the thinking or actions of others
Answers
To persuade or change the thinking or actions of others.
Answer: D. to persuade or change the thinking or action of others
This is 100% correct
Explanation:
explain the important differences between a. a function call and system call b. execution of a regular function vs execution of the main() function of a process c. a context switch and a mode switch
Answers
Function calls belong in user mode, whereas system calls belong in kernel mode. When the main calls another function, execution control is passed to the called function, causing execution to start at the function's first statement.
Although the terms "system call" and "function call" are frequently used interchangeably, they have different meanings. While function calls are used to call a specific function within the program, system calls are used when a program wants to communicate with the kernel.The source program's functions carry out one or more particular tasks. To complete their respective roles, the main function can invoke these functions. Execution starts at the first statement in the function when main calls another function, passing execution control to the function. When a return statement is executed or the function's end is reached, a function returns control to main.A "mode switch" takes place within a single process. There are multiple processes involved in a context switch (or thread, or whatever). A context change does not always indicate a mode change (could be done by the hardware alone).To learn more about system call click here:
brainly.com/question/13440584
#SPJ4
the arguments supplied to the if function, in order, are the condition for execution:_____.
Answers
The arguments written in the 'IF' function, in order, refer to the condition for execution: the result if the condition is true, and the result if the condition is false.
The 'IF' function is one of the most popular functions in MS Excel that allows for making logical comparisons between a value and what the result is expected. Hence, the 'IF' function can have two results. The first result is if the condition or comparison is true, and the second result is if the condition or comparison is false.
The syntax for the 'IF' function is as follows: IF(logical_test, value_if_true, [value_if_false]). Thus, the arguments supplied to the 'IF' function, in order, are the condition for execution: the result if the given condition is true, and the result if the given condition is false.
You can learn more about 'IF' function at
https://brainly.com/question/20497277
#SPJ4
compare and contrast the value between onboard capture systems and down-linking data systems. why are such systems usually not mandated on private general aviation aircraft?
Answers
The value between onboard capture systems and down-linking data systems is Widespread aircraft are usually misunderstood as the simplest, lightest, small-engine commercial aircraft,
Widespread aircraft are usually misunderstood as the simplest, lightest, small-engine commercial aircraft, but even huge jets and transport aircraft operating under federal aviation regulations are not as well-known aircraft.
Why are such systems usually not mandated on private general aviation aircraft?
Well-known Aviation (GA) is defined by global commercial airlines as all civil aviation operations other than scheduled air services and non-scheduled flights for compensation or employment. This means that although military and air operations do not fall under the GA umbrella, they do so broadly.
What is a statistics hyperlink gadget?Datalink refers to virtual air/floor communications among plane and floor systems. The European data link gadget is primarily based totally at the Aeronautical Telecommunications Network (ATN) the usage of interconnected routers and give up systems, and VHF Digital Link Mode 2 (VDL Mode 2/VDL2), because the air/floor statistics hyperlink technology.
Learn more about data link system :
brainly.com/question/9871051
#SPJ4
In a certain country telephone numbers have 9 digits. The first two digits are the area code (03) and are the same within a given area. The last 7 digits are the local number and cannot begin with 0. How many different telephone numbers are possible within a given area code in this country?.
Answers
The possible different numbers of telephone is 9,000,000.
How to calculate possible different number?Since, the first two digits is same, so totally only 7 digits that can be change to create possible different numbers.
Number that available for first from 7 digits is only 9 number (1 to 9) and for the rest digits is 10 number (1 to 10). Since, no restriction to repeat number in any 7 digits available. So we can calculate with this combinator formula,
Possible different numbers = 9 * 10 * 10 * 10 * 10 * 10 * 10
= 9,000,000
Learn more about digits here:
brainly.com/question/10661239
#SPJ4
you are assigned to destroy the data stored in electrical storage by degaussing. you need to ensure that the drive is destroyed. what should you do before degaussing so that the destruction can be verified?
Answers
Before degaussing, the data should be erased. You have been given the task of degaussing the data kept on electrical storage.
How does degaussing work?Degaussing is the process of minimizing or getting rid of an undesired magnetic field (or data) recorded on tape and disk media, such as hard drives in computers and laptops, diskettes, reels, cassettes, and cartridge tapes.
What types of material can a degausser safely obliterate?Therefore, all audio, video, and data signals are entirely erased from magnetic storage media using a degausser. This method works well in a variety of fields, including data security, broadcast, computer, audio, and video.
To know more about degaussing visit:-
https://brainly.com/question/14571079
#SPJ1
Configuring a firewall to ignore all incoming packets that request access to a specific port is known as ____.
Answers
Answer: Logical Point Blocking
Explanation:
Which of these statements are true about the software testing cycle? Check all of the boxes that apply.
Answers
All of the statements that are true about the software testing cycle include the following:
A. It involves inputting sample data and comparing the results to the intended results.
B. It is an iterative process.
C. It includes fixing and verifying code.
What is SDLC?In Computer technology, SDLC is an abbreviation for software development life cycle and it can be defined as a strategic methodology that defines the key steps, phases, or stages for the design, development and implementation of high quality software programs.
In Computer technology, there are seven (7) phases involved in the development of a software and these include the following;
PlanningAnalysisDesignDevelopment (coding)TestingDeploymentMaintenanceIn the software testing phase of SDLC, the software developer must carryout an iterative process in order to determine, fix and verify that all of the errors associated with a particular software program is completely attended to.
Read more on software development here: brainly.com/question/26324021
#SPJ1
Complete Question:
Which of these statements are true about the software testing cycle? Check all of the boxes that apply.
It involves inputting sample data and comparing the results to the intended results.
It is an iterative process.
It includes fixing and verifying code.
It does not require testing the fix.
assume that you are using persistent http to access a webpage. in addition to the basic html file, the html file refers to 4 images, 2 audio clips, and 1 video clip at the same web server. the round trip time between web browser and the web server is rtt. what is the total response time for the web browser to have all objects? (ignore file transmission time.)
Answers
The total response time for the web browser to have all objects would be the sum of the response times for each individual object. In this example, the total response time would be 1000 ms.
In this example, if the RTT between the web browser and the web server is 100 ms, and each of the four images has a size of 50 KB, the total response time for the web browser to download all of the images would be 400 ms (100 ms x 4 images). Similarly, if the two audio clips have a combined size of 100 KB and the video clip has a size of 200 KB, the total response time for the web browser to download all of the audio clips and the video clip would be 600 ms (100 ms x 6 objects).
Therefore, the total response time for the web browser to have all objects would be the sum of these two response times, which would be 1000 ms (400 ms for the images + 600 ms for the audio clips and video clip).
Learn more about the total response time, here https://brainly.com/question/14226496
#SPJ4
Select the correct answer. Which important design element indicates that posters have proper visual balance of text and graphics? A- order B- focus C- visual grammar D-grid E- graphics
Answers
A key design component shows that posters have the right visual balance of text and pictures.
What design components specifically focus on visuals?The foundational aspects of a product's aesthetics include line, shape, negative/white space, volume, value, color, and texture. These are known as the elements of visual design. The principles of design, on the other hand, explain how these components can and should work together for the optimal outcomes.
What elements and principles of the artistic process are used in the creation of a poster's graphic design?Posters for each of the seven design principles—contrast, rhythm, unity, emphasis, pattern, movement, and balance—as well as the seven design elements—illustrate and explain value, color, form, shape, line, space, and texture.
To know more about posters visit:-
https://brainly.com/question/8242738
#SPJ1
What causes the 'AnyConnect was not able to establish a connection to the specified secure gateway' Error Message?
Answers
Incorrect client settings you may encounter the Any Connect was unable to establish a connection to the specified secure gateway Windows error if the client and VPN connections are configured incorrectly.
What is VPN server?
There are numerous causes of common issues like Cisco AnyConnect VPN Login Failed. The most frequent root cause of this issue is the VPN client's failure to connect to the VPN server.
Among the causes of this include incorrect VPN configurations, firewall configuration issues, or issues with network connectivity. when attempting to access the Campus VPN services through a browser using the Web VPN gateway, the Cisco Any Connect software, or an incorrect or invalid login and password combination.
To learn more about Error Message from given link
brainly.com/question/15349056
#SPJ4
What are the four main attributes of information security?
Answers
Information security is a complex and important topic that is essential to protect confidential data and systems. It involves the control and protection of information through four main attributes:
ConfidentialityIntegrityAvailabilityAccountabilityWhat are the four main attributes of information security?Confidentiality: Ensuring that information is only accessed by authorized personnel and is protected from unauthorized disclosure. Integrity: Ensuring that information is accurate and complete and has not been altered in an unauthorized manner. Availability: Ensuring that authorized personnel have access to the information when they need it.Accountability: Ensuring that those who use the information are identified and can be held responsible for their actions.Learn more about Security System: https://brainly.com/question/14364696
#SPJ4
once you move your company to the aws cloud, which tools will help you with security compliance to ensure that the correct security settings are put into place?
Answers
AWS Trusted Advisor tools will help you with security compliance to ensure that the correct security settings are put into place, once you move your company to the AWS cloud.
You can follow AWS best practices with the advice made by AWS Trusted Advisor. Checks are used by Trusted Advisors to evaluate your account. These audits reveal opportunities for streamlining your AWS infrastructure, enhancing security and performance, cutting expenses, and keeping an eye on service quotas. Then, you can implement the suggestions to maximize the use of your resources and services.
Customers of AWS Basic Support and AWS Developer Support have access to fundamental security checks and service quota checks. All tests, including cost reduction, security, fault tolerance, performance, and service quotas, are available to AWS Business Support and AWS Enterprise Support clients.
With the aid of AWS Trusted Advisor Priority, you may concentrate on the most crucial suggestions for streamlining your cloud deployments, enhancing resilience, and fixing security flaws.
To learn more about AWS click here:
brainly.com/question/29034074
#SPJ4
The methods defined in the custom stack class are identical to the ones in the lifoqueue class in the python standard library.a. Trueb. False
Answers
The methods defined in the custom stack class are identical to the ones in the LIFO queue class in the python standard library. Thus, the provided statement is false.
The stack class represents a last in first out (LIFO) order. Using a stack class, a new item is always added at one end of the stack and an item is removed from that end of the stack only. In Pythons standard library, there also exists a stack class that is identical in implementation to the one defined as a custom stack class. Hence, the given statement pertains to a false statement because it states as that the custom stack class is identical to the ones in the LIFO queue class in the python standard library, rather than stating the LIFO stack class.
You can learn more about stack at
https://brainly.com/question/29480873
#SPJ4
Which function in the random library will generate a random integer from 0 to the parameter value inclusive?
Answers
The random.randint() function in the random library will generate a random integer from 0 to the parameter value inclusive.
Define a library.
A library in computer science is a group of non-volatile materials utilized by computer programs, frequently in the creation of software. Programmers can use a collection of prewritten code called a programming library to streamline processes. This library of reused code often focuses on a small number of widespread issues. A number of generic containers, functions, function objects, generic strings, and streams (including interactive and file I/O), as well as support for several language features, are all provided by the C++ Standard Library.
Several different pre-coded components are typically included in a library. These could be information on configuration, information on assistance and documentation, templates for messages, prewritten code and routines, classes, variables, or type specifications. Libraries can be either static or dynamic/shareable. Either one or both can be used to create a program.
To learn more about a library, use the link given
https://brainly.com/question/29407092
#SPJ4
What are the top three wireless network attacks? Out of these attacks, which one has the capability of causing the most damage? Why? What steps would you take to protect your wireless network?
Answers
The top three wireless network attacks are Man-in-the-Middle (MitM) attack, Denial-of-Service (DoS) attack, and Wireless Jamming attack. Out of these attacks, the Man-in-the-Middle attack has the capability of causing the most damage. This is because a MitM attack enables an attacker to intercept data transferred between two parties, potentially allowing them to access sensitive information, tamper with the data, or even modify their identity.
To protect your wireless network, the following steps should be taken:
1. Use strong encryption for your wireless network.
2. Use a virtual private network (VPN) when accessing public networks.
3. Enable two-factor authentication on all devices connected to the network.
4. Install a firewall and regularly update your router's firmware.
5. Use an intrusion detection system to monitor and detect potential attacks.
6. Disable any services not in use.
7. Change your network's SSID and password regularly.
a workstation was patched last night with the latest operating system security update. this morning, the workstation only displays a blank screen. you restart the computer, but the operating system fails to load. what is the next step you should attempt to boot this workstation? reboot the workstation into safe mode and disable windows services/applications reboot the workstation into safe mode and roll back the recent security update reboot the workstation into safe mode, open regedit, and repair the windows registry reboot the workstation into the bios and reconfigure boot options see all questions back next question
Answers
Answer:
A workstation was patched last night with the latest operating system security update. This morning, the workstation only displays a black screen
Explanation:
what access control model below is considered to be the most restrictive access control model, and involves assigning access controls to users strictly according to the custodian?
Answers
The Mandatory Access Control Model is considered to be the most restrictive access control model and involves assigning access controls to users strictly according to the custodian.
Define the access control model.
The access control paradigm enables you to manage a process's capacity to access secure objects or carry out different system administration duties. The elements of the access control model and their interactions are high-level described in the following areas. Access control applies to both the physical and digital worlds and is used to protect sensitive data.
Companies select one of the four most popular access control models based on infrastructure, security needs, and other factors:
Mandatory Access Control (MAC)Discretionary Access Control (DAC)Role-Based Access Control (RBAC)Privileged Access Management (PAM)To learn more about access control model, use the link given
https://brainly.com/question/29526734
#SPJ4
the goal of what type of threat evaluation is to better understand who the attackers are, why they attack, and what types of attacks might occur?
Answers
The goal of threat modeling is a threat evaluation is to better understand who the attackers are, why they attack, and what types of attacks might occur. The correct option is d.
What is threat modeling?The aim of threat modeling, a structured approach, are to identify security needs, identify security threats and probable vulnerabilities, assess the criticality of those threats and vulnerabilities, and rank remedial options.
Agile threat modeling primarily entails two distinct workshop days with your architectural and development teams, either on-site or remotely.
Therefore, the correct option is d. threat modeling.
To learn more about threat modeling, refer to the link:
https://brainly.com/question/28178975
#SPJ1
The question is incomplete. Your most probably complete question is given below:
a. threat mitigation
b. threat profiling
c. risk modeling
d. threat modeling
ibm has developed an internal network which is connected to the internet but can only be used by their employees for information sharing, communications, collaboration, and web publishing?
Answers
IBM has developed an internal network that is connected to the internet but can only be used by their employees for information sharing, communications, collaboration, and web publishing called INTRANET.
An intranet is a personal network that is exclusive to a specific company. It is intended for usage by a company and those connected to it, including customers, employees, and other authorized individuals. It provides a safe environment for sharing data and information with authorized users.
The staff can be given access to confidential data, databases, links, forms, and apps via the intranet. In order to give access to information and documents within an organization to its employees, it functions like a private internet or an internal website. An exclusive IP Address is used to identify every computer on the network.
It is based on internet protocols (TCP/IP) and is secured by firewalls and other security measures against unauthorized access. The firewall keeps an eye on the incoming and outgoing data packets to make sure no illegal requests are present. Users of the intranet can therefore access the internet, but if they are not permitted, internet users cannot access the intranet.
To learn more about INTRANET click here:
brainly.com/question/13139335
#SPJ4
what makes the use of cs better than prior approaches? does it allow creators to do things easier, faster, or in ways that were impossible before?
Answers
Of course computer science has a better approach than before and allows creators to do things easier and faster. This is because computer science has improved graphics, improved multiplayer play, enabled cloud-based and on-demand play, and the availability of virtual and augmented reality.
What is computer science?Computer science is the study of computation, automation, and information. Computer science spans the theoretical disciplines (algorithms, theory of computation, information theory, automation, etc.) to the practical disciplines (hardware and software design and implementation, etc.). Computer science is generally considered an area of academic study and is distinct from computer programming.
Algorithms and data structures are at the heart of computer science. Theory of Computation is concerned with abstract models of computation and the general class of problems they can solve. The field of cryptography and computer security looks at secure means of communication and avoiding security gaps. Computer graphics and computational geometry deal with image generation. Programming language theory considers different ways of describing computational processes, while database theory is concerned with managing data stores.
Learn more about computer science https://brainly.com/question/20837448
#SPJ4
about _____ percent of adolescents and young adults have reported being cyberbullied or cybervictims.
Answers
Answer: 20%
You're Welcome :D
in which special identity group does a user become a member when the user logs onto a computer locally?
Answers
Interactive identity group become a member when the the user logs onto a computer locally.
The Interactive identity is available to any user who is signed into the local system. Only local users with this identity are able to access a resource. A user is automatically added to the Interactive group whenever they use a certain resource on the machine to which they are presently signed on.
The Active Directory security groups that are listed in the Active Directory Users and Built In containers are comparable to special identity groups. Access control for network resources can be efficiently assigned using special identification groups. You can use unique identity groups to:
Active Directory user permissions should be granted to security groups.Give security groups access rights so they can access resources.To learn more about identity click here
brainly.com/question/13652356
#SPJ4