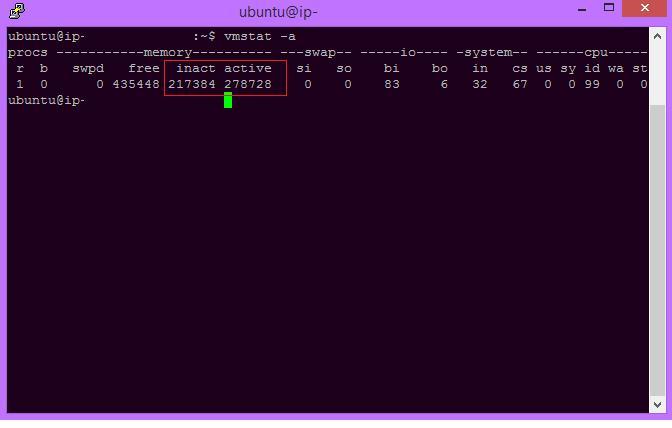
You can display active and inactive memory using the vmstat command with the _________ parameter.
Answers
You can display active and inactive memory using the vmstat command with the -a parameter.
What is vmstat?Vmstat is abbreviation for virtual memory statistics. Vmstat used in as a tool for computer system to monitoring information about system memory, interrupts, processes, paging and block I/O. Vmstat is mostly available in Unix based operating system such as Linux.
Vmstat use parameter command to display information, like -s to display memory statistics and -a to display active and inactive memory.
Attached image for example how to read information display, Inact in vmstat display is for inactive memory that is not being used and active in vmstat display is for active memory that is currently use.
Learn more about vmstat here:
brainly.com/question/29738509
#SPJ4
Related Questions
A few risks that do NOT arise when we connect to the Internet are
A. viruses
B. farming
C. spam
D. stolen PII or credit card data
Pls help i appreciate it
Answers
Answer: Farming
Explanation: That involves using your email also.
what breaks a project into tiny phases, and developers cannot continue on to the next phase until the first phase is complete? group of answer choices extreme programming. agile methodology. waterfall methodology. rad methodology.
Answers
Before moving on to the next phase, the previous phase must be finished. Phases "trickle down" into one another until the application is developed, hence the phrase "waterfall" process.
The rigidity and structure of this methodology hindered the development of software. RUP (Rational Unified Process) offers a framework for segmenting software development into four gates. Inception, development, construction, and transition are the first three gates. The IBM-owned Rational Unified Process (RUP) approach offers a framework for segmenting software development into four "gates." Phases "trickle down" into one another until the application is developed, hence the phrase "waterfall" process.
Learn more about software here-
https://brainly.com/question/985406
#SPJ4
what is worldwide interoperability for microware access (wimax)? group of answer choices includes the inner workings of a wi-fi service or utility, including the signal transmitters, towers, or poles and additional equipment required to send out a wi-fi signal. a metropolitan area network that uses radio signals to transmit and receive data. a means by which portable devices can connect wirelessly to a local area network, using access points that send and receive data via radio waves. a communications technology aimed at providing high-speed wireless data over metropolitan area networks.
Answers
a communications technology aimed at providing high-speed wireless data over metropolitan area networks.
What is WiMAX (Worldwide Interoperability for Microwave Access)?Worldwide Microwave Access Interoperability (WiMAX) A communications technology that enables high-speed wireless data transmission over metropolitan area networks.
What is the Worldwide Interoperability for Microwave Access (WiMAX) range?WiMAX, which stands for Worldwide Interoperability for Microwave Access, is a wireless microwave MAN technology that can deliver up to 1 Gbit/s from up to 30 miles away. WiMAX, also known as IEEE 802.16, is a technology that is similar to Wi-Fi but can provide much higher data transfer rates.
Where can you find Wi-Fi and WiMax?Wireless network connections are created using Wifi and WiMax. Wifi is used to connect printers, computers, and gaming consoles to form small networks. WiMax uses spectrum to connect to networks. WiMax is a technology that is used to provide internet services such as mobile data and hotspots.
learn more about wimax visit:
brainly.com/question/24242279
#SPJ4
you will take the example from the code along where we wrote the employee and productionworker class and modify. in a particular factory, a team leader is an hourly paid production worker who leads a small team. in addition to hourly pay, team leaders earn a fixed monthly bonus, team leaders are required to attend a minimum number of hours of training per year. design a teamleader class that extends the productionworker class we designed together. the teamleader class should have member variables for the monthly bonus amount, the required number of training hours, and the number of training hours that the team leader has attended. write one or more constructors and the appropriate accessor and mutator functions for the class. demonstrate the class by writing a program that uses a teamleader object. these classes were worked on in the week 11 code along if you need to find them.
Answers
The following code contains the use of constructors and the appropriate accessor and mutator functions for the class.
class Employe {
private String name;
private String number;
private String hireDate; // public methods
public Employe(String name, String number, String hireDate) {
this.name = new String(name);
this.number = new String(number);
this.hireDate = new String(hireDate);
}
public String getName() {
return name;
}
public void setName(String name) {
this.name = name;
}
public String getNumber() {
return number;
}
public void setNumber(String number) {
this.number = number;
}
public String getHireDate() {
return hireDate;
}
public void setHireDate(String hireDate) {
this.hireDate = hireDate;
}
public String toString() {
String str = "Empl Name: " + name + "\nEmp Number: " + number + "\nEmp Hire Date: " + hireDate;
return str;
}
}
class ProductionWorker extends Employe {
// private fields
private int shift;
private double hourlyPayRate;
// public methods
public ProductWorker(String name, String number, String hireDate, int shift, double payRate) {
super(name, number, hireDate);
this.shift = shift;
this.hourlyPayRate = payRate;
}
public ProductWorker(ProductWorker productionWorker) {
super(prodionWorker.getName(), productionWorker.getNumber(), productWorker.getHireDate());
this.shift = productWorker.getShift();
this.hourlyPayRate = productWorker.getPayRate();
}
public int getShift() {
return shift;
}
public void setShift(int newShift) {
this.shift = newShift;
}
public double getPayRate() {
return hourlyPayRate;
}
public void setPayRate(double newPayRate) {
this.hourlyPayRate = newPayRate;
}
public String toString() {
String str = super.toString();
str += "\nEmployee Shift: " + shift + "\nHourly Pay Rate: " + hourlyPayRate;
return str;
}
}
class TeamLeader extends ProductWorker {
// private fields
private double monthlyBonus;
private double requiredTrainingHours;
private double completedTrainingHours;
// public method
public TeamLeader(String name, String number, String hireDate, int shift, double payRate, double monthlyBonus,
double requiredTrainingHours, double completedTrainingHours) {
super(name, number, hireDate, shift, payRate);
this.monthlyBonus = monthlyBonus;
this.requiredTrainingHours = requiredTrainingHours;
this.completedTrainingHours = completedTrainingHours;
}
public TeamLeader(TeamLeader tl) {
super(tl.getName(), tl.getNumber(), tl.getHireDate(), tl.getShift(), tl.getPayRate());
this.monthlyBonus = tl.getMonthlyBonus();
this.requiredTrainingHours = tl.getRequiredTrainingHours();
this.completedTrainingHours = tl.getCompletedTrainingHours();
}
public double getMonthlyBonus() {
return monthlyBonus;
}
public void setMonthlyBonus(double bonus) {
this.monthlyBonus = bonus;
}
public double getRequiredTrainingHours() {
return requiredTrainingHours;
}
public void setRequiredTrainingHours(double hours) {
this.requiredTrainingHours = hours;
}
public double getCompletedTrainingHours() {
return completedTrainingHours;
}
public void setCompletedTrainingHours(double hours) {
this.completedTrainingHours = hours;
}
public String toString() {
String str = super.toString();
str += "\nEmployee Monthly Bonus: " + monthlyBonus + "\nRequired Training Hours: "
+ requiredTrainingHours + "\n Completed Training Hours: " + completedTrainingHours;
return str;
}
}
class App {
public static void main(String[] args) {
Employe employee = new Employe("Dominic Giglio", "123-A", "01/25/2022");
System.out.println("\n Basic employee object: ");
System.out.println(employee);
ProductWorker productionWorker1 = new ProductionWorker("Michael Giglio", "456-B", "01/24/2022", 2, 30.00);
ProductWorker productionWorker2 = new ProductionWorker(productionWorker1);
System.out.println("\n Production Worker object:One ");
System.out.println(productionWorker1);
System.out.println("\nT Production Worker object:TWO ");
System.out.println(productionWorker2);
TeamLeader teamLeader1 = new TeamLeader("Katie Proodian", "987-D", "01/10/2022", 1, 15.00, 1500, 100, 50);
TeamLeader teamLeader2 = new TeamLeader(teamLeader1);
System.out.println("\n Team Leader object: one ");
System.out.println(teamLeader1);
System.out.println("\nTeam Leader object two: ");
System.out.println(teamLeader2);
}
}
To learn more about constructors click here:
brainly.com/question/14977765
#SPJ4
information system using the latest information technology has benefited which modern need?
Answers
Information systems using the latest information technology have benefited a lot of today's modern needs, such as education, buying and selling activities, transportation activities, and others.
What is the important role of information technology in everyday life?Most IT professionals work with an organization and technically understand what they need to meet their needs, showing them what current technology is available to perform the required tasks and then their current implementation technology in the setup or by creating an entirely new setup. Information technology in today's world underestimates the scope of the important career field. There is a very unexpected importance of information technology.
A 1958 article published in the Harvard Business Review on information technology includes three basic parts: computer data processing, decision support and business software. Information technology refers to anything related to computer technology, such as networks, hardware, software, the Internet, or the people who work with these technologies.
Learn more about the importance of information technology https://brainly.com/question/13724249
#SPJ4
configuring a firewall to ignore all incoming packets that request access to a specific port is known as ________.
Answers
Configuring a firewall to ignore all incoming packets that request access to a specific port is known as logical port blocking.
Why do ports get blocked? A setting that instructs a firewall to reject any incoming packets that ask for access to a specific port, preventing any unauthorized requests from reaching the machine.The technique of an Internet Service Provider (ISP) recognizing and completely blocking Internet traffic based on its port number and transport protocol is known as "port blocking."If there are appropriate options available for stopping undesirable traffic and protecting customers, ISPs should refrain from port blocking.Additionally, if port blocking is deemed required, it should only be applied to safeguard the network and users of the ISP doing the blocking.A logical port is one that has been programmed.A logical port's function is to enable the receiving device to determine which service or application the data is intended for.To learn more about logical port blocking refer
https://brainly.com/question/6275974
#SPJ4
write an expression that retrieves the value in the location immediately after the location pointed to by the integer pointer variable ip.
Answers
An expression that retrieves the value in the location immediately after the location pointed to by the integer pointer variable ip is *(ip +1).
What is integer pointer variable ip?Int **p declares a stack pointer that points to one or more heap pointers. Each of the pointers points to a heap-based integer or array of integers. When you declare a pointer on the stack and initialize it to point to an array of 100 pointers on the heap, you write int **p = new int*[100];. While *p is the value kept in the memory address pointed by p, p is the value of p. You can have an integer pointer point to the value of an integer I when you want to indirectly access it (int *p = I and then use that pointer to indirectly change the value of I (*p = 10).
Learn more about pointer variable: https://brainly.com/question/28565988
#SPJ4
What are the five primary requirements for patentability?
Answers
A patent must satisfy five requirements: utility, novelty, nonobviousness, patentable subject matter, and enablement.
Utility: Patents can only be granted for practical inventions. This indicates that the thing being patented serves a respectable, precise, and significant purpose. Usefulness must be unique to the product being patented; general utility that covers a wide range of products is insufficient.Novelty: The two components of the novelty requirement are novelty and statutory patentability barriers. Novelty requires that the invention be novel, meaning that it could not have been used or known by others. The statutory restriction stipulates that the patented product must not have been available for purchase or use in the US more than a year before the patent application date.Nonobviousness: Patents need not be evident. If the innovation extends beyond the predictable application of prior art in accordance with its recognized functionalities, the patent claim is not evident.Patentable subject matter: Any process, device, manufacture, composition of matter, or material improvement is considered a patentable subject matter. If it is connected to a physical innovation and is either novel and valuable or new and non-obvious, printed materials may also qualify for patent protection.Enablement: A written description of the product being patented, along with information on how to make and use it, must be included in the patent application in order to satisfy the enablement requirement. Such texts must be thorough, understandable, and succinct so that persons with common artistic ability can duplicate and use the object without needless experimenting. The optimal way to use the invention must also be disclosed in the documents.To learn more about Patents click here:
brainly.com/question/2016241
#SPJ4
write an if-else statement that assigns finalvalue with uservalue 5 if uservalue is greater than 100. otherwise assign finalvalue with
Answers
Answer:
Here is an if-else statement that assigns finalvalue with uservalue + 5 if uservalue is greater than 100. Otherwise, it assigns finalvalue with uservalue - 5.
if uservalue > 100:
finalvalue = uservalue + 5
else:
finalvalue = uservalue - 5
Explanation:
In this statement, we first check if uservalue is greater than 100. If it is, we assign finalvalue with the value of uservalue + 5. Otherwise, we assign finalvalue with the value of uservalue - 5.
This if-else statement provides a simple way to assign a value to finalvalue based on the value of uservalue. If uservalue is greater than 100, finalvalue will be assigned a value that is 5 greater than uservalue. Otherwise, finalvalue will be assigned a value that is 5 less than uservalue.
If Diamond, a corporate recruiter, wants to selectively recruit passive job candidates, she should utilize the LinkedIn social media network.
True or False
Answers
The Linked social media network should be used by corporate recruiter Diamond if she wants to selectively find passive employment applicants.
What would you say is media?A medium's plural form. The forms of communication that have a broad audience or effect, such as radio or television, publications, magazines, and the internet: The address is being covered by the media tonight.
What three sorts of media are there?The terms earned media, owned media, and corporate media may also be used to refer to the three categories of media, which are also referred to as news media, online networks, and digital media.
To know more about Media visit :
https://brainly.com/question/14526554
#SPJ4
Which kind of attack exploits previously unknown vulnerabilities in software applications, hardware, and operating system program code?
Answers
A zero-day type of attack exploits previously unknown vulnerabilities in hardware, software applications, and operating system program code.
A zero-day (0-day) type of exploit is a cyber attack that targets a software vulnerability that is unknown to the software vendor. The cyber attacker spots the software vulnerability before any parties attempt to mitigate it, quickly creates an exploit and uses it for an attack. Zero-day exploit attacks unknown and unprotected vulnerabilities. This novel vulnerability is difficult to detect and defend against, making zero-day attacks a significant threat to organization cybersecurity.
You can learn more about zero-day vulnerability at
https://brainly.com/question/29239283
#SPJ4
What are the 5 layers of security?
Answers
All of these layers of security are essential to ensure the safety and integrity of a network and its resources:
Access controlNetwork securityApplication securityData securityEndpoint securityWhat are the 5 layers of security?Access control is the first layer of security and is used to regulate which users have access to certain resources. Network security focuses on protecting the infrastructure of the network, such as routers and firewalls, from unauthorized access. Application security is used to protect applications from malicious activities and data breaches. Data security focuses on protecting data from unauthorized access, modification, or destruction. Finally, endpoint security focuses on protecting the devices connected to the network, such as computers and mobile devices, from malicious activities.Learn more about Security System: https://brainly.com/question/26260220
#SPJ4
The 5 layers of security:
1. Network Access Control (NAC)2. Data Security3. Application Security4. Endpoint Security5. Identity and Access Management (IAM)The Essential Layers of Security for Securing Your NetworkIn a world where data breaches and cyber-attacks are becoming more and more common, it is essential to ensure that your network is secure. To do this, businesses and individuals must implement the five essential layers of security. These layers are Network Access Control (NAC), Data Security, Application Security, Endpoint Security, and Identity and Access Management (IAM).
Starting with Network Access Control (NAC), this layer of security is designed to protect networks from unauthorized users. NAC allows administrators to set up access control policies which can be used to control who is allowed to access the network and what they are allowed to do while they are on the network. By implementing NAC, businesses and individuals can ensure that only authorized users are accessing their network and that those users are unable to access or modify any sensitive data.
The second layer of security is Data Security. This layer of security is designed to protect data from unauthorized access, modification, or destruction. Data Security involves the use of encryption, authentication, and access control mechanisms to ensure that data is only available to authorized users and that it is safe from unauthorized access.
Learn more about Data Security:
https://brainly.com/question/28004913
#SPJ4
Which type of attack involves an adversary attempting to gather information about a network to identify vulnerabilities?
reconnaissance
DoS
dictionary
man-in-the-middle
Answers
In a reconnaissance attack, the intruder seeks for wireless network vulnerabilities.
What is reconnaissance attack?
Attacks known as reconnaissance are ones that aim to learn more about a system or network of a target company without that organization's knowledge or consent.
Typically, threat actors that are looking for vulnerabilities to exploit are the ones who carry out these attacks.
a. Passive reconnaissance:
The practice of passive reconnaissance involves employing a variety of techniques to learn more about an organization.
These include Wireshark and Shodan, which enable users to both observe what is happening and gather data for later use.
Many times, public resources are used in this kind of surveillance.
b. Active reconnaissance:
Active reconnaissance is quicker and more accurate, but it's riskier because it makes more noise on many systems, which can be picked up by security personnel or administrators.
The attacker must connect to the system in order to do so. This can be anything from social engineering to active fingerprinting.
To know more about Cyber Attack, visit:
https://brainly.com/question/14286078
#SPJ4
write the function declaration or signature for a function called my function that returns an integer value and has three parameters, the first parameter is an integer that is passed by reference, the second parameter is a string, and the third is an integer with default value of 10. you simply need to write the declaration, you do not need to write a function.
Answers
Answer:
int myFunction(int &firstParameter, string secondParameter, int thirdParameter = 10);
what does momentum assist with in training artificial neural networks? what may happen if you set the momentum hyperparameter too close to 1
Answers
Momentum in neural ODEs can reduce the stiffness of the ODE dynamics, which significantly enhances the computational efficiency in training and testing.
What does momentum do in neural networks?
Neural network momentum is a simple technique that often improves both training speed and accuracy. Training a neural network is the process of finding values for the weights and biases so that for a given set of input values, the computed output values closely match the known, correct, target values.
What is the use of momentum in deep learning?
Momentum is a widely-used strategy for accelerating the convergence of gradient-based optimization techniques. Momentum was designed to speed up learning in directions of low curvature, without becoming unstable in directions of high curvature.
If you set the momentum hyperparameter too close to 1 (e.g., 0.99999) when using an SGD optimizer, then the algorithm will likely pick up a lot of speed, hopefully moving roughly toward the global minimum, but its momentum will carry it right past the minimum.
To know more about artificial neural networks:
https://brainly.com/question/27371893
#SPJ4
A computer network that is restricted to the organization it serves; an internal internet.
a. True
b. False
Answers
The statement "A computer network that is restricted to the organization it serves; an internal internet" is a true statement. The internal internet or what is often called an intranet is a computer network that is limited to the organization it serves.
What is Intranet?An intranet is a private network that uses the Internet protocol (TCP/IP), to share confidential company information or activities within the company with its employees. Sometimes, the term intranet refers only to a display service, specifically a company's internal website. To build an intranet, the network must have several components that make up the Internet, namely the Internet Protocol (TCP/IP protocols, IP addresses, and others), clients, and servers. The HTTP protocol and some other Internet protocols (FTP, POP3, or SMTP) are generally the most frequently used protocol components.
In general, an intranet can be understood as a "private version of the Internet" or a version of the Internet owned by an organization.
Learn more about intranet https://brainly.com/question/1032917
#SPJ4
one who performs lockout/tagout on a machine or equipment to do servicing or maintenance is called the:
Answers
One who performs lockout/Tagout on a machine or equipment to do servicing or maintenance is called the Authorized employee. It is a worker who locks or tags machinery or equipment to carry out service or maintenance.
Operators of energy facilities, plumbers, and electricians are a few examples of authorized staff. When an impacted employee's responsibilities include servicing or doing maintenance, that employee becomes an authorized employee.
Tagout is the established practice of attaching a tagout device to an energy-isolating device to signify that operation of the energy-isolating device and the controlled equipment is prohibited until the tagout device has been removed. Lockout is the recognized technique of attaching a lockout device to an energy-isolating device to prevent the operation of the energy-isolating device or the controlled equipment until the lockout device has been removed.
Lockout device is any mechanism that holds an energy-isolating device in a secure place and prevents the energizing of machinery or equipment by using positive means, such as a lock, blank flanges, and bolted slip shutters
To learn more about lockout/Tagout click here:
brainly.com/question/28284754
#SPJ4
using the what-if function in excel to make a decision is considered a type of __________.
Answers
using the what-if function in excel to make a decision is considered a type of forecast and scenario model.
What is the IF function?
One of the most used Exceel functions, the IF function enables you to compare values logically to what you anticipate. Therefore, there are two outcomes that can come from an IF statement. If your comparison is True, the first outcome will be true; if it is False, the second outcome will be true.
There are three elements (arguments) to the syntax of the IF function, one of the logical functions in Microsooft Exceel:
logical test: EVALUATE something, such as the contents of a cell.Value if True: Describe the desired outcome in the event that the test result is TRUE.value if false: Define the action to be taken in the event that the test result is FALSE.To learn more about an IF function, use the link given
https://brainly.com/question/20497277
#SPJ4
A network administrator needs to keep the user ID, password, and session contents private when establishing remote CLI connectivity with a switch to manage it. Which access method should be chosen?
- Telnet
- AUX
- SSH
- Console
Answers
In order to make the mentioned contents private, the access method that should be chosen is SSH. Therefore, option 'C' holds the correct answer.
Secure Shell or SSH is an authentication method for secure remote access over a network. The SSH allows keeping the session contents and other data such as user login information private.
According to the given situation, where a network administrator wants to keep the data such as the user ID, password, and other session contents private when deploying a remote CLI connectivity with a switch to manage it. The most suitable access method should be 'SSH'.
You can learn more about SSH at
https://brainly.com/question/28269727
#SPJ4
measures that are taken to prevent one user's work from inappropriately influencing another user's work are called: select one: a. concurrency control b. checkpoint c. database recovery d. database logging e. interleaving
Answers
A. Concurrency control
Measures that are taken to prevent one user's work from inappropriately influencing another user's work are called concurrency control. Concurrency control prevents data integrity issues.
Concurrent processes can be completely independent of one another but can also interact with each other. Interacting processes require synchronization to be well controlled. Processes are called concurrent if the processes (more than one process) exist at the same time. Concurrent processes can be completely independent of one another but can also interact with each other. Interacting processes require synchronization to be well controlled. Concurrency is a common cornerstone of operating system design. Processes are called concurrent if the processes (more than one process) exist at the same time.
You can learn more about Concurrency control here brainly.com/question/14209825
#SPJ4
Suppose you are playing the Star Trek version of Rock, Paper, Scissors where the choices are rock, paper,
scissors, lizard, and Spock.
The list of options now is larger.
options = ["rock", "paper", "scissors", "lizard", "spock"]
Complete the code for the computer to randomly choose an option.
from random import randint
compPlay = options[randint(_,__)]
Answers
Rock wins over scissors (“rock crushes scissors,” “breaks scissors,” or even “blunts scissors”), but loses to paper (“paper covers rock”); a play of paper (“paper covers rock”) loses to a play of scissors (“rock breaks scissors”) (“scissors cuts paper”).
What is the role of Rock Paper Scissors?In a game of Rock, Paper, Scissors, inexperienced men tend to begin with the rock the majority of the time. You have a better chance of winning if you throw paper at them when you make your first move. According to statistics, the rock move has the highest throw rate (35.4%).
Therefore, It turns out that the most frequent throws are rocks (35%), scissors (35%), and finally paper (25%). (29.6 percent). Confused as to what to do next? You might have a very little advantage by choosing paper.
Learn more about paper Scissors here:
https://brainly.com/question/17286388
#SPJ1
Answer: compPlay = options[randint(0,4)]
A network administrator needs to keep the user id, password, and session contents private when establishing remote cli connectivity with a switch to manage it. which access method should be chosen?
Answers
The SSH access method should be chosen to keep the user id, password, and session contents private when establishing remote CLI connectivity with a switch to manage it.
What is an access method?
A computer's operating system component known as an access method is in charge of preparing data sets and sending them to particular storage locations. Examples from the mainframe world include Indexed Sequential Access Method (ISAM) and Virtual Storage Access Method (VSAM) (ISAM).
Software routines that open files, fetch data into memory, and write data to permanent storage, like a disk, make up an access method. Similar to device drivers in non-mainframe operating systems, access methods offer an application programming interface (API) for programmers to transport data to or from devices, but often offer a higher level of capability.
To learn more about an access method, use the link given
https://brainly.com/question/28334307
#SPJ4
assume x is a one-dimensional int array that was declared and initialized in a java process. also, assume x contains at least one value. would x[x.length] cause an error? if so, then what kind of error?
Answers
Yes, the code shows error like this: Index out of bounds . A correct way to calculate the size of an array would be using the length function. For example, the size of the array "a" is calculated as "x.length". Below is the complete code.
Java Codeimport java.io.*;
public class Main {
public static void main(String args[]) {
int i;
String x[];
x = new String[5];
for (i=0;i<=4;i++) {
x[i] = "a";
}
System.out.println("Array size: " + x.length);
}
}
To learn more about length functions in Java see: https://brainly.com/question/13151204
#SPJ4
What makes the use of cs better than prior approaches? does it allow creators to do things easier, faster, or in ways that were impossible before?
Answers
Computer science has a better approach than before and allows creators to do things easier and faster because computer science has improved graphics, improved multiplayer play, enabled cloud-based and on-demand play, and the availability of virtual and augmented reality.
What is computer science?Computer science, the study of computers and informatics, including the theoretical foundations and algorithms, hardware and software, and how they are used to process information. Computer science includes the study of algorithms and data structures, computer and network design, data modeling and information processes, and artificial intelligence.
Computer science takes some of its foundations from mathematics and engineering and thus incorporates techniques from areas such as queuing theory, probability, and statistics as well as electronic circuit design. Computer science also makes extensive use of hypothesis testing and testing when conceptualizing, designing, measuring, and refining new algorithms, information structures, and computer architectures.
Learn more about computer science brainly.com/question/20837448
#SPJ4
Is Windows a proprietary OS?
Answers
Yes, Windows is a proprietary operating system, as are Adobe Flash Player, iTunes, Adobe Photoshop.
Nonproprietary software is open source and accessible for free download and usage. It also makes its source code completely available. Nonproprietary software is also known as open-source software. The fundamental parts come from the proprietary Unix operating system and the free and open-source software (FOSS) Android Open Source Project (AOSP), Windows which is principally licensed under the Apache License. Although the Unix operating system uses a CLI (Command Line Interface), a GUI for Unix computers has recently been developed. An OS that is popular in businesses, academic institutions, large corporations, etc. is Unix.Under the terms of the GNU General Public License, Linux is a free and open source operating system (GPL). The source code may be used, examined, altered, and distributed by anybody, and they may even sell copies of the altered code.
Learn more about Windows here:
https://brainly.com/question/13502522
#SPJ4
an attacker might use a confidentiality attack such as packet capturing. what common utility might an attacker use to capture packets on a network for further analysis?
Answers
The common utility might an attacker use to capture packets on a network for further analysis is --- Wireshark
Why do hackers use packet sniffers?
An attacker uses a sniffer to intercept his packets of data, including sensitive information such as passwords and account information. A sniffer is a piece of hardware or software installed on your system. By installing a promiscuous mode packet sniffer on your network, a malicious intruder can capture and analyze all network her traffic.
What are the dangers of packet sniffing?Parcel detectors don't read our data for laughs, like a nosy reads someone's personal diary for fun. Steal passwords, account numbers, social security numbers, and more. They want to steal money and ruin the reputation of organizations and individuals.
Do hackers use sniffer devices?Ethical hackers can use sniffing to gain tremendous insight into how a network is performing and the behavior of its users. This can be used to improve your organization's cybersecurity. However, when deployed by malicious hackers, sniffing can be used to launch devastating attacks against unsuspecting targets.
Learn more about Packet sniffer :
brainly.com/question/29607482
#SPJ4
a developer is implementingan apex class for a financial system. within the class, the variables 'creditamount' and 'debtamount' should not be able to change once a value is assigned. in which two ways can the developer declare the variables to
Answers
Two ways can the developer declare the variables to use the final keyword by assigning its value in the class constructor and for other way assign its value when declaring the variable.
The final keyword can be used to change variables. Final variables can only receive a value once, either during the variable declaration process or in a constructor. It needs to have value in one of these two places. Static initialization code or the places where they are defined can affect static final variables. In initialization code blocks, constructors, or with other variable declarations, member final variables can be modified. Make a variable static and final define a constant. To convey the state at the class level, non-final static variables are employed (such as the state between triggers). They are not, however, shared between requests. Classes and methods are by default final. In a class's declaration, the final keyword is not allowed.
To learn more about constructor click here:
brainly.com/question/14701603
#SPJ4
write the definition of a method reverse, whose parameter is an array of integers. the method reverses the elements of the array. the method does not return a value.
Answers
The reverse () method mutates the array and returns a reference to it while transposing the items of the caller array object .
What is Method Reverse?The reverse() function of the Collections class is used to turn elements back around in the object in which they are stored, as the name suggests. The entries of a list supplied as an input are rearranged.The Java built-in method reverse() is used to return the bits' reverse order in the two's complement binary representation of an input value.Parameters: An integer value with its bits reversed makes up the parameter a.Return Value: Reversing the bits in the supplied int value yields the value that the method returns.To learn more about Method Reverse refer to:
https://brainly.com/question/27960232
#SPJ1
How many buttons are there in a mouse name them?
Answers
Answer:
In a classic mouse, there are 3 buttons, left click, right click, and scroll wheel.
Explanation:
If you have a more advanced mouse, however it may have 5 buttons. The 2 new buttons are back and forward. These buttons mainly apply to website where you can go back to the previous page you were on or return to the page you left. This is helpful since you don't have to move your mouse pointer all the way to the top of your screen and so you don't have to use the keyboard shortcuts, which in case you were wondering, is alt + left arrow to go back or alt + right arrow to go forward. There is also another button that you can use by pressing down on the scroll wheel. This button allows you to scroll through the page without having to constantly scroll down.
a computer network that is restricted to the organization it serves; an internal internet.
Answers
The statement "A computer network that is restricted to the organization it serves; an internal internet" is a true statement. The internal internet or what is often called an intranet is a computer network that is limited to the organization it serves.
What is Intranet?Intranet is a computer network for sharing information, easier communication, collaboration tools, operating systems, and other computer services within an organization, often excluding third-party access. The term is used in contrast to public networks, such as the Internet, but uses the same technology based on the Internet protocol suite.
An organization-wide intranet can be an important focal point for internal communication and collaboration, and provides a single starting point for accessing internal and external resources. In its simplest form, an intranet is set up with local area network (LAN) and wide area network (WAN) technologies. Many modern intranets have search engines, user profiles, blogs, mobile apps with notifications and event scheduling in their infrastructure.
Learn more about intranet brainly.com/question/1032917
#SPJ4
The statement above should be accompanied by a question asking whether the statement is true or false