This is to be done in java
Task 1: Write a car class - this is a prototype or blueprint for many different cars that will follow the same basic type of pattern. Your car class should have 4 fields that describe characteristics of a car including model, make, year, color, speed, velocity.
Possible values for each field:
Model: Wrangler, Grand Cherokee, Camry, Corolla, Corvette, Bolt
Make: Jeep, Toyota, Chevrolet
Year: 1946, 2022
Color: red, blue, silver
Speed: 25, 25, 55, 75,100
Task 2: Your car class should also have several methods - assuming it has a rider to do them, the car can have certain behaviors or actions that it can take. Add the methods to accomplish the following:
Set a speed (could take an integer in mph)
Calculate a speed (could take a distance in miles and a time in hours)
Get a speed (in mph)
Task 3: Create a constructor that takes four parameters for your car class and initializes speed to 0.
Write a main method and inside it, invoke a new car object for every person at your table. Print a complete ‘description’ of each car to the console using the System.out.println and toString methods. Each car should be unique, so be creative with the color choice.
Task 4: Agree on the value of and create a speedLimit field for your car class and create two public methods to get and change the value of the speed limit.
Task 5: Draw the UML representation of the class that you have created.
IndividualTask 6: Create a class method that is named isSpeeding that takes as arguments a distance in miles, a time in hours and a Car to determine whether the car is speeding. Ask your colleges how fast they want to go to the beach and determine whether they would be speeding. Assume the beach is 330 miles away.
IndividualTask 7: Draw the UML Diagram for your class.
Answers
Using the knowledge in computational language in python it is possible to write a code that write a car class - this is a prototype or blueprint for many different cars that will follow the same basic type of pattern.
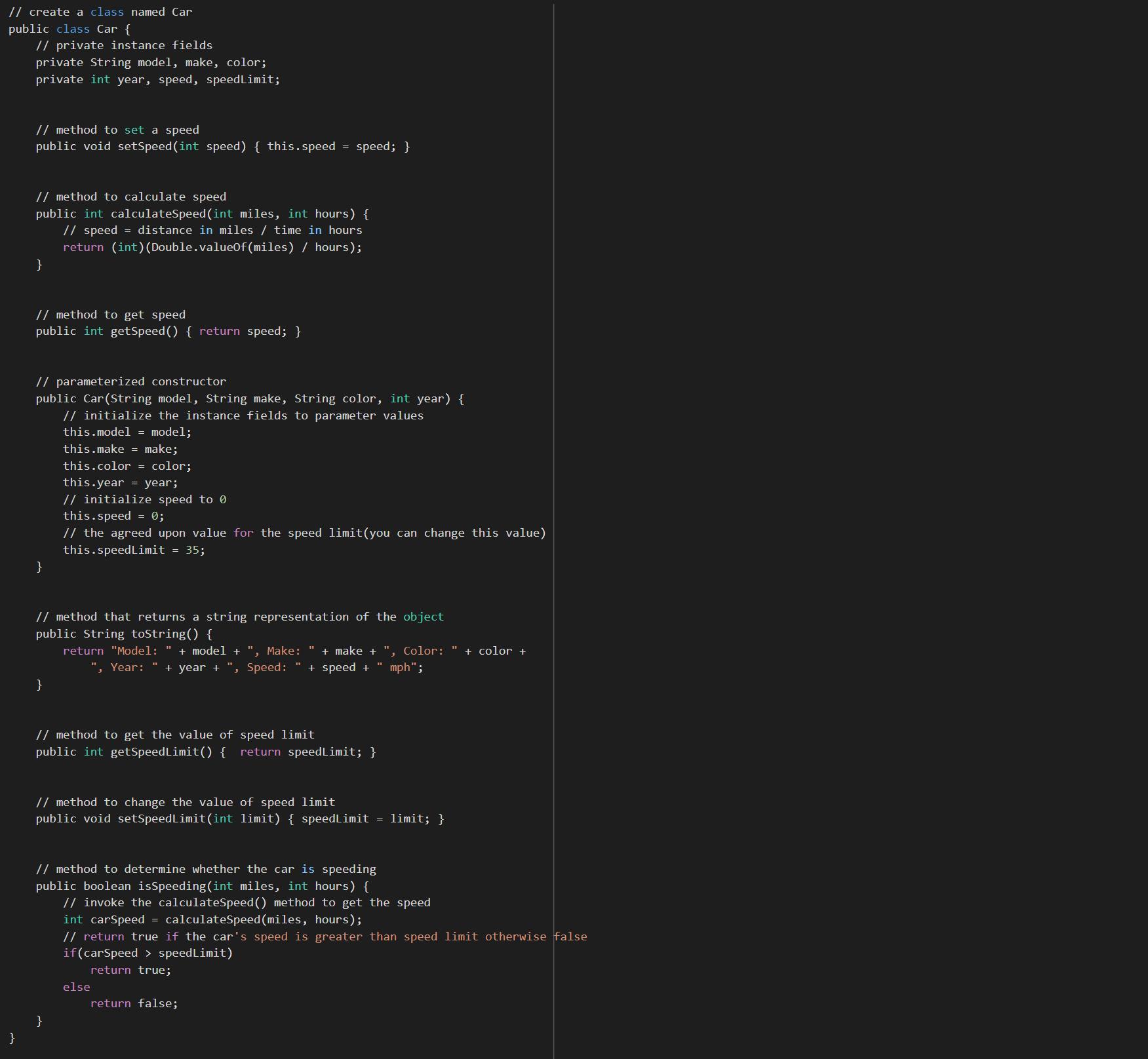
Writting the code:// create a class named Car
public class Car {
// private instance fields
private String model, make, color;
private int year, speed, speedLimit;
// method to set a speed
public void setSpeed(int speed) { this.speed = speed; }
// method to calculate speed
public int calculateSpeed(int miles, int hours) {
// speed = distance in miles / time in hours
return (int)(Double.valueOf(miles) / hours);
}
// method to get speed
public int getSpeed() { return speed; }
// parameterized constructor
public Car(String model, String make, String color, int year) {
// initialize the instance fields to parameter values
this.model = model;
this.make = make;
this.color = color;
this.year = year;
// initialize speed to 0
this.speed = 0;
// the agreed upon value for the speed limit(you can change this value)
this.speedLimit = 35;
}
// method that returns a string representation of the object
public String toString() {
return "Model: " + model + ", Make: " + make + ", Color: " + color +
", Year: " + year + ", Speed: " + speed + " mph";
}
// return true if the car's speed is greater than speed limit otherwise false
if(carSpeed > speedLimit)
return true;
else
return false;
}
}
See more about JAVA at brainly.com/question/18502436
#SPJ1
Related Questions
Discuss how to handle risk management in the DevOps environment.
Answers
To handle risk management in the DevOps environment, accept it, avoid it, and diminish it.
What is a DevOps environment?Embrace it, possibly a highly popular tactic, and prevent it, useless or untested technology should not be used, diminish it. This tactic actively lowers hazards.
It's simple for problems like cross-site scripting (XSS) and SQL injections to make it into code that is produced.
Therefore, deployed if security checks aren't performed as part of the code creation process.
Learn more about DevOps, here:
https://brainly.com/question/29388529
#SPJ1
The Middletown Wholesale Copper Wire Company sells spools of copper wiring for $100 each and ships them for $10 a piece. Write a program that displays the status of an order. It should use two functions.
getOrderInfo (order, stock, specialCharges)
displayStatus( numOrdered, inStock, unitShipChg)
The first function asks for the following data and stores the input values in reference parameters.
The number of spools ordered.
The number of spools in stock.
Any special shipping and handling charges (above the regular $10 rate).
The second function receives as arguments any values needed to compute and display the following information:
The number of ordered spools ready to ship from current stock.
The number of ordered spools on backorder (if the number ordered is greater than what is in stock).
The total selling price of the portion ready to ship (the number of spools ready to ship times $100).
Total shipping and handling charges on the portion ready to ship.
Total of the order ready to ship.
The shipping and handling parameter in the second function should have the default argument 10.00.
Answers
SOLUTION- I have solved the problem in python code with comments and a screenshot for easy understanding :) CODE- # function to get order information from the user and return it def get order info(): order = int(input("How many spools are being ordered.
What is information?Information is a general term for everything with the capacity to inform. Information is most fundamentally concerned with the interpretation of what may be sensed. Any naturally occurring process that is not entirely random, as well as any discernible pattern in any medium, can be said to convey some level of information.
A program that displays the status of an order. It should use two functions. in python code with comments and a screenshot for easy understanding :) CODE- # function to get order information from the user and return it def get order info(): order = int(input("How many spools are being ordered.
Therefore, the information carried by your genes.
Learn more about the information here:
https://brainly.com/question/13629038
#SPJ1
a(n) ____________________________ is a health care provider who enters into a contract with a specific insurance company or program and agrees to accept the contracted fee schedule.
Answers
Answer:
Explanation:
Master policy provider.
What is Master policy provider?
Master policy: A master policy is a single contract for group health insurance provided to the business.
To know more about Insurance policies, visit:
https://brainly.com/question/29042328?referrer=searchResults
Why would someone chose to use lamp over iis
Answers
Answer:
open source
Explanation:
LAMP technology is open source and extremely secure, and it runs on the LINUX operating system.
Why is LAMP technology a popular choice?It provides complete flexibility in building and deploying apps based on your specific business requirements. LAMP technology is safe and reliable. It has a strong security mechanism to prevent vulnerable assaults, and if an error arises, it can be repaired swiftly in a cost-effective manner.The LAMP stack is a versatile option for constructing web infrastructure. Developers can create online content, add dynamic application features, and administer the database.LAMP technology is open source and extremely secure, and it runs on the LINUX operating system. When compared to other software architectural bundles, the LAMP stack is quite inexpensive.To learn more about LAMP technology refer,
https://brainly.com/question/17241979
#SPJ1
Spreadsheet software enables you to organize, calculate, and present numerical data. Numerical entries are called values, and the
instructions for calculating them are called.
Answers
Answer:
It's called coding frame
Creating a company culture for security design document
Answers
Use strict access control methods: Limit access to cardholder data to those who "need to know." Identify and authenticate system access. Limit physical access to cardholder information.
Networks should be monitored and tested on a regular basis. Maintain a policy for information security.
What is a healthy security culture?Security culture refers to a set of practises employed by activists, most notably contemporary anarchists, to avoid or mitigate the effects of police surveillance and harassment, as well as state control.
Your security policies, as well as how your security team communicates, enables, and enforces those policies, are frequently the most important drivers of your security culture. You will have a strong security culture if you have relatively simple, common sense policies communicated by an engaging and supportive security team.
What topics can be discussed, in what context, and with whom is governed by security culture. It forbids speaking with law enforcement, and certain media and locations are identified as security risks; the Internet, telephone and mail, people's homes and vehicles, and community meeting places are all assumed to have covert listening devices.
To learn more about security culture refer :
https://brainly.com/question/14293154
#SPJ1
Which of these is used for long-range wireless communication?
Zig-Bee
LPWAN
Power-Line Communication
HaLow
Answers
Answer:
LPWAN
Explanation:
first thing taught in administrative technology.
Which of the following should be used to enter a word ?
(A) Expo.enterBoolean();
(B) Expo.enterChar();
(C) Expo.enterDouble();
(D) Expo.enterInt();
(E) Expo.enterString();
Answers
Expo.enterBoolean();An expression that may only be evaluated as true or false is called a boolean expression (after mathematician George Boole)
What is an example of a Boolean?An expression that may only be evaluated as true or false is called a boolean expression (after mathematician George Boole).Let's examine some examples in everyday language:Pink is one of my favorite colors.I'm apprehensive about programming computers.It's entertaining to read this book. A boolean value in computer science is one that can either be true or false.George Boole, an English mathematician, gave his name to In Boole's new branch of algebra, now referred to as Boolean Algebra, the value of true is 1, while the value of false is 0. The mathematician George Boole, who published An Investigation of the Laws of Thought in 1854, is the source of the term "Boolean."The branch of mathematics known as boolean algebra works with how to logically describe true and false using the integers 0 and 1.To learn more about Boolean refer
https://brainly.com/question/2467366
#SPJ1
Answer:
Expo.enterInt();
Explanation:
NOTE: The program will crash with a Run-time Error if you enter something that is not an integer like a word or even a real number.
7.10 LAB: Warm up: Parsing strings
(1) Prompt the user for a string that contains two strings separated by a comma. (1 pt)
Examples of strings that can be accepted:
o Jill, Allen
Jill, Allen
Jill, Allen
Ex
Enter input string:
Jill, Allen
k
(2) Print an error message if the input string does not contain a comma. Continue to prompt until valid string is entered. Note If the input
contains a comma, then assume that the input also contains two strings. (2 pts) c++
Answers
The Python code that follows was created. It is a loop that solicits feedback from the user.
What purposes serves Python code?Python is a computer programming language that is frequently used to create software and websites, automate processes, and perform data analysis. Because Python is a general-purpose language, it may be used to develop a wide range of programs and isn't tailored for any particular issues.Two functions in Python can receive data directly from input(). raw input() . A string of data is requested by raw input() from the user.The Python code that follows was created. It is a loop that solicits feedback from the user. If there is a comma in the string, the program removes all whitespace, divides the word into two, prints each word separately, and then ends the loop. If there isn't a comma, the user is prompted for more information.Though True:
input = string
Enter the following string.
if string contains ","
replacing "" with "'" in a string
String.split(',') = string split
"First word:" printed after string split[0]
"Second word:" print("+ string split[1] + "
break.
To learn more about Python refer to:
https://brainly.com/question/28379867
#SPJ1
The following Python code was written. It is a feedback loop that solicits user feedback.
What purposes serves Python code?Python is a computer programming language that is commonly used to create software and websites, automate processes, and analyze data. Python is a general-purpose programming language that can be used to create a wide variety of programs and is not tailored to any specific issues.Python has two functions that can receive data directly from input (). raw input() Raw input() requests a string of data from the user. The following Python code was written. It is a feedback loop that solicits user feedback. If the string contains a comma, the program removes all whitespace, divides the word into two, prints each word separately, and then exits the loop. If no comma is present, the user is prompted for more information.Though True:
input = string
Enter the following string.
if string contains ","
replacing "" with "'" in a string
String. Split(',') = string split
"First word:" printed after string split[0]
"Second word:" print("+ string split[1] + "
break.
To learn more about Python, refer to:
brainly.com/question/28379867
#SPJ1
Identify the operational level of the Purdue model in which the production management, individual plant monitoring, and control functions are defined.
Layer 1
Layer 2
Layer 3
Layer 4
Answers
The operational level of the Purdue model in which production management, individual plant monitoring, and control functions are defined is: Level 3: Manufacturing Operations Systems Zone" (Option C).
What is the Purdue Model?Purdue Enterprise Reference Architectural is an enterprise architecture reference model established in the 1990s by Theodore J. Williams and participants of the Industry-Purdue University Consortium for Computer-Aided Manufacturing.
The Purdue model, which is part of the Purdue Enterprise Reference Architecture (PERA), was created as a reference model for data flows in computer-integrated manufacturing (CIM), which automates all of a plant's activities.
Learn more about the Purdue model:
https://brainly.com/question/4290673
#SPJ1
Which of the following examples does not use descriptive analytics?
A business owner discovering that spring has been the season with the highest sales
over the last 4 years.
A retail store wants to know if it's worth creating a loyal customer discount by seeing
how many repeat customers they had last year.
A non-profit organization using last year's total donations to project next year's total
donations.
Human resources has developed a survey to determine how engaged employees are
currently feeling at the company.
Answers
A charity that predicts its total donations for the following year using the
totals from the previous year.
What is Descriptive analytics?Using descriptive analytics, you can better understand how changes in a firm have changed by analyzing historical data. Decision-makers have a comprehensive understanding of performance and trends on which to base corporate strategy by using a variety of historical data and benchmarking.
Descriptive analytics may use metrics like year-over-year price fluctuations, month-over-month sales growth, user count, or total revenue per subscriber. Predictive and prescriptive analytics, two more recent types of analytics, are now employed in conjunction with descriptive analytics.
The most basic type of data analysis, descriptive analytics, involves summarizing the key elements and traits of a data set. Statistical measures of distribution, central tendency, and variability are used in descriptive analytics.
To learn more about Descriptive analytics refer to:
https://brainly.com/question/6990681
#SPJ9
Create a Raptor program that asks the user for a numerical input. The program then multiplies that number by 10 and outputs the result.
Answers
Using javascript, explanation with javascript comment.
Using flowcharts, users of RAPTOR can create and run programs. Students can learn the fundamental concepts of computer programming using RAPTOR's simple language and graphical elements.
What is the explanation of the program?function guessNumber(){
var randomize= math.random()*10;
var roundrand= math.floor(randomize);
var getInput= prompt("guess number from 1 to 10");
var x= 3;
do(
if(getInput>roundrand){
Console.log("your guess is too high");
guessNumber();
}
if(getInput<roundrand){
Console.log("your guess is too high");
guessNumber();
}
else{
Console.log("you are correct pal!");
break;
}
)
while(x<=3)
}
If the input passes the if condition and the guess is incorrect, the recursive function guessNumber is called one more inside the function definition. Once the user inputs a correct input, the function exits the do... while loop after checking for a correct number three times.
To learn more about programming refer to:
https://brainly.com/question/24222119
#SPJ1
4) Name and describe three benefits that information systems can add to a
company's operations.
Answers
Operating effectiveness. cost savings. providing information to those who make decisions. improved clientele service.
What is information systems?An information system is a coordinated group of parts used to gather, store, and process data as well as to deliver knowledge, information, and digital goods.The purpose of strategic information systems planning is to create plans to make sure that the infrastructure and information technology function serve the business and are in line with its mission, objectives, and goals.Information systems store data in an advanced manner that greatly simplifies the process of retrieving the data. A business's decision-making process is aided by information systems. Making smarter judgments is made simpler with an information system that delivers all the crucial facts.
To learn more about information systems refer to:
https://brainly.com/question/14688347
#SPJ9
Each week, the Pickering Trucking Company randomly selects one of its 30
employees to take a drug test. Write an application that determines which
employee will be selected each week for the next 52 weeks. Use the Math.
random() function explained in Appendix D to generate an employee number
between 1 and 30; you use a statement similar to:
testedEmployee = 1 + (int) (Math.random() * 30);
After each selection, display the number of the employee to test. Display four
employee numbers on each line. It is important to note that if testing is random,
some employees will be tested multiple times, and others might never be tested.
Run the application several times until you are confident that the selection is
random. Save the file as DrugTests.java
Answers
In the Java program provided, a class named Main is formed, and inside of that class, the main method is declared, where an integer variable named "testedEmployee" is declared. The loop is then declared, and it has the following description.
How is a random number generated?RAND() * (b - a) + a, where an is the smallest number and b is the largest number that we wish to generate a random number for, can be used to generate a random number between two numbers. A random method is used inside the loop to calculate the random number and print its value. A variable named I is declared inside the loop. It starts at 1 and stops when its value is 52.The following step defines a condition that, if true, prints a single space if the check value is divisible by 4.In the Java program provided, a class named Main is formed, and inside of that class, the main method is declared, where an integer variable named "testedEmployee" is declared. The loop is then declared, and it has the following description.To learn more about Java program refer to:
https://brainly.com/question/25458754
#SPJ1
Detailed information about each use case is described with a
Answers
A use case is a thorough explanation of how online consumers will utilize it to carry out activities.
What is information?"Information can be defined as the process or the moment of the data that is collected and is being either or taken by the person himself. It is news or that can be used for various things."
A use case is a detailed explanation of how visitors will employ the website to accomplish tasks. It describes how a computer behaves in response to a query from the viewpoint of a user. Every usage case is described as a series of easy actions that start with the user's objective and finish when that objective is achieved.
Learn more about information, here:
https://brainly.com/question/27798920
#SPJ
currentScore = 7
highScore= currentScore
currentScore = 3
(Display highScore)
O 3
O7
O4
O2
Answers
Answer:
the current score is 3 because it says in the guidelines that the current score is 3
In the following expression, identify variables, values, and operators. Evaluate the result of the expression (assume that the value of the variable X is 1).
Variable(s):
Values(s):
Operator(s):
Result of the expression:
Answers
Answer:
The assignment statement creates new variables and gives them values:
>>> message = "What's up, Doc?"
>>> n = 17
>>> pi = 3.14159
This example makes three assignments. The first assigns the string "What's up, Doc?" to a new variable named message. The second gives the integer 17 to n, and the third gives the floating-point number 3.14159 to pi.
The assignment operator, =, should not be confused with an equals sign (even though it uses the same character). Assignment operators link a name, on the left hand side of the operator, with a value, on the right hand side. This is why you will get an error if you enter:
Explanation:
history of computer and generation of computer
Answers
Answer:
computing evolution
Explanation:
Computer Science using JavaScript code form:
Design a cake for your birthday!
Draw a cake on the screen. Ask the user how old they are and then draw that many candles on the cake.
(I am 18 years old so there would be 18 candles below is the image I need to make) (Help ASAP!!!!)
Hints:
Use Constance to control the size of your cake so that if one value changes, the cake is still proportional.
Make sure your candles are added to the cake from the center rather than adding them from left or right.
There are many different ways to decorate your cake, but using loops will make adding lots of decoration much easier!
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that Draw a cake on the screen and Ask the user how old they are and then draw that many candles on the cake.
Writting the code:function birthdayCakeCandles(arr) {
// Step 1
let max = 0;
let counter = 0;
// Step 2 (a)
arr.forEach(item => {
// Step 3
if (item > max) {
// Step 4
max = item;
counter = 1;
// Step 2 (b)
} else if (item === max) {
counter++;
}
});
return counter;
}
See more about JAVA at brainly.com/question/18502436
#SPJ1
Suppose we want to put an array of n integer numbers into descending numerical
order. This task is called sorting. One simple algorithm for sorting is selection sort.
You let an index i go from 0 to n-1, exchanging the ith element of the array with
the maximum element from i up to n. Using this finite set of integers as the input
array {4 3 9 6 1 7 0}:
i. Perform the asymptotic and worst-case analysis on the sorting algorithm
been implemented
Answers
i) Time complexity for worst case is O(n^2).
What is asymptotic?
Asymptotic, informally, refers to a value or curve that is arbitrarily close. The term "asymptote" refers to a line or curve that is asymptotic to a given curve. Let be a continuous variable that tends to some limit, to put it more formally.
1) Asymptotic & worst case analysis:
The worst case analysis occur when the array is sorted in decreasing order.
Time Complexity = O(n^2)
Pseudocode:
for(i=0; i<n-1; i++)
{
int min_index = i;
for (j=i+1;, j<n; j++)
{
if(arr[i]<arr[min_index])
{
min_index = j; }
swap(arr[i],arr[min_index]);
}
}
Let n=6
so,
i =[0,1,2,3,4]
j = [1→5,2→5,3→5,4→5,5→5]
Number of iteration:
5,4,3,2,1
General case:
[tex]\sum^{n-1}_1= 1 + 2 +3 +......+(n-1)[/tex]
[tex]\sum^{n-1}_1= \frac{n(n-1)}{2}[/tex]
[tex]= \frac{n^2-n}{2}[/tex]
So, Time complexity = O(n^2).
∴Time complexity for worst case is O(n^2).
Learn more about asymptotic click here:
https://brainly.com/question/28328185
#SPJ1
List five negative and positive impacts of cybersecurity.
Answers
Utilizing personnel, procedures, technology, and policies to defend enterprises, their vital systems, and sensitive data from online attacks is known as cybersecurity.
What are the negative impact of cybersecurity?Damage to reputation Since the vast majority of people would not do business with a firm that had been infiltrated, especially if it had failed to protect its customers' data, the loss of customer and stakeholder trust can be the most detrimental effect of cybercrime.
Protection for your company - cyber security solutions offer digital defense for your company, ensuring that your staff is safe from potential dangers like ransomware and adware. Increased productivity - infections can cause computers to run so slowly that work becomes nearly impossible.
A better use of time is made possible through productivity apps. Access to biometric gadgets, food management software, and exercise routines easily leads to improved health. communication with friends and family is simpler and less expensive.
To learn more about cybersecurity refer to:
https://brainly.com/question/28004913
#SPJ1
2.12.1: LAB: Name format
This is what I have so far:
name_input = input()
name_separator = name_input.split()
if len(name_separator) == 3:
first_name = name_separator[-3]
middle_name = name_separator[-2]
last_name = name_separator[-1]
first_initial = first_name[0]
middle_initial = middle_name[0]
last_initial = last_name[0]
print(last_name + ", " + first_initial + '.' + middle_initial +'.')
elif len(name_separator) == 2:
first_name = name_separator[-2]
last_name = name_separator [-1]
first_initial = first_name[0]
last_initial = last_name[0]
print(last_name + ", " + first_initial + ".")
Answers
A program that reads a person's name in the following format: first name, middle name, last name is given below:
The Programimport java.util.Scanner;
public class LabProgram {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
String firstName;
String middleName;
String lastName;
String name;
name = scnr.nextLine();
int firstSpace = name.indexOf(" ");
firstName = name.substring(0, firstSpace);
int secondSpace = name.indexOf(" ", firstSpace + 1);
if (secondSpace < 0) {
lastName = name.substring(firstSpace + 1);
System.out.println(lastName + ", " + firstName);
}
else {
middleName = name.substring(firstSpace, secondSpace);
lastName = name.substring(secondSpace + 1);
System.out.println(lastName + ", " + firstName + " " + middleName.charAt(1) + ".");
}
}
}
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1
Olivia is writing a detailed report about nutrition in school lunches. She wants to assure that the text appears professional and that none of the information is lost in the margin. Which option can she adjust to assure that her information is not hidden by the margin?
A: Footer
B: Header
C: Edge
D: Gutter
Answers
She adjust to assure that her information is not hidden by the margin is Gutter.
What is Nutrition?
In terms of nutrition, a balanced diet should be consumed. You can get the nutrition and energy you need from food and drink. Making better food decisions may be made simpler for you if you understand these nutrition terms. Find out more definitions for vitamins, minerals, general health, fitness, and general wellness.
A gutter margin setting enlarges the top or side margins of a document you intend to bind. A gutter margin makes sure that the binding won't cover the text. Note: When using the Mirror margins, 2 pages per sheet, or Book fold options, the Gutter position box is not available.
Open the document or start with a template.
From the, menuFile -> OptionsThis opens the Option window.Select Advanced from the menu an scroll down to DisplayFind the line “Show measurements in units of:” and set it to Centimeters.Learn more about Gutter click here:
https://brainly.in/question/6139979
#SPJ1
For some interest rate i and some number of interest periods n, the uniform series capital recovery factor is 0.1728 and the sinking fund factor is 0.0378. What is the interest rate?
Answers
The Interest Rate, where the Sinking Fund Factor (SFF) is 0.0378, and the Uniform Series Capital Recovery Factor (USCRF) is 21.74%.
What is Sinking Fund Factor?The Sinking Fund Factor (SFF) is a ratio that is used to determine the future worth of a sequence of equal yearly cash flows.
A sinking fund is an account where money is saved to pay off a debt or bond. Sinking money may aid in the repayment of debt at maturity or in the purchase of bonds mostly on the open market. Callable bonds with sinking funds may be recalled back early, depriving the holder of future interest payments.
The interest rate can be calculated by dividing the sinking fund factor by the uniform series capital recovery factor.
The formula for calculating the interest rate is as follows: r = SFF / USCF
Where r = Interest rate;
SFF = 0.0378 (Given) and
USCF = 0.1728 (Given)
Hence,
Interest rate (r) = 0.0378 / 0.1728
= 0.2174 or 21.74%
Therefore, the Interest Rate, where the Sinking Fund Factor (SFF) is 0.0378, and the Uniform Series Capital Recovery Factor (USCRF) amounts to 21.74%.
Learn more about Capital Recovery Factor:
https://brainly.com/question/24297218
#SPJ1
Natalia needs to work on memorizing the keys. What technique will help her the MOST to focus on as she types?
Question 1 options:
focus and concentrate on each key as she presses it
sitting up straight when she starts to slouch
taking a break when her eyes get tired
looking down at the keyboard as she types
Answers
This is the most important technique among all. The correct answer is (option B) because Even information stored in long-term memory becomes difficult to recall if we don’t use it regularly.
What is technique?Therefore, This is the most important technique among all. The correct answer is (option B) because Even information stored in long-term memory becomes difficult to recall if we don’t use it regularly.
Learn more about technique here:
https://brainly.com/question/29775537
#SPJ2
Which answer below correctly identifies two parts
of a function?
1 arguments and executables
2 arguments and statements
3 statements and Python
4 executables and programs
Answers
Answer:
2: arguments and statements
Explanation:
A function does need to be passed arguments, unless it does not take any. And executables are a special type of file that can be executed, eliminate 1.
Eliminate 3, we absolutely do not know that Python is being used here
Eliminate 4, as there are no executables, even though programs are a part of a function.
Which of these vulnerabilities would you find in the device firmware attack surface area?
Inability to wipe device
Buffer Overflow
Interoperability Standards
Security-related function API exposure
Answers
Interoperability Standards, Interoperability is the capacity of devices, programs, systems, or other items from several manufacturers to work in concert without the intervention of end users.
What is Interoperability?
The capacity of various systems, devices, applications, or products to connect and interact in a coordinated manner without needing any help from the end user is known as interoperability (pronounced IHN- tuhr -AHP- uhr -uh-BIHL- ih -tee).Greater timely sharing of important information is made possible by interoperability. The information from a patient's last-week blood test at his doctor's office can therefore be used today at the emergency room, saving time and money from performing additional (and unnecessary) tests at the hospital.Interoperability is the capacity of devices, programs, systems, or other items from several manufacturers to work in concert without the intervention of end users.To learn more about Interoperability refer to:
https://brainly.com/question/2672436
#SPJ1
Why is necessary to have a w-2 or 1099 form when using tax preparation software?
Answers
The reason that it is necessary to have a w-2 or 1099 form when using tax preparation software is that Your employer must report your income tax information to you on a W-2 in accordance with IRS regulations. The form details your annual earnings from that employment, which you can use to determine your adjusted gross income, or AG.
Why is it necessary to use W 2 form?To document payments made to independent contractors, utilize a 1099-MISC (who cover their own employment taxes). On the other hand, employees use a W-2 form (whose employer withholds payroll taxes from their earnings).
Hence, Important details regarding your income from your company, the amount of taxes deducted from your paycheck, perks offered, and other information are displayed on a W-2 tax form. You submit your federal and state taxes using this form.
Learn more about w-2 form from
https://brainly.com/question/1530194
#SPJ1
Implement the primary queue operations using an array of size 3
Answers
It is quite easy to implement the queue data structure using an array. Simply define a one-dimensional array of a certain size, then add or remove the values.
What is an array queue?A queue is a linear data structure where FIFO is used to determine the order of operations (first in first out). The array is a form of data structure that keeps elements of the same type in one continuous area in memory. The insertion and deletion operations in a queue are carried out at its opposing ends.Using the enqueue() function, fresh data can be added to the queue. Dequeue(): Removes the element from the queue with the highest priority. Using the peek()/top() function, you can retrieve the element in the queue with the highest priority without deleting anything else from the queue.It is quite easy to implement the queue data structure using an array. Simply define a one-dimensional array of a certain size, then add or remove the values.To learn more about Array queue refer to:
https://brainly.com/question/27883075
#SPJ1
Help with Linux question--
1. Execute the command ( use symbolic permissions ) that sets the Message.txt permissions, as shown below. Then show the command to display the new file permissions.
Owner: Full control (but be security conscious.)
Group Members: Read-Only
Other: No permissions.
2. Execute the command that sets the Message.txt owner and group to root and A-Team, respectively. Then execute the command to display the new file owner and group.
Answers
The EXECUTE command allows you to run Windows and DOS commands from the Analytics command line or from an Analytics script.
This capability can be used to increase the automation of Analytics scripts by performing a variety of useful tasks that are not possible with ACLScript syntax alone.
How to Execute command in Linux ?The command behaves more or less like a single-line command-line interface. In the Unix-like derivative interface, the run command can be used to run applications by terminal commands.
It can be authorised by pressing Alt+F2. The KDE environment includes the same functionality as KRunner. Similar key binds can be used to authorise it.
The RUN command is used in common programming languages to start programme execution in direct mode or to start an overlay programme via the loader programme.
Beginning with Windows 95, the run command is accessible via the Start menu and the shortcut key Win+R. The command, however, is still available in Windows Vista. It no longer appears directly over the start menu by default, in favour of the newer search box and the shortcut to a run command inside the Windows System sub-menu.
In Linux, create a new file called demo.sh with a text editor such as nano or vi.In Linux, create a new file called demo.sh with a text editor such as nano or vi.Execute a shell script in Linux.To learn more about command refer :
https://brainly.com/question/4068597
#SPJ1